- Business Essentials
- Leadership & Management
- Credential of Leadership, Impact, and Management in Business (CLIMB)
- Entrepreneurship & Innovation
- Digital Transformation
- Finance & Accounting
- Business in Society
- For Organizations
- Support Portal
- Media Coverage
- Founding Donors
- Leadership Team

- Harvard Business School →
- HBS Online →
- Business Insights →

Business Insights
Harvard Business School Online's Business Insights Blog provides the career insights you need to achieve your goals and gain confidence in your business skills.
- Career Development
- Communication
- Decision-Making
- Earning Your MBA
- Negotiation
- News & Events
- Productivity
- Staff Spotlight
- Student Profiles
- Work-Life Balance
- AI Essentials for Business
- Alternative Investments
- Business Analytics
- Business Strategy
- Business and Climate Change
- Creating Brand Value
- Design Thinking and Innovation
- Digital Marketing Strategy
- Disruptive Strategy
- Economics for Managers
- Entrepreneurship Essentials
- Financial Accounting
- Global Business
- Launching Tech Ventures
- Leadership Principles
- Leadership, Ethics, and Corporate Accountability
- Leading Change and Organizational Renewal
- Leading with Finance
- Management Essentials
- Negotiation Mastery
- Organizational Leadership
- Power and Influence for Positive Impact
- Strategy Execution
- Sustainable Business Strategy
- Sustainable Investing
- Winning with Digital Platforms
What Is Risk Management & Why Is It Important?

- 24 Oct 2023
Businesses can’t operate without risk. Economic, technological, environmental, and competitive factors introduce obstacles that companies must not only manage but overcome.
According to PwC’s Global Risk Survey , organizations that embrace strategic risk management are five times more likely to deliver stakeholder confidence and better business outcomes and two times more likely to expect faster revenue growth.
If you want to enhance your job performance and identify and mitigate risk more effectively, here’s a breakdown of what risk management is and why it’s important.
Access your free e-book today.
What Is Risk Management?
Risk management is the systematic process of identifying, assessing, and mitigating threats or uncertainties that can affect your organization. It involves analyzing risks’ likelihood and impact, developing strategies to minimize harm, and monitoring measures’ effectiveness.
“Competing successfully in any industry involves some level of risk,” says Harvard Business School Professor Robert Simons, who teaches the online course Strategy Execution . “But high-performing businesses with high-pressure cultures are especially vulnerable. As a manager, you need to know how and why these risks arise and how to avoid them.”
According to Strategy Execution , strategic risk has three main causes:
- Pressures due to growth: This is often caused by an accelerated rate of expansion that makes staffing or industry knowledge gaps more harmful to your business.
- Pressures due to culture: While entrepreneurial risk-taking can come with rewards, executive resistance and internal competition can cause problems.
- Pressures due to information management: Since information is key to effective leadership , gaps in performance measures can result in decentralized decision-making.
These pressures can lead to several types of risk that you must manage or mitigate to avoid reputational, financial, or strategic failures. However, risks aren’t always obvious.
“I think one of the challenges firms face is the ability to properly identify their risks,” says HBS Professor Eugene Soltes in Strategy Execution .
Therefore, it’s crucial to pinpoint unexpected events or conditions that could significantly impede your organization’s business strategy .
Related: Business Strategy vs. Strategy Execution: Which Course Is Right for Me?
According to Strategy Execution , strategic risk comprises:
- Operations risk: This occurs when internal operational errors interrupt your products or services’ flow. For example, shipping tainted products can negatively affect food distribution companies.
- Asset impairment risk: When your company’s assets lose a significant portion of their current value because of a decreased likelihood of receiving future cash flows . For instance, losing property assets, like a manufacturing plant, due to a natural disaster.
- Competitive risk: Changes in the competitive environment can interrupt your organization’s ability to create value and differentiate its offerings—eventually leading to a significant loss in revenue.
- Franchise risk: When your organization’s value erodes because stakeholders lose confidence in its objectives. This primarily results from failing to control any of the strategic risk sources listed above.
Understanding these risks is essential to ensuring your organization’s long-term success. Here’s a deeper dive into why risk management is important.
4 Reasons Why Risk Management Is Important
1. protects organization’s reputation.
In many cases, effective risk management proactively protects your organization from incidents that can affect its reputation.
“Franchise risk is a concern for all businesses,“ Simons says in Strategy Execution . “However, it's especially pressing for businesses whose reputations depend on the trust of key constituents.”
For example, airlines are particularly susceptible to franchise risk because of unforeseen events, such as flight delays and cancellations caused by weather or mechanical failure. While such incidents are considered operational risks, they can be incredibly damaging.
In 2016, Delta Airlines experienced a national computer outage, resulting in over 2,000 flight cancellations. Delta not only lost an estimated $150 million but took a hit to its reputation as a reliable airline that prided itself on “canceling cancellations.”
While Delta bounced back, the incident illustrates how mitigating operational errors can make or break your organization.
2. Minimizes Losses
Most businesses create risk management teams to avoid major financial losses. Yet, various risks can still impact their bottom lines.
A Vault Platform study found that dealing with workplace misconduct cost U.S. businesses over $20 billion in 2021. In addition, Soltes says in Strategy Execution that corporate fines for misconduct have risen 40-fold in the U.S. over the last 20 years.
One way to mitigate financial losses related to employee misconduct is by implementing internal controls. According to Strategy Execution , internal controls are the policies and procedures designed to ensure reliable accounting information and safeguard company assets.
“Managers use internal controls to limit the opportunities employees have to expose the business to risk,” Simons says in the course.
One company that could have benefited from implementing internal controls is Volkswagen (VW). In 2015, VW whistle-blowers revealed that the company’s engineers deliberately manipulated diesel vehicles’ emissions data to make them appear more environmentally friendly.
This led to severe consequences, including regulatory penalties, expensive vehicle recalls, and legal settlements—all of which resulted in significant financial losses. By 2018, U.S. authorities had extracted $25 billion in fines, penalties, civil damages, and restitution from the company.
Had VW maintained more rigorous internal controls to ensure transparency, compliance, and proper oversight of its engineering practices, perhaps it could have detected—or even averted—the situation.
Related: What Are Business Ethics & Why Are They Important?
3. Encourages Innovation and Growth
Risk management isn’t just about avoiding negative outcomes. It can also be the catalyst that drives your organization’s innovation and growth.
“Risks may not be pleasant to think about, but they’re inevitable if you want to push your business to innovate and remain competitive,” Simons says in Strategy Execution .
According to PwC , 83 percent of companies’ business strategies focus on growth, despite risks and mixed economic signals. In Strategy Execution , Simons notes that competitive risk is a challenge you must constantly monitor and address.
“Any firm operating in a competitive market must focus its attention on changes in the external environment that could impair its ability to create value for its customers,” Simons says.
This requires incorporating boundary systems —explicit statements that define and communicate risks to avoid—to ensure internal controls don’t extinguish innovation.
“Boundary systems are essential levers in businesses to give people freedom,” Simons says. “In such circumstances, you don’t want to stifle innovation or entrepreneurial behavior by telling people how to do their jobs. And if you want to remain competitive, you’ll need to innovate and adapt.”

Netflix is an example of how risk management can inspire innovation. In the early 2000s, the company was primarily known for its DVD-by-mail rental service. With growing competition from video rental stores, Netflix went against the grain and introduced its streaming service. This changed the market, resulting in a booming industry nearly a decade later.
Netflix’s innovation didn’t stop there. Once the steaming services market became highly competitive, the company shifted once again to gain a competitive edge. It ventured into producing original content, which ultimately helped differentiate its platform and attract additional subscribers.
By offering more freedom within internal controls, you can encourage innovation and constant growth.
4. Enhances Decision-Making
Risk management also provides a structured framework for decision-making. This can be beneficial if your business is inclined toward risks that are difficult to manage.
By pulling data from existing control systems to develop hypothetical scenarios, you can discuss and debate strategies’ efficacy before executing them.
“Interactive control systems are the formal information systems managers use to personally involve themselves in the decision activities of subordinates,” Simons says in Strategy Execution . “Decision activities that relate to and impact strategic uncertainties.”
JPMorgan Chase, one of the most prominent financial institutions in the world, is particularly susceptible to cyber risks because it compiles vast amounts of sensitive customer data . According to PwC , cybersecurity is the number one business risk on managers’ minds, with 78 percent worried about more frequent or broader cyber attacks.
Using data science techniques like machine learning algorithms enables JPMorgan Chase’s leadership not only to detect and prevent cyber attacks but address and mitigate risk.

Start Managing Your Organization's Risk
Risk management is essential to business. While some risk is inevitable, your ability to identify and mitigate it can benefit your organization.
But you can’t plan for everything. According to the Harvard Business Review , some risks are so remote that no one could have imagined them. Some result from a perfect storm of incidents, while others materialize rapidly and on enormous scales.
By taking an online strategy course , you can build the knowledge and skills to identify strategic risks and ensure they don’t undermine your business. For example, through an interactive learning experience, Strategy Execution enables you to draw insights from real-world business examples and better understand how to approach risk management.
Do you want to mitigate your organization’s risks? Explore Strategy Execution —one of our online strategy courses —and download our free strategy e-book to gain the insights to build a successful strategy.

About the Author
Home — Essay Samples — Business — Risk Management — The Importance of Risk Management
The Importance of Risk Management
- Categories: Risk Management
About this sample

Words: 549 |
Published: Sep 1, 2023
Words: 549 | Page: 1 | 3 min read

Cite this Essay
To export a reference to this article please select a referencing style below:
Let us write you an essay from scratch
- 450+ experts on 30 subjects ready to help
- Custom essay delivered in as few as 3 hours
Get high-quality help

Verified writer
- Expert in: Business

+ 120 experts online
By clicking “Check Writers’ Offers”, you agree to our terms of service and privacy policy . We’ll occasionally send you promo and account related email
No need to pay just yet!
Related Essays
1 pages / 413 words
2 pages / 868 words
1 pages / 416 words
3 pages / 1419 words
Remember! This is just a sample.
You can get your custom paper by one of our expert writers.
121 writers online
Still can’t find what you need?
Browse our vast selection of original essay samples, each expertly formatted and styled
Related Essays on Risk Management
Khan, Mohammad, Robert Breitenecker, and Erich Schwarz. “Adding fuel to the fire.” Management Decision 53.1 (2015): 75-99. Print. Kurlick, Gary. “Stop, drop, and roll: workplace hazards of local government firefighters.” [...]
Deepwater Disaster Plan Failure Risk management failures were a core factor leading to one of the largest oil well disaster in the Gulf of Mexico, US. The Deepwater explosion, in May 2010, killed 11 men and left miles of [...]
The COSO cube helps us look at the whole organizations enterprise risk management model and focus on individual parts. Enterprise risk management (ERM) is the process of planning, organizing, leading and controlling the [...]
Risk management procedures facilitate the protection of a company’s reputation as the company’s involved often concentrate on ethical procedures when assessing and creating awareness on the potential risks in the company (Hopkin [...]
According to the USA state law, critical structures are mainly defined as any asset, system of resource that is of indispensable importance to the welfare and well-being of the country. The destruction of these critical [...]
Amongst many dilemmas that we face today, although communication is easier than ever, yet it is being increasingly difficult for us to maintain conversations face to face. Interaction is becoming increasingly digitalized, where [...]
Related Topics
By clicking “Send”, you agree to our Terms of service and Privacy statement . We will occasionally send you account related emails.
Where do you want us to send this sample?
By clicking “Continue”, you agree to our terms of service and privacy policy.
Be careful. This essay is not unique
This essay was donated by a student and is likely to have been used and submitted before
Download this Sample
Free samples may contain mistakes and not unique parts
Sorry, we could not paraphrase this essay. Our professional writers can rewrite it and get you a unique paper.
Please check your inbox.
We can write you a custom essay that will follow your exact instructions and meet the deadlines. Let's fix your grades together!
Get Your Personalized Essay in 3 Hours or Less!
We use cookies to personalyze your web-site experience. By continuing we’ll assume you board with our cookie policy .
- Instructions Followed To The Letter
- Deadlines Met At Every Stage
- Unique And Plagiarism Free
Risk Management - Free Essay Examples And Topic Ideas
Risk management involves identifying, assessing, and controlling threats to an organization’s capital and earnings. These threats could stem from a wide variety of sources, including financial uncertainty, legal liabilities, strategic management errors, accidents, and natural disasters. An essay on risk management might cover strategies to mitigate risks, the impact of risk management on business performance, and the evolution of risk management practices over time. This topic might also touch on various risk assessment models, the ethical aspects of risk management, and case studies illustrating the consequences of inadequate risk management. We have collected a large number of free essay examples about Risk Management you can find in Papersowl database. You can use our samples for inspiration to write your own essay, research paper, or just to explore a new topic for yourself.
Risk Management in Nursing Practice
Bowers (2014) identifies the need for the preservation of safety as the most crucial objective for mental health nursing. However, this is a very isolative environment with seclusion being a part of this treatment and intervention. Clifton et al (2017) argues that this could lead to possible deterioration of social inclusion, independence and communication. Shared decision-making (SDM) is a frequently utilized model for the purpose of approaching sensitive decisions (Stiggelbout et al, 2015). This process is where clinicians and patients […]
Risk Management of Innovation Projects
Abstract A company’s ability to create new products and services that differentiate them from the competition is becoming a key factor to ensure a business’ longevity in this ever-growing market. Because of this, organizations have continuously tried to launch innovation projects that ultimately fail in most cases due to the higher than normal levels of risk and uncertainty associated with these types of ventures. The purpose of this paper is to review and analyze the characteristics of radical innovation projects […]
Discuss the Importance of Data Management in Research
1. Definiton of Key terms Data management is a general term which refers to a part of research process involving organising, structuring, storage and care of data generated during the research process. It is of prime importance in that it is part of good research practice and it has a bearing on the quality of analysis and research output. The University of Edinburgh (2014) defines data management as a general term covering how you organize, structure, store and care for […]
We will write an essay sample crafted to your needs.
What is Risk Management?
A risk is any unverifiable event or condition that may influence our task(project). Not all dangers are negative. A few occasions or conditions can encourage our task. At the point when this occurs, we consider it a chance; however it's as yet dealt with simply like a hazard. A proactive task group attempts to determine potential issues previously they happen. This is the craft of hazard administration. The motivation behind hazard administration is to recognize the hazard factors for a […]
Effective Risk Management
Uncertainty bounds today's economy, and every organization needs a structured process for effective risk management to sustain a competitive edge (K. J., A., V. R., and U., 2017). Numerous corporate governance regulations, like the SOX Act 2002, COSO Enterprise Risk Management Framework 2004, Companies Act 2013, and Clause 49 of SEBI, have made the existence of a risk management committee mandatory. A risk management committee, a person, or a group of persons, is required at the top management level for […]
Citizen and Government Collaboration in Addressing Natural Disasters in Japan
Natural hazards are indeed inevitable, even during this time of pandemic. A massive 7.3 magnitude earthquake has jolted the northeastern coast of Japan, leaving 150 injured people last February 13, 2021. It’s considered an aftershock of the 2011 Great East Japan Earthquake because it happened just weeks before its 10th anniversary. The 7.3 magnitude earthquake caused widespread blackouts, affecting 950,000 households, and displaced around 240 people in Miyagi and Fukushima prefectures from their homes. The Japanese Intensity Scale logged it […]
Futuram’s Risk Management Strategy
Read the following story about this agricultural biotech firm carefully, then answer the questions at the end of the case. This story, all names, characters, and incidents described are fictitious. No identification with actual persons, companies, places, or products is intended or should be inferred. Normally, when Futuram is mentioned in newspapers, it's usually for a new genetically engineered seed. Yet this agricultural biotech firm, based in California, has turned to financial engineering to ensure its profits. At its January 2017 […]
IT Risk Management Techniques
Introduction In life, only two things are true about failure. One, it is common and second, nobody likes them. Failure is something that cannot be completely avoided but it is not absolute as well. Past failures become better lessons on which such failures doesn’t occur in the future. Modifications and changes made due to failures signal positive changes in the entity and scopes for improvement. The only irony in this case is that each failure comes at a certain cost. […]
Risk Policy, Management and Communication
I would like to thank the Municipal Administration and Water Supplies Department, State Government of Tamil Nadu, India for inviting me to speak about the current scenario and to give my recommendations for making P.N.Palayam a model town with regard to Sanitation. I am Priscilla, an Environmental Scientist, representing Bill and Melinda Gates Foundation, India. I have done my master’s in environmental science in 1996 and completed my Doctoral degree in Environmental Health at Johns Hopkins Bloomberg School of Public […]
Disaster Risk Management
"Disasters can happen to anyone at any time, but research says even the best disaster-recovery plans will not work exactly as envisioned (Drew & Tysiac, 2013). Huge amounts of destruction and suffering can lead to mental health and other issues for employees. This is why organizations should focus on their people's needs. Firms in the state of Florida and other natural disaster areas are well-advised to have business interruption insurance, which is structured to compensate businesses for time-frames when they […]
Effective Teamwork: Risk Management
Risk is the presence of uncertainty of results regarding present actions ( Shastri and Shastri, 2014 ). Risk arises due to occurrence of chance events, incubating and culminating in the changing dynamics of the environment. All functional areas of an organization are affected by risk. A single event can unleash a variety of risks. Risk is omnipresent, omnipotent and omniscient. Risk management is a process effected by the entity’s board of directors, management and other personnel, applied in strategy setting […]
Hazard Management in Foreign Exchange
Back Back is a term portraying the investigation and arrangement of cash, ventures, and other money related instruments. A few people want to isolate back into three unmistakable classifications: open fund, corporate fund, and individual fund. There is additionally the as of late rising region of social back. Conduct fund tries to distinguish the intellectual (e.g. enthusiastic, social, and mental) explanations for money related choices. Outside Exchange Outside trade is the transformation of one nation's money into another. In a […]
Impact of Natural Disasters on Risk Management
Research says threats of natural disasters may continue to rise due to the increase in the average temperature of the water in oceans (Tennyson & Diala, 2016). Weather events will be intense and frequent due to global warming. This will result in rising sea levels and other environmental changes. According to Tennyson and Diala, disaster preparedness is the total of all measures that have been taken and the policies that have been adopted to address a disaster before it occurs […]
Risk Management in Online Transactions
Abstract There has been a significant increase in the number of online transactions on various platforms. Online transactions are boosting the global economy by offering convenience and speed of the money transactions between merchants and customers. For online transactions to be successful, there is a need to have a reliable network that is enhanced by a security system to safeguard the information of the transactions. The networks used to secure online transactions are not entirely effective hence there is need […]
Risk Management in a Banking System
A risk is an essential part of our daily lives. Despite the complexity of this concept, we often and easily operate it in practice, describing a particular life situation. For us, a risk is primarily a possible profit or loss of something. Commercial activities, as well as any other activities related to the formulation and achievement of certain goals, include: situation analysis; strategy formulation; resource planning; organization of a process; measurement and evaluation of results; operational corrective strategic and tactical actions […]
Risk Management – Essential and Complete Corporate Governance System
Risk management is a known element of an essential and complete corporate governance system. It is defined as a mix of activities that effectively reduce the negative impact of risk exposure on the company's projected profits, cash flow, and consequently, the value of the organization. Effective risk management is regarded as an important factor that determines the survival and success of an organization. While risk management is not a new concept, it has recently garnered attention and become moreassertive in […]
Identifying and Managing Business Risks
Introduction A risk is a probability that something with an undesirable effect will occur. Risk management involves steps and policies taken by a company to eliminate these risks or reduce the possibility of their occurrence. A risk management plan is prepared to predict the risks, estimate their impact and severity, and suggest possible responses. Health Network allows clients to access the kind of healthcare services they require over the internet at the right locations. It faces several risks that can […]
The Effects Automation Technology has on Risk Management
Automation technology is the system of controlling a process by highly automatic means, resulting in reduced human intervention. This technology was created to relieve operators from continuous input. Automation benefits users by increasing safety, profitability, and productivity. By the use of machinery products are more predictable, consistent, and the cycle time of production is shorter than it would be if done by man. Though the idea of automatic technology seems fool proof there are disadvantages to it as well. Since […]
Risk Management Techniques for Satellite Programs
Successfully placing a satellite into space requires many elements of a very complicated process coming together, to allow for an on-schedule launch, and nominal operations of the system once on-orbit. Modern day government organizations and private sector companies have become adept at this process, as space launches occur with regularity all over the world. Despite the high success rates seen in the launch and operation of modern satellite systems, risk still pervades these programs, from writing requirements to the ready-for-launch' […]
Enterprise Risk Management Project
Coca-Cola Bottling Company Consolidated was formed 116 years ago in Greensboro North Carolina. Here they started to begin to produce and deliver an ironic brand there. It was all started by J.B. Harrison where he started selling the bottles. In 1955 they started to make 10,12, and 26 ounce family size and king sized bottles. In 1982 they first introduced the idea of Diet Coke. Also, in 2002 they celebrated their 100 year of business. Currently, the company's corporate offices […]
Assessment Credit Risk Management
Credit risk management practices is an issue of concern in financial institutions today and there is needto develop improved processes and systems to deliver better visibility into future performance. There have been controversies among researchers on the effect of credit management techniques adopted by various institutions. According to Saunders and Allen (2002), good selection strategy for risk monitoring is adopted by the credit unions implies good pricing of the products in line with the estimated risk which greatly affect their […]
Issue, Risk and Reputation Management
The proactive behavior, commonly associated with the initiative, creativity, and innovation, is required in today's organizations. It can be a positive differential in times of market turmoil and uncertainty. According to Coombs, the best way to prevent a crisis in an organization is to have a proactive management. Proactive behavior is an element of change and it impacts the company's performance. A proactive management seeks deliberately for changes and improvements, it anticipates the problems and chooses its own course to […]
Risk Management: Role in Security and Establishes the Importance of Assets Within a Company
According to the Principles of Information Security, "risk management is the process of identifying risk, assessing its relative magnitude, and taking steps to reduce it to an acceptable level." Risk management plays an important role in security and establishes the importance of assets within a company. Financial and economic decisions made by a company are heavily influenced by the way risk management is handled. There are many important aspects to risk management, such as: risk identification, risk assessment, and risk […]
Risk Management Section of your Company’s
Read the Risk Management section of your company's 10-K. Do not print the 10-K. In your own words, summarize the risk management strategy. Tie this into the Risk Factors that you wrote in Project 1. Netflix's risk management strategy includes the following: Retaining and expanding its customer base: Subscription fees are the major revenue source for Netflix. Its ability to produce and acquire quality content depends directly on retaining its current customers and attracting new ones. If Netflix cannot satisfy […]
Essay about Risk Management Techniques for Satellite Programs
Either way, this helps to burn down the consequence of only have a sole dedicated relay through redundancy. Another aspect a program manager should consider when assessing risk with ground relays points to the operations crews that run them. An example of a human error causing a space disaster is showcased in the 2009 collision of an Iridium Communications satellite and a defunct Russian communications satellite. With the Russian satellite out of commission, it rested on the Iridium satellite to maneuver […]
Risk Management and Insurance
As people, we are faced with the possibility of loss in our everyday lives. Be it a car accident, illness, Property loss, or even death. As early as the millennia B.C, modern profit insurance was demonstrated in a contract of a loan of trading capital to traveling merchants. The first insurance company formed in the United States was in Charleston, South Carolina during 1732. Later in 1752, Benjamin Franklin helped spread insurance by creating the Philadelphia Contributionship which ensured that […]
Facilities Management
Introduction In any big gathering, crowd control is essential. Sports facilities are protected through crowd control since, where there are many people gathered together there is a high chance for a danger to take place. Secondly, the crowd needs to be managed because when people are in a crowd they always take for granted that other people have the responsibility (Ammon & Unruh 2010). Thirdly, big gathering makes people assimilate changes at a lower phase since they make the process […]
Health Data Breach Response Plan: a Managed Care Organization’s Comprehensive Plan
Response plan on health data breach Introduction Security imperatives of preventing, responding to, and detecting breaches will finally end with good reason and appropriate rejoinder criteria implemented. Breaches in various companies have become inevitable despite efforts put in place to prevent their continuous occurrence. Once there is an unauthorized disclosure, compromise of protected data, or hacking of information that is protected, an organization is obliged to respond. Putting an effective response plan in place is not a small feat. Organization's […]
Network Infrastructure: Analyzing NT1310 Unit 6 Assignment
Introduction The study of network infrastructure is super important for getting how modern digital communication works. NT1310 Unit 6 Assignment dives into the nitty-gritty of network design, setup, and management, giving students a complete look at what makes connectivity tick. This essay wants to break down the main parts of the assignment, including its goals, methods, and what it means for network pros. We'll look at both the theory and the practical side of network infrastructure, making sure the analysis […]
The Confluence of AAA4 Insurance and Virtual Reality Innovation
In today's fast-paced world, insurance remains a bedrock of financial security, shielding individuals from the uncertainties that life often throws our way. Among the plethora of insurance products, AAA4 insurance is notable for its specialized coverage options tailored to unique needs. When we merge the concept of AAA4 insurance with the burgeoning field of virtual reality (VR), an intriguing narrative unfolds, highlighting the transformative potential and unforeseen synergies between these two domains. AAA4 insurance is characterized by its bespoke coverage, […]
Additional Example Essays
- Reasons Why I Want to Study Abroad
- "Mother to Son" by Langston Hughes
- The Cask of Amontillado Literary Analysis
- A Class Divided
- “Allegory of the Cave”
- Cinderella Marxism
- Rhetorical Analysis of Steve Jobs’ Commencement Address
- The Girl (Jig) Character Analysis in Hills Like White Elephants
- Dental Hygiene Application Essay
- Their Eyes Were Watching God Literary Analysis
- Things Fall Apart: Character Analysis Okonkwo
- Symbolism in Nathaniel Hawthrone’s “Young Goodman Brown”
1. Tell Us Your Requirements
2. Pick your perfect writer
3. Get Your Paper and Pay
Hi! I'm Amy, your personal assistant!
Don't know where to start? Give me your paper requirements and I connect you to an academic expert.
short deadlines
100% Plagiarism-Free
Certified writers
Enterprise Risk Management: A Literature Review and Agenda for Future Research
- November 2020
- Journal of Risk and Financial Management 13(11):281

- Universitatea Alexandru Ioan Cuza

Abstract and Figures

Discover the world's research
- 25+ million members
- 160+ million publication pages
- 2.3+ billion citations
- Siti Aminah Ahmad
- Poh-Chuin Teo
- Nataliya Skopenko
- Iryna Fedulova
- Tetiana Mostenska
- Larysa Kapinus
- Abhulimen Adedeji Adeniran
- Obiki-Osafiele

- Wasim ULLAH
- Ahmad Shauqi Mohamad Zubir
- Akmalia M. Ariff
- Soha Mamdouuh Elkhouly
- Elsayeda Said Elwakeil
- Basma Abdelmogy Ismail
- Manag Finance

- Sorabh Lakhanpal
- Rishabh Jain
- Maxwell Nana Ameyaw
- Courage Idemudia
- Toluwalase Vanessa Iyelolu

- Pablo Durán Santomil
- Aracely Tamayo Herrera

- ANN OPER RES

- Thomas R. Berry-Stölzle

- Weerawan Siripong
- On-anong Sattayarak
- Sutira Limroscharoen
- J Model Manag

- Fazeeda Mohamad

- Ilies Bensaada

- J Risk Finance

- Recruit researchers
- Join for free
- Login Email Tip: Most researchers use their institutional email address as their ResearchGate login Password Forgot password? Keep me logged in Log in or Continue with Google Welcome back! Please log in. Email · Hint Tip: Most researchers use their institutional email address as their ResearchGate login Password Forgot password? Keep me logged in Log in or Continue with Google No account? Sign up
- Search Menu
Sign in through your institution
- Browse content in Arts and Humanities
- Browse content in Archaeology
- Anglo-Saxon and Medieval Archaeology
- Archaeological Methodology and Techniques
- Archaeology by Region
- Archaeology of Religion
- Archaeology of Trade and Exchange
- Biblical Archaeology
- Contemporary and Public Archaeology
- Environmental Archaeology
- Historical Archaeology
- History and Theory of Archaeology
- Industrial Archaeology
- Landscape Archaeology
- Mortuary Archaeology
- Prehistoric Archaeology
- Underwater Archaeology
- Urban Archaeology
- Zooarchaeology
- Browse content in Architecture
- Architectural Structure and Design
- History of Architecture
- Residential and Domestic Buildings
- Theory of Architecture
- Browse content in Art
- Art Subjects and Themes
- History of Art
- Industrial and Commercial Art
- Theory of Art
- Biographical Studies
- Byzantine Studies
- Browse content in Classical Studies
- Classical History
- Classical Philosophy
- Classical Mythology
- Classical Numismatics
- Classical Literature
- Classical Reception
- Classical Art and Architecture
- Classical Oratory and Rhetoric
- Greek and Roman Papyrology
- Greek and Roman Epigraphy
- Greek and Roman Law
- Greek and Roman Archaeology
- Late Antiquity
- Religion in the Ancient World
- Social History
- Digital Humanities
- Browse content in History
- Colonialism and Imperialism
- Diplomatic History
- Environmental History
- Genealogy, Heraldry, Names, and Honours
- Genocide and Ethnic Cleansing
- Historical Geography
- History by Period
- History of Emotions
- History of Agriculture
- History of Education
- History of Gender and Sexuality
- Industrial History
- Intellectual History
- International History
- Labour History
- Legal and Constitutional History
- Local and Family History
- Maritime History
- Military History
- National Liberation and Post-Colonialism
- Oral History
- Political History
- Public History
- Regional and National History
- Revolutions and Rebellions
- Slavery and Abolition of Slavery
- Social and Cultural History
- Theory, Methods, and Historiography
- Urban History
- World History
- Browse content in Language Teaching and Learning
- Language Learning (Specific Skills)
- Language Teaching Theory and Methods
- Browse content in Linguistics
- Applied Linguistics
- Cognitive Linguistics
- Computational Linguistics
- Forensic Linguistics
- Grammar, Syntax and Morphology
- Historical and Diachronic Linguistics
- History of English
- Language Evolution
- Language Reference
- Language Acquisition
- Language Variation
- Language Families
- Lexicography
- Linguistic Anthropology
- Linguistic Theories
- Linguistic Typology
- Phonetics and Phonology
- Psycholinguistics
- Sociolinguistics
- Translation and Interpretation
- Writing Systems
- Browse content in Literature
- Bibliography
- Children's Literature Studies
- Literary Studies (Romanticism)
- Literary Studies (American)
- Literary Studies (Asian)
- Literary Studies (European)
- Literary Studies (Eco-criticism)
- Literary Studies (Modernism)
- Literary Studies - World
- Literary Studies (1500 to 1800)
- Literary Studies (19th Century)
- Literary Studies (20th Century onwards)
- Literary Studies (African American Literature)
- Literary Studies (British and Irish)
- Literary Studies (Early and Medieval)
- Literary Studies (Fiction, Novelists, and Prose Writers)
- Literary Studies (Gender Studies)
- Literary Studies (Graphic Novels)
- Literary Studies (History of the Book)
- Literary Studies (Plays and Playwrights)
- Literary Studies (Poetry and Poets)
- Literary Studies (Postcolonial Literature)
- Literary Studies (Queer Studies)
- Literary Studies (Science Fiction)
- Literary Studies (Travel Literature)
- Literary Studies (War Literature)
- Literary Studies (Women's Writing)
- Literary Theory and Cultural Studies
- Mythology and Folklore
- Shakespeare Studies and Criticism
- Browse content in Media Studies
- Browse content in Music
- Applied Music
- Dance and Music
- Ethics in Music
- Ethnomusicology
- Gender and Sexuality in Music
- Medicine and Music
- Music Cultures
- Music and Media
- Music and Religion
- Music and Culture
- Music Education and Pedagogy
- Music Theory and Analysis
- Musical Scores, Lyrics, and Libretti
- Musical Structures, Styles, and Techniques
- Musicology and Music History
- Performance Practice and Studies
- Race and Ethnicity in Music
- Sound Studies
- Browse content in Performing Arts
- Browse content in Philosophy
- Aesthetics and Philosophy of Art
- Epistemology
- Feminist Philosophy
- History of Western Philosophy
- Meta-Philosophy
- Metaphysics
- Moral Philosophy
- Non-Western Philosophy
- Philosophy of Language
- Philosophy of Mind
- Philosophy of Perception
- Philosophy of Science
- Philosophy of Action
- Philosophy of Law
- Philosophy of Religion
- Philosophy of Mathematics and Logic
- Practical Ethics
- Social and Political Philosophy
- Browse content in Religion
- Biblical Studies
- Christianity
- East Asian Religions
- History of Religion
- Judaism and Jewish Studies
- Qumran Studies
- Religion and Education
- Religion and Health
- Religion and Politics
- Religion and Science
- Religion and Law
- Religion and Art, Literature, and Music
- Religious Studies
- Browse content in Society and Culture
- Cookery, Food, and Drink
- Cultural Studies
- Customs and Traditions
- Ethical Issues and Debates
- Hobbies, Games, Arts and Crafts
- Natural world, Country Life, and Pets
- Popular Beliefs and Controversial Knowledge
- Sports and Outdoor Recreation
- Technology and Society
- Travel and Holiday
- Visual Culture
- Browse content in Law
- Arbitration
- Browse content in Company and Commercial Law
- Commercial Law
- Company Law
- Browse content in Comparative Law
- Systems of Law
- Competition Law
- Browse content in Constitutional and Administrative Law
- Government Powers
- Judicial Review
- Local Government Law
- Military and Defence Law
- Parliamentary and Legislative Practice
- Construction Law
- Contract Law
- Browse content in Criminal Law
- Criminal Procedure
- Criminal Evidence Law
- Sentencing and Punishment
- Employment and Labour Law
- Environment and Energy Law
- Browse content in Financial Law
- Banking Law
- Insolvency Law
- History of Law
- Human Rights and Immigration
- Intellectual Property Law
- Browse content in International Law
- Private International Law and Conflict of Laws
- Public International Law
- IT and Communications Law
- Jurisprudence and Philosophy of Law
- Law and Politics
- Law and Society
- Browse content in Legal System and Practice
- Courts and Procedure
- Legal Skills and Practice
- Legal System - Costs and Funding
- Primary Sources of Law
- Regulation of Legal Profession
- Medical and Healthcare Law
- Browse content in Policing
- Criminal Investigation and Detection
- Police and Security Services
- Police Procedure and Law
- Police Regional Planning
- Browse content in Property Law
- Personal Property Law
- Restitution
- Study and Revision
- Terrorism and National Security Law
- Browse content in Trusts Law
- Wills and Probate or Succession
- Browse content in Medicine and Health
- Browse content in Allied Health Professions
- Arts Therapies
- Clinical Science
- Dietetics and Nutrition
- Occupational Therapy
- Operating Department Practice
- Physiotherapy
- Radiography
- Speech and Language Therapy
- Browse content in Anaesthetics
- General Anaesthesia
- Clinical Neuroscience
- Browse content in Clinical Medicine
- Acute Medicine
- Cardiovascular Medicine
- Clinical Genetics
- Clinical Pharmacology and Therapeutics
- Dermatology
- Endocrinology and Diabetes
- Gastroenterology
- Genito-urinary Medicine
- Geriatric Medicine
- Infectious Diseases
- Medical Toxicology
- Medical Oncology
- Pain Medicine
- Palliative Medicine
- Rehabilitation Medicine
- Respiratory Medicine and Pulmonology
- Rheumatology
- Sleep Medicine
- Sports and Exercise Medicine
- Community Medical Services
- Critical Care
- Emergency Medicine
- Forensic Medicine
- Haematology
- History of Medicine
- Browse content in Medical Skills
- Clinical Skills
- Communication Skills
- Nursing Skills
- Surgical Skills
- Browse content in Medical Dentistry
- Oral and Maxillofacial Surgery
- Paediatric Dentistry
- Restorative Dentistry and Orthodontics
- Surgical Dentistry
- Medical Ethics
- Medical Statistics and Methodology
- Browse content in Neurology
- Clinical Neurophysiology
- Neuropathology
- Nursing Studies
- Browse content in Obstetrics and Gynaecology
- Gynaecology
- Occupational Medicine
- Ophthalmology
- Otolaryngology (ENT)
- Browse content in Paediatrics
- Neonatology
- Browse content in Pathology
- Chemical Pathology
- Clinical Cytogenetics and Molecular Genetics
- Histopathology
- Medical Microbiology and Virology
- Patient Education and Information
- Browse content in Pharmacology
- Psychopharmacology
- Browse content in Popular Health
- Caring for Others
- Complementary and Alternative Medicine
- Self-help and Personal Development
- Browse content in Preclinical Medicine
- Cell Biology
- Molecular Biology and Genetics
- Reproduction, Growth and Development
- Primary Care
- Professional Development in Medicine
- Browse content in Psychiatry
- Addiction Medicine
- Child and Adolescent Psychiatry
- Forensic Psychiatry
- Learning Disabilities
- Old Age Psychiatry
- Psychotherapy
- Browse content in Public Health and Epidemiology
- Epidemiology
- Public Health
- Browse content in Radiology
- Clinical Radiology
- Interventional Radiology
- Nuclear Medicine
- Radiation Oncology
- Reproductive Medicine
- Browse content in Surgery
- Cardiothoracic Surgery
- Gastro-intestinal and Colorectal Surgery
- General Surgery
- Neurosurgery
- Paediatric Surgery
- Peri-operative Care
- Plastic and Reconstructive Surgery
- Surgical Oncology
- Transplant Surgery
- Trauma and Orthopaedic Surgery
- Vascular Surgery
- Browse content in Science and Mathematics
- Browse content in Biological Sciences
- Aquatic Biology
- Biochemistry
- Bioinformatics and Computational Biology
- Developmental Biology
- Ecology and Conservation
- Evolutionary Biology
- Genetics and Genomics
- Microbiology
- Molecular and Cell Biology
- Natural History
- Plant Sciences and Forestry
- Research Methods in Life Sciences
- Structural Biology
- Systems Biology
- Zoology and Animal Sciences
- Browse content in Chemistry
- Analytical Chemistry
- Computational Chemistry
- Crystallography
- Environmental Chemistry
- Industrial Chemistry
- Inorganic Chemistry
- Materials Chemistry
- Medicinal Chemistry
- Mineralogy and Gems
- Organic Chemistry
- Physical Chemistry
- Polymer Chemistry
- Study and Communication Skills in Chemistry
- Theoretical Chemistry
- Browse content in Computer Science
- Artificial Intelligence
- Computer Architecture and Logic Design
- Game Studies
- Human-Computer Interaction
- Mathematical Theory of Computation
- Programming Languages
- Software Engineering
- Systems Analysis and Design
- Virtual Reality
- Browse content in Computing
- Business Applications
- Computer Security
- Computer Games
- Computer Networking and Communications
- Digital Lifestyle
- Graphical and Digital Media Applications
- Operating Systems
- Browse content in Earth Sciences and Geography
- Atmospheric Sciences
- Environmental Geography
- Geology and the Lithosphere
- Maps and Map-making
- Meteorology and Climatology
- Oceanography and Hydrology
- Palaeontology
- Physical Geography and Topography
- Regional Geography
- Soil Science
- Urban Geography
- Browse content in Engineering and Technology
- Agriculture and Farming
- Biological Engineering
- Civil Engineering, Surveying, and Building
- Electronics and Communications Engineering
- Energy Technology
- Engineering (General)
- Environmental Science, Engineering, and Technology
- History of Engineering and Technology
- Mechanical Engineering and Materials
- Technology of Industrial Chemistry
- Transport Technology and Trades
- Browse content in Environmental Science
- Applied Ecology (Environmental Science)
- Conservation of the Environment (Environmental Science)
- Environmental Sustainability
- Environmentalist Thought and Ideology (Environmental Science)
- Management of Land and Natural Resources (Environmental Science)
- Natural Disasters (Environmental Science)
- Nuclear Issues (Environmental Science)
- Pollution and Threats to the Environment (Environmental Science)
- Social Impact of Environmental Issues (Environmental Science)
- History of Science and Technology
- Browse content in Materials Science
- Ceramics and Glasses
- Composite Materials
- Metals, Alloying, and Corrosion
- Nanotechnology
- Browse content in Mathematics
- Applied Mathematics
- Biomathematics and Statistics
- History of Mathematics
- Mathematical Education
- Mathematical Finance
- Mathematical Analysis
- Numerical and Computational Mathematics
- Probability and Statistics
- Pure Mathematics
- Browse content in Neuroscience
- Cognition and Behavioural Neuroscience
- Development of the Nervous System
- Disorders of the Nervous System
- History of Neuroscience
- Invertebrate Neurobiology
- Molecular and Cellular Systems
- Neuroendocrinology and Autonomic Nervous System
- Neuroscientific Techniques
- Sensory and Motor Systems
- Browse content in Physics
- Astronomy and Astrophysics
- Atomic, Molecular, and Optical Physics
- Biological and Medical Physics
- Classical Mechanics
- Computational Physics
- Condensed Matter Physics
- Electromagnetism, Optics, and Acoustics
- History of Physics
- Mathematical and Statistical Physics
- Measurement Science
- Nuclear Physics
- Particles and Fields
- Plasma Physics
- Quantum Physics
- Relativity and Gravitation
- Semiconductor and Mesoscopic Physics
- Browse content in Psychology
- Affective Sciences
- Clinical Psychology
- Cognitive Psychology
- Cognitive Neuroscience
- Criminal and Forensic Psychology
- Developmental Psychology
- Educational Psychology
- Evolutionary Psychology
- Health Psychology
- History and Systems in Psychology
- Music Psychology
- Neuropsychology
- Organizational Psychology
- Psychological Assessment and Testing
- Psychology of Human-Technology Interaction
- Psychology Professional Development and Training
- Research Methods in Psychology
- Social Psychology
- Browse content in Social Sciences
- Browse content in Anthropology
- Anthropology of Religion
- Human Evolution
- Medical Anthropology
- Physical Anthropology
- Regional Anthropology
- Social and Cultural Anthropology
- Theory and Practice of Anthropology
- Browse content in Business and Management
- Business Ethics
- Business Strategy
- Business History
- Business and Technology
- Business and Government
- Business and the Environment
- Comparative Management
- Corporate Governance
- Corporate Social Responsibility
- Entrepreneurship
- Health Management
- Human Resource Management
- Industrial and Employment Relations
- Industry Studies
- Information and Communication Technologies
- International Business
- Knowledge Management
- Management and Management Techniques
- Operations Management
- Organizational Theory and Behaviour
- Pensions and Pension Management
- Public and Nonprofit Management
- Social Issues in Business and Management
- Strategic Management
- Supply Chain Management
- Browse content in Criminology and Criminal Justice
- Criminal Justice
- Criminology
- Forms of Crime
- International and Comparative Criminology
- Youth Violence and Juvenile Justice
- Development Studies
- Browse content in Economics
- Agricultural, Environmental, and Natural Resource Economics
- Asian Economics
- Behavioural Finance
- Behavioural Economics and Neuroeconomics
- Econometrics and Mathematical Economics
- Economic History
- Economic Systems
- Economic Methodology
- Economic Development and Growth
- Financial Markets
- Financial Institutions and Services
- General Economics and Teaching
- Health, Education, and Welfare
- History of Economic Thought
- International Economics
- Labour and Demographic Economics
- Law and Economics
- Macroeconomics and Monetary Economics
- Microeconomics
- Public Economics
- Urban, Rural, and Regional Economics
- Welfare Economics
- Browse content in Education
- Adult Education and Continuous Learning
- Care and Counselling of Students
- Early Childhood and Elementary Education
- Educational Equipment and Technology
- Educational Strategies and Policy
- Higher and Further Education
- Organization and Management of Education
- Philosophy and Theory of Education
- Schools Studies
- Secondary Education
- Teaching of a Specific Subject
- Teaching of Specific Groups and Special Educational Needs
- Teaching Skills and Techniques
- Browse content in Environment
- Applied Ecology (Social Science)
- Climate Change
- Conservation of the Environment (Social Science)
- Environmentalist Thought and Ideology (Social Science)
- Management of Land and Natural Resources (Social Science)
- Natural Disasters (Environment)
- Pollution and Threats to the Environment (Social Science)
- Social Impact of Environmental Issues (Social Science)
- Sustainability
- Browse content in Human Geography
- Cultural Geography
- Economic Geography
- Political Geography
- Browse content in Interdisciplinary Studies
- Communication Studies
- Museums, Libraries, and Information Sciences
- Browse content in Politics
- African Politics
- Asian Politics
- Chinese Politics
- Comparative Politics
- Conflict Politics
- Elections and Electoral Studies
- Environmental Politics
- Ethnic Politics
- European Union
- Foreign Policy
- Gender and Politics
- Human Rights and Politics
- Indian Politics
- International Relations
- International Organization (Politics)
- Irish Politics
- Latin American Politics
- Middle Eastern Politics
- Political Behaviour
- Political Economy
- Political Institutions
- Political Methodology
- Political Communication
- Political Philosophy
- Political Sociology
- Political Theory
- Politics and Law
- Politics of Development
- Public Policy
- Public Administration
- Qualitative Political Methodology
- Quantitative Political Methodology
- Regional Political Studies
- Russian Politics
- Security Studies
- State and Local Government
- UK Politics
- US Politics
- Browse content in Regional and Area Studies
- African Studies
- Asian Studies
- East Asian Studies
- Japanese Studies
- Latin American Studies
- Middle Eastern Studies
- Native American Studies
- Scottish Studies
- Browse content in Research and Information
- Research Methods
- Browse content in Social Work
- Addictions and Substance Misuse
- Adoption and Fostering
- Care of the Elderly
- Child and Adolescent Social Work
- Couple and Family Social Work
- Direct Practice and Clinical Social Work
- Emergency Services
- Human Behaviour and the Social Environment
- International and Global Issues in Social Work
- Mental and Behavioural Health
- Social Justice and Human Rights
- Social Policy and Advocacy
- Social Work and Crime and Justice
- Social Work Macro Practice
- Social Work Practice Settings
- Social Work Research and Evidence-based Practice
- Welfare and Benefit Systems
- Browse content in Sociology
- Childhood Studies
- Community Development
- Comparative and Historical Sociology
- Disability Studies
- Economic Sociology
- Gender and Sexuality
- Gerontology and Ageing
- Health, Illness, and Medicine
- Marriage and the Family
- Migration Studies
- Occupations, Professions, and Work
- Organizations
- Population and Demography
- Race and Ethnicity
- Social Theory
- Social Movements and Social Change
- Social Research and Statistics
- Social Stratification, Inequality, and Mobility
- Sociology of Religion
- Sociology of Education
- Sport and Leisure
- Urban and Rural Studies
- Browse content in Warfare and Defence
- Defence Strategy, Planning, and Research
- Land Forces and Warfare
- Military Administration
- Military Life and Institutions
- Naval Forces and Warfare
- Other Warfare and Defence Issues
- Peace Studies and Conflict Resolution
- Weapons and Equipment

Riskwork: Essays on the Organizational Life of Risk Management
Professor of Accounting
- Cite Icon Cite
- Permissions Icon Permissions
This collection of essays deals with the situated management of risk in a wide variety of organizational settings—aviation, mental health, railway project management, energy, toy manufacture, financial services, chemicals regulation, and NGOs. Each chapter connects the analysis of risk studies with critical themes in organization studies more generally based on access to, and observations of, actors in the field. The emphasis in these contributions is upon the variety of ways in which organizational actors, in combination with a range of material technologies and artefacts, such as safety reporting systems, risk maps, and key risk indicators, accomplish and make sense of the normal work of managing risk— riskwork . In contrast to a preoccupation with disasters and accidents after the event, the volume as a whole is focused on the situationally specific character of routine risk management work. It emerges that this riskwor k is highly varied, entangled with material artefacts which represent and construct risks and, importantly, is not confined to formal risk management departments or personnel. Each chapter suggests that the distributed nature of this riskwork lives uneasily with formalized risk management protocols and accountability requirements. In addition, riskwork as an organizational process makes contested issues of identity and values readily visible. These ‘back stage/back office’ encounters with risk are revealed as being as much about emotional as they are rationally calculative. Overall, the collection combines constructivist sensibilities about risk objects with a micro-sociological orientation to the study of organizations.
Personal account
- Sign in with email/username & password
- Get email alerts
- Save searches
- Purchase content
- Activate your purchase/trial code
- Add your ORCID iD
Institutional access
Sign in with a library card.
- Sign in with username/password
- Recommend to your librarian
- Institutional account management
- Get help with access
Access to content on Oxford Academic is often provided through institutional subscriptions and purchases. If you are a member of an institution with an active account, you may be able to access content in one of the following ways:
IP based access
Typically, access is provided across an institutional network to a range of IP addresses. This authentication occurs automatically, and it is not possible to sign out of an IP authenticated account.
Choose this option to get remote access when outside your institution. Shibboleth/Open Athens technology is used to provide single sign-on between your institution’s website and Oxford Academic.
- Click Sign in through your institution.
- Select your institution from the list provided, which will take you to your institution's website to sign in.
- When on the institution site, please use the credentials provided by your institution. Do not use an Oxford Academic personal account.
- Following successful sign in, you will be returned to Oxford Academic.
If your institution is not listed or you cannot sign in to your institution’s website, please contact your librarian or administrator.
Enter your library card number to sign in. If you cannot sign in, please contact your librarian.
Society Members
Society member access to a journal is achieved in one of the following ways:
Sign in through society site
Many societies offer single sign-on between the society website and Oxford Academic. If you see ‘Sign in through society site’ in the sign in pane within a journal:
- Click Sign in through society site.
- When on the society site, please use the credentials provided by that society. Do not use an Oxford Academic personal account.
If you do not have a society account or have forgotten your username or password, please contact your society.
Sign in using a personal account
Some societies use Oxford Academic personal accounts to provide access to their members. See below.
A personal account can be used to get email alerts, save searches, purchase content, and activate subscriptions.
Some societies use Oxford Academic personal accounts to provide access to their members.
Viewing your signed in accounts
Click the account icon in the top right to:
- View your signed in personal account and access account management features.
- View the institutional accounts that are providing access.
Signed in but can't access content
Oxford Academic is home to a wide variety of products. The institutional subscription may not cover the content that you are trying to access. If you believe you should have access to that content, please contact your librarian.
For librarians and administrators, your personal account also provides access to institutional account management. Here you will find options to view and activate subscriptions, manage institutional settings and access options, access usage statistics, and more.
Our books are available by subscription or purchase to libraries and institutions.
| Month: | Total Views: |
|---|---|
| October 2022 | 15 |
| October 2022 | 2 |
| October 2022 | 5 |
| October 2022 | 2 |
| October 2022 | 1 |
| October 2022 | 3 |
| October 2022 | 1 |
| October 2022 | 2 |
| October 2022 | 4 |
| October 2022 | 104 |
| October 2022 | 3 |
| October 2022 | 2 |
| October 2022 | 1 |
| October 2022 | 1 |
| October 2022 | 1 |
| October 2022 | 1 |
| November 2022 | 4 |
| November 2022 | 2 |
| November 2022 | 4 |
| November 2022 | 12 |
| November 2022 | 1 |
| November 2022 | 1 |
| November 2022 | 2 |
| November 2022 | 50 |
| November 2022 | 2 |
| November 2022 | 4 |
| November 2022 | 1 |
| November 2022 | 9 |
| November 2022 | 1 |
| November 2022 | 1 |
| December 2022 | 3 |
| December 2022 | 9 |
| December 2022 | 2 |
| December 2022 | 8 |
| December 2022 | 104 |
| December 2022 | 2 |
| December 2022 | 3 |
| December 2022 | 4 |
| December 2022 | 1 |
| December 2022 | 5 |
| December 2022 | 2 |
| December 2022 | 5 |
| January 2023 | 2 |
| January 2023 | 2 |
| January 2023 | 2 |
| January 2023 | 9 |
| January 2023 | 3 |
| January 2023 | 2 |
| January 2023 | 2 |
| January 2023 | 2 |
| January 2023 | 9 |
| January 2023 | 3 |
| January 2023 | 2 |
| January 2023 | 2 |
| January 2023 | 2 |
| January 2023 | 2 |
| January 2023 | 2 |
| January 2023 | 2 |
| January 2023 | 131 |
| January 2023 | 2 |
| January 2023 | 3 |
| February 2023 | 1 |
| February 2023 | 7 |
| February 2023 | 2 |
| February 2023 | 12 |
| February 2023 | 3 |
| February 2023 | 13 |
| February 2023 | 12 |
| February 2023 | 4 |
| February 2023 | 230 |
| February 2023 | 2 |
| February 2023 | 2 |
| February 2023 | 23 |
| February 2023 | 5 |
| February 2023 | 2 |
| February 2023 | 7 |
| March 2023 | 14 |
| March 2023 | 28 |
| March 2023 | 4 |
| March 2023 | 1 |
| March 2023 | 104 |
| March 2023 | 1 |
| March 2023 | 3 |
| March 2023 | 2 |
| March 2023 | 7 |
| March 2023 | 8 |
| March 2023 | 4 |
| March 2023 | 3 |
| March 2023 | 2 |
| April 2023 | 5 |
| April 2023 | 37 |
| April 2023 | 41 |
| April 2023 | 6 |
| April 2023 | 29 |
| April 2023 | 3 |
| April 2023 | 1 |
| April 2023 | 3 |
| April 2023 | 23 |
| April 2023 | 4 |
| April 2023 | 2 |
| April 2023 | 25 |
| April 2023 | 1 |
| April 2023 | 18 |
| May 2023 | 2 |
| May 2023 | 39 |
| May 2023 | 2 |
| May 2023 | 28 |
| May 2023 | 6 |
| May 2023 | 3 |
| May 2023 | 29 |
| May 2023 | 1 |
| May 2023 | 21 |
| May 2023 | 18 |
| May 2023 | 11 |
| May 2023 | 25 |
| May 2023 | 4 |
| June 2023 | 7 |
| June 2023 | 4 |
| June 2023 | 2 |
| June 2023 | 12 |
| June 2023 | 4 |
| June 2023 | 2 |
| June 2023 | 6 |
| June 2023 | 2 |
| June 2023 | 6 |
| July 2023 | 2 |
| July 2023 | 3 |
| July 2023 | 7 |
| July 2023 | 1 |
| July 2023 | 5 |
| July 2023 | 2 |
| July 2023 | 1 |
| July 2023 | 1 |
| July 2023 | 1 |
| July 2023 | 1 |
| August 2023 | 2 |
| August 2023 | 4 |
| August 2023 | 2 |
| August 2023 | 6 |
| August 2023 | 1 |
| August 2023 | 2 |
| August 2023 | 1 |
| August 2023 | 2 |
| August 2023 | 2 |
| August 2023 | 4 |
| August 2023 | 2 |
| September 2023 | 5 |
| September 2023 | 2 |
| September 2023 | 1 |
| September 2023 | 2 |
| September 2023 | 7 |
| September 2023 | 1 |
| September 2023 | 1 |
| September 2023 | 4 |
| September 2023 | 2 |
| September 2023 | 1 |
| September 2023 | 2 |
| October 2023 | 3 |
| October 2023 | 4 |
| October 2023 | 1 |
| October 2023 | 8 |
| October 2023 | 4 |
| October 2023 | 1 |
| October 2023 | 1 |
| October 2023 | 1 |
| November 2023 | 1 |
| November 2023 | 2 |
| November 2023 | 21 |
| November 2023 | 1 |
| November 2023 | 2 |
| December 2023 | 1 |
| December 2023 | 4 |
| January 2024 | 4 |
| January 2024 | 5 |
| January 2024 | 70 |
| January 2024 | 1 |
| February 2024 | 2 |
| February 2024 | 9 |
| February 2024 | 3 |
| February 2024 | 1 |
| February 2024 | 51 |
| February 2024 | 1 |
| February 2024 | 1 |
| February 2024 | 2 |
| February 2024 | 20 |
| February 2024 | 1 |
| February 2024 | 1 |
| February 2024 | 4 |
| March 2024 | 2 |
| March 2024 | 7 |
| March 2024 | 1 |
| March 2024 | 3 |
| March 2024 | 11 |
| March 2024 | 1 |
| March 2024 | 2 |
| March 2024 | 1 |
| April 2024 | 3 |
| April 2024 | 14 |
| April 2024 | 5 |
| April 2024 | 2 |
| April 2024 | 1 |
| April 2024 | 13 |
| April 2024 | 1 |
| April 2024 | 2 |
| April 2024 | 2 |
| April 2024 | 2 |
| April 2024 | 1 |
| April 2024 | 6 |
| April 2024 | 18 |
| May 2024 | 2 |
| May 2024 | 5 |
| May 2024 | 18 |
| May 2024 | 2 |
| May 2024 | 4 |
| May 2024 | 4 |
| May 2024 | 20 |
| May 2024 | 1 |
| May 2024 | 3 |
| May 2024 | 3 |
| May 2024 | 4 |
| May 2024 | 14 |
| May 2024 | 3 |
| June 2024 | 7 |
| June 2024 | 7 |
| June 2024 | 3 |
| June 2024 | 19 |
| June 2024 | 8 |
| June 2024 | 10 |
| June 2024 | 12 |
| June 2024 | 9 |
| June 2024 | 3 |
| June 2024 | 15 |
| June 2024 | 1 |
| June 2024 | 2 |
| June 2024 | 4 |
| June 2024 | 9 |
| June 2024 | 8 |
| June 2024 | 1 |
| June 2024 | 13 |
| June 2024 | 8 |
| June 2024 | 9 |
| June 2024 | 13 |
| July 2024 | 1 |
| July 2024 | 1 |
| July 2024 | 2 |
| July 2024 | 7 |
| July 2024 | 4 |
| July 2024 | 2 |
| July 2024 | 1 |
| July 2024 | 3 |
| July 2024 | 3 |
| July 2024 | 3 |
| July 2024 | 3 |
| July 2024 | 2 |
| August 2024 | 1 |
| September 2024 | 4 |
| September 2024 | 8 |
| September 2024 | 4 |
| September 2024 | 2 |
| September 2024 | 5 |
| September 2024 | 2 |
| September 2024 | 2 |
| September 2024 | 2 |
| September 2024 | 1 |
| September 2024 | 6 |
- About Oxford Academic
- Publish journals with us
- University press partners
- What we publish
- New features
- Open access
- Rights and permissions
- Accessibility
- Advertising
- Media enquiries
- Oxford University Press
- Oxford Languages
- University of Oxford
Oxford University Press is a department of the University of Oxford. It furthers the University's objective of excellence in research, scholarship, and education by publishing worldwide
- Copyright © 2024 Oxford University Press
- Cookie settings
- Cookie policy
- Privacy policy
- Legal notice
This Feature Is Available To Subscribers Only
Sign In or Create an Account
This PDF is available to Subscribers Only
For full access to this pdf, sign in to an existing account, or purchase an annual subscription.

Essay on Risk Management
Students are often asked to write an essay on Risk Management in their schools and colleges. And if you’re also looking for the same, we have created 100-word, 250-word, and 500-word essays on the topic.
Let’s take a look…
100 Words Essay on Risk Management
What is risk management.
Risk Management is the process of identifying, assessing, and controlling threats to an organization’s capital and earnings. These threats or risks could stem from a wide variety of sources, including financial uncertainty, legal liabilities, strategic management errors, accidents, and natural disasters.
Importance of Risk Management
Risk Management is important because it prepares an organization to face uncertainties. It helps to understand potential risks and to make plans to minimize their impact. Proper risk management can reduce not only the likelihood of an event occurring, but also the magnitude of its impact.
Steps in Risk Management
Risk Management involves several steps. The first step is identifying the risks. The next step is analyzing the risk to understand its potential impact. The third step is evaluating or ranking the risk. The final step is treating or controlling the risk.
Risk Management Techniques
There are several techniques for managing risk. One is risk avoidance, where the aim is to eliminate all risks. Another technique is risk reduction, where steps are taken to reduce the severity of the loss. Risk retention and risk transfer are other techniques used in risk management.
250 Words Essay on Risk Management
Risk Management is a process that helps identify, assess, and control threats that could harm an organization. These threats or risks could be anything from financial problems, accidents, natural disasters, or even legal issues. The main goal of Risk Management is to lessen the impact of these risks.
Risk Management follows four main steps. First, we identify the risks. This means we look at what could possibly go wrong. Next, we assess the risks. We try to figure out how likely it is that these risks will happen and how much damage they could cause. Then, we work on ways to control these risks. This could mean coming up with a plan to prevent the risk or lessen its impact. Finally, we monitor the risks. We keep an eye on them to see if they change or if new risks come up.
Risk Management is very important because it helps organizations prepare for the unexpected. It helps them make plans that can prevent or lessen damage from risks. It also helps them save money that they might lose if these risks were to happen.
In conclusion, Risk Management is a necessary practice for all organizations. It helps them identify, assess, control, and monitor risks. By doing this, organizations can prevent or lessen the impact of these risks, saving them from potential damage and loss.
500 Words Essay on Risk Management
Risk Management is a process that helps you identify and control possible problems that might happen in the future. It’s like a safety net that prepares you for any unexpected events.
Why is Risk Management Important?
Risk Management includes four main steps:
1. Identifying the Risks: The first step is to find out what could go wrong. This could be anything from a machine breaking down to a sudden change in market trends. 2. Analyzing the Risks: Next, you need to understand how big the problem could be. This helps to decide which risks need the most attention. 3. Planning the Response: Once you know the risks, you can make plans to handle them. This could mean avoiding the risk, reducing its impact, or accepting it and making a plan to recover from it. 4. Monitoring the Risks: Finally, you need to keep an eye on the risks and how well your plans are working. This means you can make changes if needed.
Benefits of Risk Management
Risk management in everyday life.
So, Risk Management is a very helpful tool. It prepares us for the future and helps to avoid or reduce problems. It is used in businesses, but also in our everyday lives. By understanding and using Risk Management, we can make better decisions and be ready for whatever comes our way.
Apart from these, you can look at all the essays by clicking here .
Happy studying!
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
- Risk management
- Share this item with your network:
Tech Accelerator
Risk management is the process of identifying, assessing and controlling threats to an organization's capital, earnings and operations. these risks stem from a variety of sources, including financial uncertainties, legal liabilities, technology issues, strategic management errors, accidents and natural disasters. this comprehensive guide explains why risk management is more important than ever and leads readers through how to establish a risk management plan, with hyperlinked articles with additional, essential information., what is risk management and why is it important.
- Linda Tucci, Industry Editor -- CIO/IT Strategy
- Craig Stedman, Industry Editor
Risk management is the process of identifying, assessing and controlling threats to an organization's capital, earnings and operations. These risks stem from a variety of sources, including financial uncertainties, legal liabilities, technology issues, strategic management errors, accidents and natural disasters.
A successful risk management program helps an organization consider the full range of risks it faces. Risk management also examines the relationship between different types of business risks and the cascading impact they could have on an organization's strategic goals.
This holistic approach to managing risk is sometimes described as enterprise risk management because of its emphasis on anticipating and understanding risk across an organization. In addition to a focus on internal and external risk threats, enterprise risk management (ERM) emphasizes the importance of managing positive risk. Positive risks are opportunities that could increase business value or, conversely, damage an organization if not taken, as the companies disrupted by Amazon, Netflix and other born-digital powerhouses will attest.
Indeed, the aim of any risk management program is not to eliminate all risk but to preserve and add to overall enterprise value by making smart risk decisions.
"We don't manage risks so we can have no risk. We manage risks so we know which risks are worth taking, which ones will get us to our goal, which ones have enough of a payout to even take them," said Forrester Research senior analyst Alla Valente, who specializes in governance, risk and compliance (GRC), third-party risk management, ERM and other risk-related topics.
Thus, a risk management program should be intertwined with organizational strategy. To link them, risk management leaders must first define the organization's risk appetite -- i.e., the amount of risk it is willing to accept to realize its objectives. Some risks will fit within the risk appetite and be accepted with no further action necessary. Others will be mitigated to reduce the potential negative effects, shared with or transferred to another party, or avoided altogether.
Every organization faces the risk of unexpected, harmful events that can cost it money -- or, in the worst case, cause it to close. This guide to risk management provides a comprehensive overview of the key concepts, requirements, tools, trends and debates driving this dynamic field. Throughout, hyperlinks connect to other TechTarget articles that deliver in-depth information on the topics covered here, so be sure to click on them to learn more.
Why is risk management important?
Risk management has perhaps never been more important than it is now. The risks that modern organizations face have grown more complex, fueled by the rapid pace of globalization. New risks are constantly emerging, often related to and generated by the now-pervasive use of digital technology. Climate change has been dubbed a "threat multiplier" by risk experts.
A recent external risk that initially manifested itself as a supply chain issue at many companies -- the COVID-19 pandemic -- quickly evolved into an existential threat, affecting the health and safety of employees, the means of doing business, the ability to interact with customers and corporate reputations.
Businesses made rapid adjustments to the threats posed by the pandemic. But, going forward, they are grappling with novel risks, including the ongoing issue of how or whether to bring employees back to the office, what can be done to make supply chains less vulnerable, inflation and the business and economic effects of the war in Ukraine.
In many companies, business executives and the board of directors are taking a fresh look at their risk management programs. Organizations are reassessing their risk exposure , examining risk processes and reconsidering who should be involved in risk management. Companies that currently take a reactive approach to risk management -- guarding against past risks and changing practices after a new risk causes harm -- are considering the competitive advantages of a more proactive approach. There is heightened interest in supporting business sustainability, resiliency and agility. Companies are also exploring how AI technologies and sophisticated GRC platforms can improve risk management.
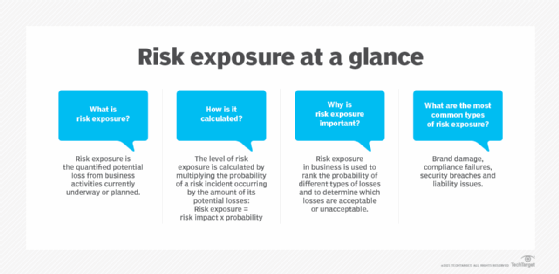
Financial vs. nonfinancial industries. In discussions of risk management, many experts note that managing risk is a formal function at companies that are heavily regulated and have a risk-based business model.
Banks and insurance companies, for example, have long had large risk departments typically headed by a chief risk officer (CRO), a title still relatively uncommon outside of the financial industry. Moreover, the risks that financial services companies face tend to be rooted in numbers and therefore can be quantified and effectively analyzed using known technology and mature methods. Risk scenarios in finance companies can be modeled with some precision.
For other industries, risk tends to be more qualitative and therefore harder to manage, increasing the need for a deliberate, thorough and consistent approach to risk management, said Gartner analyst Matt Shinkman, who leads the consulting firm's enterprise risk management and audit practices. "Enterprise risk management programs aim to help these companies be as smart as they can be about managing risk," he added.
Traditional risk management vs. enterprise risk management
Traditional risk management often gets a bad rap these days compared to enterprise risk management . Both approaches aim to mitigate risks that could harm organizations. Both buy insurance to protect against a range of risks -- from losses due to fire and theft to cyber liability . Both adhere to guidance provided by the major standards bodies. But traditional risk management, experts argue, lacks the mindset and mechanisms required to understand risk as an integral part of enterprise strategy and performance.
For many companies, "risk is a dirty four-letter word -- and that's unfortunate," said Forrester's Valente. "In ERM, risk is looked at as a strategic enabler versus the cost of doing business."
"Siloed" vs. holistic is one of the big distinctions between the two approaches, according to Shinkman. In traditional risk management programs, for example, risk has typically been the job of the business leaders in charge of the units where the risk resides. For example, the CIO or CTO is responsible for IT risk, the CFO is responsible for financial risk, the COO for operational risk and so on. Departments and business units might have sophisticated systems in place to manage their various types of risks, Shinkman explained, but the company can still run into trouble by failing to see the relationships among risks or their cumulative impact on operations. Traditional risk management also tends to be reactive rather than proactive.
"The pandemic is a great example of a risk issue that is very easy to ignore if you don't take a holistic, long-term strategic view of the kinds of risks that could hurt you as a company," Shinkman said. "A lot of companies will look back and say, 'You know, we should have known about this, or at least thought about the financial implications of something like this before it happened.'"
In enterprise risk management, managing risk is a collaborative, cross-functional and big-picture effort. An ERM team , which could be as small as five people, works with the business unit leaders and staff to debrief them, help them use the right tools to think through the risks, collate that information and present it to the organization's executive leadership and board. Having credibility with executives across the enterprise is a must for risk leaders of this ilk, Shinkman said.
These types of experts increasingly come from a consulting background or have a "consulting mindset," he said, and they possess a deep understanding of the mechanics of business. Unlike in traditional risk management, where the head of risk typically reports to the CFO, the heads of enterprise risk management teams -- whether they hold the chief risk officer title or some other title -- commonly report to the CEO, an acknowledgement that risk is part and parcel of business strategy.
In defining the chief risk officer role, Forrester makes a distinction between the "transactional CROs" typically found in traditional risk management programs and the "transformational CROs" who take an ERM approach. The former work at companies that see risk as a cost center and risk management as an insurance policy, according to Forrester. Transformational CROs, in the Forrester lexicon, are "customer-obsessed," Valente said. They focus on their company's brand reputation, understand the horizontal nature of risk and define ERM as the "proper amount of risk needed to grow," as Valente put it.
Risk averse is another trait of organizations with traditional risk management programs. But as Valente noted, companies that define themselves as risk averse with a low risk appetite are sometimes off the mark in their risk assessments .
"A lot of organizations think they have a low risk appetite, but do they have plans to grow? Are they launching new products? Is innovation important? All of these are growth strategies and not without risk," Valente said.
Risk management glossary
Many terms are used to define the various aspects and attributes of risk management. Click on the hyperlinks below to learn more about some useful terms to know.
What is pure risk?
What is residual risk?
What is a risk profile?
What is integrated risk management?
What is risk reporting?
Risk management process
The risk management discipline has published many bodies of knowledge that document ways for organizations to manage risk. One of the best-known resources is the ISO 31000 standard . Formally called ISO 31000:2018 Risk management -- Guidelines, it was developed by the International Organization for Standardization, a standards body commonly known as ISO.
ISO 31000 outlines a risk management process that can be used by any type of entity and includes the following steps for identifying, assessing and managing risks:
- Identify the risks faced by your organization.
- Analyze the likelihood and possible impact of each one.
- Evaluate and prioritize the risks based on business objectives.
- Treat -- or respond to -- the risk conditions.
- Monitor the results of risk controls and adjust as necessary.
These steps are straightforward, but risk management committees should not underestimate the work required to complete the process. For starters, it requires a solid understanding of what makes the organization tick. To obtain that, the ISO 31000 process also includes an upfront step to establish the scope of risk management efforts, the business context for them and a set of risk criteria. The end goal is to know how each identified risk relates to the maximum risk the organization is willing to accept and what actions should be taken to preserve and enhance organizational value.
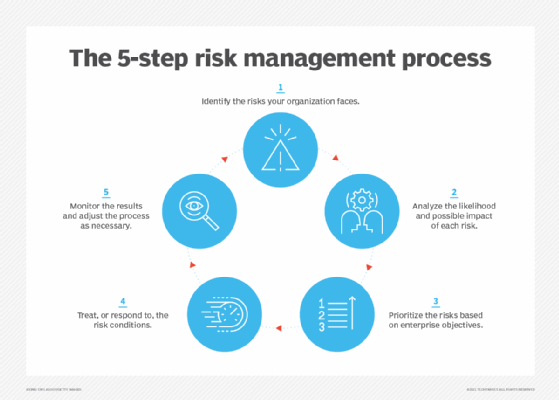
When identifying risks, it is important to understand that, by definition, something is only a risk if it has a business impact, according to risk expert Greg Witte, a senior security engineer for Huntington Ingalls Industries and an architect of frameworks developed by the National Institute of Standards and Technology ( NIST ) on cybersecurity, privacy and workforce risks, among others. For example, the following four factors must be present for a negative risk scenario, according to guidance from NISTIR 8286A , a report on identifying cybersecurity risk in ERM initiatives that NIST published in 2021:
- A valuable asset or resources that could be impacted.
- A source of a threatening action that would act against the asset or resources.
- A preexisting condition or vulnerability that enables the threat source to act.
- Some harmful impact that occurs from the threat source exploiting that vulnerability.
While the NIST criteria pertains to negative risks, similar processes can be applied to managing positive risks.
Top-down, bottom-up. In identifying risk scenarios that could impede or enhance an organization's objectives, many risk committees find it useful to take a top-down, bottom-up approach, Witte said. In the top-down exercise, leadership identifies the organization's mission-critical processes and works with internal and external stakeholders to determine the conditions that could impede them. The bottom-up perspective starts with the threat sources -- earthquakes, economic downturns, cyber attacks, etc. -- and considers their potential impact on critical assets.
The final task in the risk identification step is for organizations to record their findings in a risk register, which helps track the risks through the subsequent steps of the risk management process. An example of such a risk register can be found in the NISTIR 8286A report cited above.

Risk management standards and frameworks
As government and industry compliance rules have expanded over the past two decades, regulatory and board-level scrutiny of corporate risk management practices have also increased, making risk analysis , internal audits, risk assessments and other features of risk management a major component of business strategy. How can an organization put this all together?
The rigorously developed -- and evolving -- frameworks developed by the risk management field can help. Here is a sampling of them, starting with brief descriptions of the two most widely recognized frameworks, ISO 31000 and the COSO enterprise risk management framework offered by the Committee of Sponsoring Organizations of the Treadway Commission, better known as COSO:
- COSO ERM framework. Launched in 2004, the COSO framework was updated in 2017 to address the increasing complexity of ERM and highlight the importance of embedding risk considerations into business strategies and linking risk management and operational performance. It defines key concepts and principles of ERM, suggests a common ERM language and provides clear directions for managing risk. Developed by consulting firm PwC with input from COSO's five member organizations and external advisors, the updated framework is a set of 20 principles organized into five interrelated components:
- Governance and culture.
- Strategy and objective-setting.
- Performance.
- Review and revision.
- Information, communication and reporting.
- ISO 31000. Released in 2009 and revised in 2018, the ISO standard includes a list of ERM principles, a framework to help organizations apply risk management mechanisms to operations, and the process detailed above for identifying, evaluating and mitigating risks . Developed by ISO's risk management technical committee with input from ISO national member bodies, ISO 31000:2018 is a shorter and more concise document than its predecessor and includes more strategic guidance on ERM. The newer version also emphasizes the important role of senior management in risk programs and the integration of risk management practices throughout the organization.
- BS 31100. The current version of this British Standard risk management code of practice was issued in 2021 and provides a process for implementing concepts described in ISO 31000:2018 -- including functions such as identifying, assessing and responding to risks and then reporting on and reviewing risk management activities.
Other frameworks that focus specifically on IT and cybersecurity risks are also available. They include NIST's Risk Management Framework , which details a process for integrating security, data privacy and cybersecurity supply chain risk management initiatives into the system development lifecycle, and the ISACA professional association's COBIT 2019, an information and technology governance framework that supports IT risk management efforts.
Enterprises might also consider establishing customized frameworks for specific categories of risks. Carnegie Mellon University's enterprise risk management framework, for example, examines potential risks and opportunities based upon the following risk categories: reputation, life/health safety, financial, mission, operational and compliance/legal.
In addition, various risk maturity models can be used to benchmark risk management capabilities and assess their maturity levels. The most prominent one is the Risk and Insurance Management Society's Risk Maturity Model (RMM), which was developed in 2005 with software vendor LogicManager and updated in 2022. The revamped RMM helps risk professionals assess their programs in five categories: strategy alignment; culture and accountability; risk management capabilities; risk governance; and analytics. Other risk maturity models are available from the Risk Management Association, consulting firm Investors in Risk Management and the Organisation for Economic Co-operation and Development's Forum on Tax Administration.
The three lines model developed by the Institute of Internal Auditors (IIA) offers another type of standardized approach to support governance and risk management initiatives. Originally called the three lines of defense before being renamed in 2020, the IIA's model outlines the different roles that business executives, risk and compliance managers and internal auditors should play in risk management efforts, with a governing body providing oversight and accountability.
What are the benefits and challenges of risk management?
Effectively managing risks that could have a negative or positive impact on capital, earnings and operations brings many benefits. It also presents challenges, even for companies with mature GRC and risk management strategies.
Benefits of effective risk management include the following:
- Increased awareness of risk across the organization.
- More confidence in organizational objectives and goals because risk is factored into strategy.
- Better and more efficient compliance with regulatory and internal compliance mandates because compliance is coordinated.
- Improved operational efficiency through more consistent application of risk processes and controls.
- Improved workplace safety and security for employees and customers.
- A competitive differentiator in the marketplace.
The following are some of the challenges risk management teams should expect to encounter:
- Expenditures go up initially, as risk management programs can require expensive software and services.
- The increased emphasis on governance also requires business units to invest time and money to comply.
- Reaching consensus on the severity of risk and how to treat it can be a difficult and contentious exercise and sometimes lead to risk analysis paralysis.
- Demonstrating the value of risk management to executives without being able to give them hard numbers is difficult.
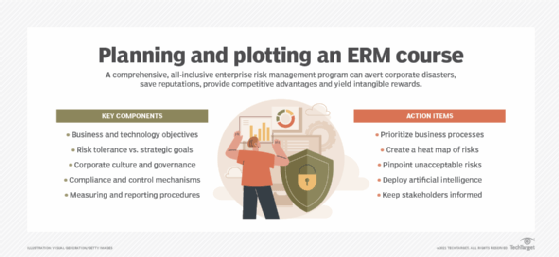
How to build and implement a risk management plan
A risk management plan describes how an organization will manage risk. It lays out elements such as the organization's risk approach, the roles and responsibilities of risk management teams, resources that will be used in the risk management process and internal policies and procedures.
ISO 31000's overall seven-step process is a useful guide to follow for developing a plan and then implementing an ERM framework , according to Witte. Here is a more detailed rundown of its components:
- Communication and consultation. Since raising risk awareness is an essential part of risk management, risk leaders must also develop a communication plan to convey the organization's risk policies and procedures to employees and relevant parties. This step sets the tone for risk decisions at every level. The audience includes anyone who has an interest in how the organization takes advantage of positive risks and minimizes negative ones.
- Establishing the scope and context. This step requires defining both the organization's risk appetite and risk tolerance -- the latter is how much the risks associated with specific initiatives can vary from the overall risk appetite. Factors to consider here include business objectives, company culture, regulatory requirements and the political environment, among others.
- Risk identification. This step defines the risk scenarios that could have a positive or negative impact on the organization's ability to conduct business. As noted above, the resulting list should be recorded in a risk register and kept up to date.
- Risk analysis. The likelihood and impact of each risk is analyzed to help sort risks. Making a risk heat map can be useful here; also known as a risk assessment matrix , it provides a visual representation of the nature and impact of a company's risks. An employee calling in sick, for example, is a high-probability event that has little or no impact on most companies. An earthquake, depending on location, is an example of a low-probability risk event with high impact. The qualitative approach many organizations use to rate the likelihood and impact of risks might benefit from a more quantitative analysis. The FAIR Institute, a professional association that promotes the Factor Analysis of Information Risk framework for cyber-risk quantification , has examples of the latter approach.

- Risk evaluation. Here is where organizations assess risks and decide how to respond to them through the following approaches:
- Risk avoidance , when the organization seeks to eliminate, withdraw from or not be involved in the potential risk.
- Risk mitigation , in which the organization takes actions to limit or optimize a risk.
- Risk sharing or transfer, which involves contracting with a third party (e.g., an insurer) to bear some or all costs of a risk that might or might not occur.
- Risk acceptance, when a risk falls within the organization's risk appetite and tolerance and is accepted without taking any risk reduction measures.
- Risk treatment. This step involves applying the agreed-upon controls and processes and confirming they work as planned.
- Monitoring and review. Are the controls working as intended? Can they be improved? Monitoring activities should measure performance and look for key risk indicators that might trigger a change in strategy.

Risk management best practices
A good starting point for any organization that aspires to follow risk management best practices is ISO 31000's nine principles of risk management. According to ISO, a risk management program should meet the following objectives:
- Create and protect value for the organization, as an overarching principle.
- Be integrated into overall organizational processes.
- Be systematic, structured and comprehensive.
- Be based on the best available information.
- Be tailored to individual projects.
- Account for human and cultural factors, including potential errors.
- Be transparent and all-inclusive.
- Be dynamic and adaptable to change.
- Be continuously monitored and improved upon.
Another best practice for the modern enterprise risk management program is to "digitally reform," said security consultant Dave Shackleford. This entails using AI and other advanced technologies to automate inefficient and ineffective manual processes. ERM and GRC platforms that include AI tools and other features are available from various risk management software vendors . Organizations can also take advantage of open source GRC tools and related resources .
Risk management for career professionals
The following articles provide resources for risk management professionals:
What is a risk management specialist?
Top risk management skills and why you need them
Top enterprise risk management certifications to consider
Risk management limitations and examples of failures.
Risk management failures are often chalked up to willful misconduct, gross recklessness or a series of unfortunate events no one could have predicted. But an examination of common risk management failures shows that risk management gone wrong is more often due to avoidable missteps -- and run-of-the-mill profit-chasing. Here is a rundown of some mistakes to avoid.
Poor governance. The tangled tale of Citibank accidentally paying off a $900 million loan, using its own money, to Revlon's lenders in 2020 when only a small interest payment was due shows how even the largest bank in the world can mess up risk management -- despite having updated policies for pandemic work conditions and multiple controls in place. While human error and clunky software were involved, a federal judge ruled that poor governance was the root cause, although an appeals court overturned an order that the bank wasn't entitled to refunds from the lenders. Nonetheless, two months after the erroneous payment, Citibank was fined $400 million by U.S. regulators for "longstanding" governance failures and agreed to overhaul its internal risk management, data governance and compliance controls.
Overemphasis on efficiency vs. resiliency. Greater efficiency can lead to bigger profits when all goes well. Doing things quicker, faster and cheaper by doing them the same way every time, however, can result in a lack of resiliency, as companies found out during the pandemic when supply chains broke down. "When we look at the nature of the world … things change all the time," said Forrester's Valente. "So, we have to understand that efficiency is great, but we also have to plan for all of the what-ifs."
Lack of transparency. The scandal involving the New York governor's office underreporting coronavirus-related deaths at nursing homes in the state during 2020 and 2021 is representative of a common failing in risk management. Hiding data, a lack of data and siloed data -- whether due to acts of commission or omission -- can cause transparency issues. Avoiding that requires an enterprise-wide risk management strategy with common risk terminology, documented processes and centralized collection and management of key risk data.
Limitations of risk analysis techniques. Many risk analysis techniques, such as creating a risk prediction model or a risk simulation, require gathering large amounts of data. Extensive data collection can be expensive and is not guaranteed to be reliable. Furthermore, the use of data in decision-making processes can have poor outcomes if simple indicators are used to reflect complex risk situations. In addition, applying a decision intended for one small aspect of a project to the whole project can lead to inaccurate results.
Lack of risk analysis expertise. Software programs developed to simulate events that might negatively impact a company can be cost-effective, but they also require highly trained personnel to accurately understand the generated results.
Illusion of control. Risk models can give organizations the false belief that they can quantify and regulate every potential risk. This could cause an organization to neglect the possibility of novel or unexpected risks.

Risk management trends: What's on the horizon?
The spotlight that was shined on risk management during the COVID-19 pandemic has driven many companies to not only reexamine their risk practices but also to explore new techniques, technologies and processes for managing risk. As a look at the trends that are reshaping risk management shows, the field is brimming with ideas.
More organizations are adopting a risk maturity model to evaluate their risk processes and better manage the interconnectedness of threats across the enterprise. They are looking anew at GRC platforms to integrate their risk management activities, manage policies, conduct risk assessments, identify gaps in regulatory compliance and automate internal audits, among other tasks. Newer GRC features that risk management experts said should be considered include the following:
- Analytics for geopolitical risks, natural disasters and other events.
- Social media monitoring to track changes in brand reputation.
- Security systems to assess the potential impact of data breaches and cyber attacks.
- Third-party risk assessment tools to help strengthen supply chain risk management .
In addition to using risk management to avoid bad situations, more companies are looking to formalize how to manage positive risks to add business value.
They are also taking a fresh look at risk appetite statements. Traditionally used as a means to communicate with employees, investors and regulators, risk appetite statements are starting to be used more dynamically, replacing "check the box" compliance exercises with a more nuanced approach to risk scenarios. The caveat? A poorly worded risk appetite statement could hem in a company or be misinterpreted by regulators as condoning unacceptable risks.
More organizations are connecting their risk management initiatives and environmental, social and governance ( ESG ) programs, too. That's making sustainability risk management and efforts to address other kinds of ESG risks a higher priority for companies looking to make their operations more sustainable and ensure that they're acting in responsible and ethical ways.
Finally, while it's tough to make predictions -- especially about the future, as the adage goes -- tools for measuring and mitigating risks are getting better. Among the improvements? Internal and external sensing tools that detect trending and emerging risks.
Dig Deeper on Risk management

How to conduct an API risk assessment and improve security

5 core steps in the risk management process

Top 12 IT security frameworks and standards explained
CI/CD processes help deploy code changes to networks. Integrating a CI/CD pipeline into automation makes networks more reliable, ...
Predictive analytics can project network traffic flows, predict future trends and reduce latency. However, tools continue to ...
Test scripts are the heart of any job in pyATS. Best practices for test scripts include proper structure, API integration and the...
To ensure an IT project's long-term success, stakeholders should keep track of certain KPIs to ensure technical debt is as low as...
The U.S. Commerce Department's proposal to ban software and hardware for connected vehicles imported from China or Russia might ...
Apple joined a list of big tech companies voluntarily committing to responsible AI. But without regulation, there is no legal ...
While wiping and reinstalling via a clean install is the simplest way to fix a broken Windows 11 desktop, an ISO file repair can ...
Organizations looking to boost productivity for key Windows users should learn what Copilot+ PCs can offer and what workflows the...
There are numerous generative AI tools that focus on enhancing user productivity, so organizations should survey the market to ...
The author of The Official CompTIA Cloud+ Instructor Guide and Student Guide shares his most interesting takeaways from the ...
If your cloud-based workloads and applications need to move back on premises, you'll need a plan. Start your reverse migration ...
Cloud repatriation should be a last resort, not a repudiation of the cloud. Do you know how to fully optimize cloud workloads to ...
Amazon Web Services criticises Competition and Markets Authority for failing to take into account competitive threat posed by ...
Malaysian property developer UEM Sunrise is leveraging Salesforce and AI to boost sales and enhance customer experience while ...
Post Office dramatically increased the number of investigations into subpostmasters after Capture Software was introduced
- Formatting Styles
Risk management, meaning, and importance for companies

Checked : Suzanne S. , Michael T.
Latest Update 19 Jan, 2024
Table of content
Risk management: what is it?
Importance of risk management in business, risk management helps in risk identification, analysis, control, and treatment of the risk, avoid scams, data security, prevention of crime, prevents theft, conclusions.
The history of economic systems and financial markets in recent years has been characterized by many cases of crisis and, in the most pathological situations, of failures that have certainly left their mark. However, there is a very recurrent element that characterizes these negative situations. It is the misalignment between performance profiles and risk profiles within the decision-making system and corporate governance. The strong emphasis given to the need to achieve performance targets, especially in the short term, has often left little room for evaluation, and to quantify risk where possible associated with certain types of choices. The result was that there was a misalignment between the maximization of results compared to the capacity of companies and banking and financial companies to create value.
It is no coincidence, therefore, that one of the most important legacies that history has left us in recent years is the growing attention to risk assessment and management issues, in a word that is commonly called risk management.
What is risk management? This is the question that many people ask themselves when approaching the world of financial markets. Whether you are an investor, an entrepreneur or an aspiring one, you have found yourself in the position of having to understand exactly what risk management is and what the right techniques are to avoid the loss of your capital.
Risk management is the continuous process of identifying, analyzing, evaluating, and managing exposures to losses and controlling risk and financial resources to minimize the negative effects of a loss.
The main function of the set of risk management techniques is to maximize profits, trying to reduce the risk of losses.
The losses that the individual seeks to minimize with risk management can come from:
- financial risks
- operational risks
- political and environmental risks
- strategic risks
More extensively, risk management addresses the downsizing of all those factors that prevent an individual or a company from achieving its objectives.
Although accidental losses are unpredictable and unplanned, there are methods included in risk management that can make risk events more predictable.
The more predictable an event, the lower the risk as it can be prevented or minimized. Furthermore, unexpected expenses can be estimated and budgeted.
This is risk management, the process to make the losses more predictable. This is the definition that can be given of the whole set of techniques that seek to secure, to the extent possible, the investor's capital.
The key to proper risk management is to control all the functions of your risk management plan and make sure that they are necessary and effective to reduce the overall cost of operational risk.
Risks are part of life as much as they are part of any organization or company planning. It’s quite natural to face risks in your business that needs to be handled in such a way that it does not result in a loss to the business or business services that are provided. Risk management is the forecasting or evaluation of possible risks and identifying the process to avoid or overcome it. It utilizes the right methods and tools to handle the threat. With a risk management plan, you can always be prepared in advance and let the business not be affected by it. Here are a few reasons why risk management is essential for business.
One of the major tasks of risk management is to identify a risk when it is about to rise or has risen. It can categorize various risks related to financing, operations, strategic, and even referred to like the environment and the public. This would either help you to avoid the chance at the early stages or come up with plans on facing the risks.
Once a risk is identified, it is important to analyze it to see how it will affect the business and come up with measures to control or overcome it. Risk has to be treated carefully so that it doesn’t change the entire industry. The probabilities of loss and gain have to be discussed before preparing to deal with it.
Risk management helps your business to avoid scams and analyses how it would affect the image of your business. Further, they help your business by investigating the source of fraud and helps in filtering the scam. They also help in building up the tarnished image if involved in a scam or fake scams.
It assures that all your essential data regarding the business are safeguarded and does not fall into the wrong hands. Data security is vital in business, and the risk management team can help you with the necessary protection. They can also come up with data recovery, backups, and insurances for your business data to not lose it and affect your business.
They make sure that the business decisions you make are legally approved and help in preventing crime in business. Furthermore, they see to the security of your employees too and assure that laws are not broken. This helps in not just creating an impression about your business to your employees but also to visitors and consumers.
One of the major risks for a business company is the theft of an idea or data. This can lead to the loss of a company. With the right risk management team, they will assure that your thoughts and business plans are safe and are not leaked. With simple measures and tracking employees, it can be assured that data leakage does not happen through unfaithful employees. They also help in keeping an eye on the inventory.

We Will Write an Essay for You Quickly
Risk management as a stream helps in securing your business to the next level. It is always best to have prevention, and having an active risk management team does precisely. It may seem scary to the possible risks. But with the right directions and solutions, it’s always easy to overcome them or even face them. Having a risk management team adds extra security to your business. It helps you in a-z of all the disasters, security, and risks of the business. If you don’t have a risk management team yet, it is high time you get one.
The growing challenges that characterize industrial, banking, insurance, and financial companies require the constant presence within the decision-making and control system of these organizations of skills and dedicated activities that allow them never to lose sight of the risk profile. It is a central theme in the life of companies. It is important, however, that this presence has the nature of a substance and does not only serve to comply with regulatory requirements or to construct façade solutions that serve no purpose concerning the responsible management of the business and the sustainability of the life of these companies over time.
Looking for a Skilled Essay Writer?

- Ohio State University Bachelor's degree
No reviews yet, be the first to write your comment
Write your review
Thanks for review.
It will be published after moderation
Latest News

What happens in the brain when learning?
10 min read
20 Jan, 2024

How Relativism Promotes Pluralism and Tolerance

Everything you need to know about short-term memory
- Search Search Please fill out this field.
What Is Business Risk?
Understanding business risk, reducing business risk, the bottom line, business risk: definition, factors, and examples.
:max_bytes(150000):strip_icc():format(webp)/wk_headshot_aug_2018_02__william_kenton-5bfc261446e0fb005118afc9.jpg)
Business risk is the exposure a company or organization has to factor(s) that will lower its profits or lead it to fail. Anything that threatens a company’s ability to achieve its financial goals is considered a business risk .
There are many factors that can converge to create business risk. Sometimes it is a company’s top leadership or management that creates situations where a business may be exposed to a greater degree of risk.
However, sometimes the cause of risk is external to a company. Because of this, it is impossible for a company to completely shelter itself from risk. However, there are ways to mitigate the overall risks associated with operating a business ; most companies accomplish this by adopting a risk management strategy.
Key Takeaways
- Business risk is any exposure a company or organization has to factor(s) that may lower its profits or cause it to go bankrupt.
- The sources of business risk are varied but include changes in consumer taste and demand, the state of the overall economy, and government rules and regulations.
- Risk can be created by external factors that the business doesn’t control, as well as by decisions made within the company’s management or executive team.
- While companies may not be able to completely avoid business risk, they can take steps to mitigate its impact, including the development of a strategic risk plan.
Xiaojie Liu / Investopedia
When a company experiences a high degree of business risk, it may impair its ability to provide investors and stakeholders with adequate returns. For example, the chief executive officer (CEO) of a company may make certain decisions that affect its profits, or the CEO may not accurately anticipate certain events in the future, causing the business to incur losses or fail.
Business risk is influenced by a number of different factors, including:
- Consumer preferences, demand, and sales volumes
- Per-unit price and input costs
- Competition
- The overall economic climate
- Government regulations
A company with a higher amount of business risk may decide to adopt a capital structure with a lower debt ratio to ensure that it can meet its financial obligations at all times. With a low debt ratio, when revenues drop, the company may not be able to service its debt (and this may lead to bankruptcy ). On the other hand, when revenues increase, a company with a low debt ratio experiences larger profits and is able to keep up with its obligations.
To calculate risk, analysts use four ratios: contribution margin, operation leverage effect, financial leverage effect, and total leverage effect. For more complex calculations, analysts can incorporate statistical methods.
Business risk usually occurs in one of four ways: strategic risk, compliance risk, operational risk, and reputational risk .
Types of Business Risk
Strategic risk.
Strategic risk arises when a business does not operate according to its business model or plan. When a company does not operate according to its business model, its strategy becomes less effective over time, and the company may struggle to reach its defined goals.
For example, imagine ABC Store is a big box store that strategically positions itself as a low-cost provider for working-class shoppers. Its main competitor is XYZ Store, which is seen as a destination for more middle-class consumers. However, if XYZ decides to undercut ABC’s prices, this becomes a strategic risk for ABC.
Compliance Risk
The second form of business risk is compliance risk, sometimes known as regulatory risk. Compliance risk primarily arises in industries and sectors that are highly regulated. For example, in the wine industry, there is a three-tier system of distribution that requires wholesalers in the United States to sell wine to a retailer, which then sells it to consumers. This system prohibits wineries from selling their products directly to retail stores in some states.
However, many U.S. states do not have this type of distribution system; compliance risk arises when a brand fails to understand the individual requirements of the state in which it is operating. In this situation, a brand risks becoming noncompliant with state-specific distribution laws and may face fines or other legal action.
Operational Risk
The third type of business risk is operational risk . This risk arises from within the corporation, especially when the day-to-day operations of a company fail to perform.
For example, in 2012, the multinational bank HSBC faced a high degree of operational risk and, as a result, incurred a large fine from the U.S. Department of Justice when its internal anti-money laundering (AML) operations team was unable to adequately stop money laundering in Mexico.
Reputational Risk
Anytime a company’s reputation is ruined, either by an event that was the result of a previous business risk or by a different occurrence, it runs the risk of losing customers and its brand loyalty suffering. The reputation of HSBC faltered in the aftermath of the fine it was levied for poor anti-money laundering practices.
Business risk cannot be entirely avoided because it is unpredictable. However, there are many strategies that businesses employ to cut back the impact of all types of business risk, including strategic, compliance, operational, and reputational risk.
The first step that brands typically take is to identify all sources of risk in their business plan . These aren’t just external risks—they may also come from within the business itself. Taking action to cut back the risks as soon as they present themselves is key. Management should come up with a plan to deal with any identifiable risks before they become too great.
Finally, most companies adopt a risk management strategy . This can be done either before the business begins operations or after it experiences a setback. Ideally, a risk management strategy will help the company be better prepared to deal with risks as they present themselves. The plan should have tested ideas and procedures in place in case risk presents itself.
Once the management of a company has come up with a plan to deal with the risk, it’s important that they take the extra step of documenting everything in case the same situation arises again. After all, business risk isn’t static—it tends to repeat itself during the business cycle. By recording what led to risk the first time, as well as the processes used to mitigate it, the business can implement those strategies a second time with greater ease. This reduces the time frame in which unaddressed risk can impact the business, as well as lowering the cost of risk management.
What Are the 4 Main Types of Business Risk?
The four main types of risk that businesses encounter are strategic, compliance (regulatory), operational, and reputational risk. These risks can be caused by factors that are both external and internal to the company.
Why Is Risk Management Important in Business?
Businesses face a great deal of uncertainty in their operations, much of it outside their control. This uncertainty creates risk that can jeopardize a company’s short-term profits and long-term existence. Because risk is unavoidable, risk management is an important part of running a business. When a business has a thorough and carefully created risk management plan in place, and when it is able to iterate on that plan to deal with new and unexpected risks, the business is more likely to survive the impact of both internal and external risk.
What Are Internal Risks That Can Impact a Business?
Internal risks that can impact a business often come from decisions made by the management or executive team in pursuit of growth. These decisions can create physical or tangible risks. For example, on-site risks such as fires, equipment malfunctions, or hazardous materials can jeopardize production, endanger employees, and lead to legal or financial penalties. Policies that guarantee a safe working environment would, in this instance, be an effective strategy for managing internal risks.
In business, risks are factors that an organization encounters that may lower its profits or cause it to fail. Sources of risk can be external, such as changes in what consumers want, changes in competitor behavior, external economic factors, and government rules or regulations. They can also be internal, such as decisions made by management or the executive team.
No company can completely avoid risks, especially because many risk factors are external. However, businesses can put risk management strategies into place. These strategies can be used to reduce risk and to mitigate the impact of risks when they arise. By documenting the sources of risk and creating a strategic plan that can be repeated, businesses can reduce the overall impact of risk and deal with it more efficiently and effectively in the future.
National Alcohol Beverage Control Association. “ Alcohol Regulation 101: Three-Tier System .”
National Alcohol Beverage Control Association. “ Alcohol Regulation 101: Structure of U.S. Alcohol Regulation .”
U.S. Department of Justice, Office of Public Affairs. “ HSBC Holdings Plc and HSBC Bank USA N.A. Admit to Anti-Money Laundering and Sanctions Violations, Forfeit $1.256 Billion in Deferred Prosecution Agreement .”
:max_bytes(150000):strip_icc():format(webp)/operational_risk.asp-Final-4be32b4ee5c74958b22dfddd7262966f.png)
- Terms of Service
- Editorial Policy
- Privacy Policy
- Call to +1 844 889-9952
Strategic Risk Management
| 📄 Words: | 1621 |
|---|---|
| 📝 Subject: | |
| 📑 Pages: | 7 |
| ✍️ Type: | Essay |
Introduction
Managers in different companies choose to focus on enterprise risk management (ERM) to predict and address possible risks that may be associated with companies’ operations and activities. ERM can cover a range of risks potentially faced by organizations (McShane, Nair, and Rustambekov 642). In addition to managing risks associated with problems in operations, deliveries, and interactions with suppliers or customers, leaders need to focus on more significant risks that might influence the strategic course of the organization and its further development (Tonello par. 3).
These are known as strategic risks, and managers concentrate on specific activities to predict and overcome these threats to the organization’s progress in the context of strategic risk management (SRM) (Frigo and Anderson 21). The purpose of this paper is to introduce the concept of SRM, discuss its definition and role, describe its principles, analyze activities that are available to assess and manage risks, and focus on the link of SRM to ERM.
Definition of SRM and Its Role
Strategic risks belong to a specific group of threats directly connected with companies’ strategic objectives. From this point, strategic risks can prevent an organization from achieving its business objectives (Wade par. 2). These risks include problems that cause a decrease in the company’s value and prospects for further growth.
Definition of SRM
In this context, strategic risk management or SRM is defined as a process of determining, evaluating, and addressing risks that are directly associated with the company’s strategy and can lead to the business or strategic failure (Tonello par. 3). Therefore, the manager’s task is to identify possible risks, assess their impact on the strategic development of an organization, and formulate a plan of action to manage risk or overcome a problem (Gandini, Gennari, and Cassano 2). With this in mind, SRM is a complex of techniques utilized by managers to increase the value for shareholders and the overall profitability of the business while reducing the number of potential risks.
The Role of SRM
However, it is important to note that strategic risk management cannot be discussed only as a group of certain actions developed to identify and address negative tendencies, processes, or risks. SRM is also significant in understanding how risks can be overcome to increase the competitive advantage of the firm (Risk and Insurance Management Society 3). It is possible to state that SRM covers “strategic planning, risk management and strategy execution in managing risks and seizing opportunities not only for protection against losses but for reducing uncertainties and seizing opportunities” (Risk and Insurance Management Society 3).
As a result, it is possible to guarantee “better performance in achieving the organization’s objectives and greater resilience in an uncertain environment” (Risk and Insurance Management Society 3). Thus, SRM is important for predicting strategic risks and contributing to the business’s value.
Principles of SRM
Researchers and managers have identified six main principles of SRM:
- this process is oriented toward determining and assessing risks that are internal and external;
- the main focus is on determining the possible shareholders’ value;
- SRM is a component of ERM;
- managers who are responsible for realizing ERM are also responsible for SRM activities;
- the focus is on the assessment of risks from a strategic perspective;
- SRM is a continual and systematic process (Frigo and Anderson 22).
Thus, according to the first principle, it is important to refer to and assess both internal and external factors to guarantee the realization of strategic objectives without obstacles. Furthermore, SRM is developed to address the needs of shareholders who expect to overcome risks and increase value.
Also, SRM should be viewed as a part of ERM, and this aspect influences the roles of managers who become responsible not only for predicting potential threats and barriers to daily operations but also for identifying factors that affect the strategic progress of an organization (Tonello par. 10). The strategic perspective is very important in this case because managers evaluate how observed contingencies and other internal and external factors can be related to the set objectives as a part of a company’s strategy (Frigo and Anderson 22). Finally, the sixth principle of strategic risk management accentuates that this process cannot be disorganized or irregular because managers need to routinely evaluate the company’s course of actions and possible risks according to set strategic objectives since SRM is a systematic process.
SRM Activities to Manage Risks
The SRM process is based on a range of activities that include identifying, assessing, and managing risks.
SRM for Identifying and Assessing Risks
At the first stage, it is important to determine or predict risks that can affect strategic objectives in an organization (Frigo and Anderson 22). The second step is assessing these risks and classifying them according to the level of their severity. The reason is that managers need to understand what risks they can face on the path to achieving strategic objectives and how these risks can influence the overall working process (Tonello par. 10). Furthermore, assessment of risks is necessary to develop an appropriate plan of action that can be used to address the identified threats. As stated by researchers, this process is systematic, and the assessment is to be conducted at each stage of the work on completing the set strategic tasks (Frigo and Anderson 22; Tonello par. 10).
SRM for Managing Risks
The activities that are not related to the assessment stage involve the direct completion of tasks aimed at addressing, decreasing, or overcoming risks. Techniques that are used in strategic risk management to address possible risks and uncertainties are many, and managers choose among them depending on the needs of the firm that can be identified with the help of the SWOT (Strengths, Weaknesses, Opportunities, Threats) analysis and other similar approaches (Gandini, Gennari, and Cassano 2). Therefore, following a stage involving assessment, managers will choose strategic planning and the development of alternative scenarios to cope with barriers that were identified with the help of the assessment.
At this stage, the activities selected in the context of strategic risk management can be divided into those that are risk-taking and others that are risk-reducing. Risk-taking activities are associated with the idea that some types of risks are not threatening to the organization, and they can be assessed and viewed as providing opportunities for further sustainable or strategic growth (Risk and Insurance Management Society 7).
The organization chooses to take the identified risks to achieve strategic goals (Wade par. 3). The other activities are risk-reducing, and they are most often discussed in the context of SRM as directed toward overcoming identified threats. With this in mind, SRM activities at the stage of overcoming or taking a risk include making decisions regarding investments, mergers or acquisitions, and expansion in marketing efforts, as well as other strategic actions.
The Connection between SRM and ERM
According to the principles that are used to explain SRM and integrate it into processes developed in an organization, this complex of practices should be viewed as an important part of ERM (Frigo and Anderson 22). From this point, there is a direct link between planning and realizing ERM and SRM activities and techniques. While following the principles of SRM, those persons who are responsible for predicting and assessing threats to operations in an organization also work to identify risks that can influence the realization of the strategy that has been determined.
However, in contrast to ERM, which is oriented to resolving practical tasks, SRM is focused on addressing such tasks as the creation of value for the shareholders and the prediction of barriers to realizing the strategic objectives which have been set for the business. Therefore, if ERM is effective to administer daily issues related to general operations, the strategic risk management as a component of enterprise risk management is important for proposing approaches to address such issues as consequences of mergers and acquisitions, the financial crisis, and changes in domestic and global markets, among other things (Frigo and Anderson 23).
Researchers and managers are inclined to discuss ERM and SRM as closely connected concepts and processes that can influence the effectiveness of a business’s work (Tonello par. 14). Therefore, when executives focus on implementing the principles of SRM in their organization, the first challenge they may face is the necessity of integrating the approaches to working with strategic risks into the framework that is oriented to reducing practical risks. Still, it is important to note that SRM cannot work effectively if ERM processes are not systematized and regulated appropriately.
It is important to note that SRM as a process is aimed at increasing an organization’s competitive advantage and the potential for growth in the market. According to modern business tendencies, risk management should be directly connected with the business strategy, and at this stage, the focus is on SRM as an approach to address uncertainties associated with the strategic progress of the firm.
Taking this into consideration, while introducing the concept of SRM, it is important to focus on such specific aspects as the definition of strategic risk management, its role and importance, and the principles that regulate the use of SRM in organizations. Also, it is possible to identify six principles that allow for speaking about the clear connection between enterprise risk management and strategic risk management.
Furthermore, it is also important for managers to understand what practices associated with SRM can be used at different stages of dealing with risks. The practices can include the processes of predicting, identifying, evaluating, and addressing the determined threats that can affect the company’s strategy and its value. In conclusion, even though SRM is a comparably new concept, its principles and ideas are actively used in modern management to guarantee to achieve strategic goals.
Works Cited
Frigo, Mark, and Richard Anderson. “ What Is Strategic Risk Management? ”. Strategic Finance 92.10 (2011): 21-24. Web.
Gandini, Giuseppina, Francesca Gennari, and Raffaella Cassano. “Global Responsibility and Strategic Risk Management.” Journal of Business Management and Applied Economics 3.5 (2014): 1-17. Print.
McShane, Michael, Anil Nair, and Elzotbek Rustambekov. “Does Enterprise Risk Management Increase Firm Value?” Journal of Accounting, Auditing & Finance 26.4 (2011): 641-658. Print.
Risk and Insurance Management Society. Why Strategic Risk Management? 2011. Web.
Tonello, Matteo. Strategic Risk Management: A Primer for Directors . 2012. Web.
Wade, Jared. How Strategic Risk Management Improves a Company’s Competitive Standing . 2012. Web.
Cite this paper
Select style
- Chicago (A-D)
- Chicago (N-B)
BusinessEssay. (2022, December 5). Strategic Risk Management. https://business-essay.com/strategic-risk-management/
"Strategic Risk Management." BusinessEssay , 5 Dec. 2022, business-essay.com/strategic-risk-management/.
BusinessEssay . (2022) 'Strategic Risk Management'. 5 December.
BusinessEssay . 2022. "Strategic Risk Management." December 5, 2022. https://business-essay.com/strategic-risk-management/.
1. BusinessEssay . "Strategic Risk Management." December 5, 2022. https://business-essay.com/strategic-risk-management/.
Bibliography
BusinessEssay . "Strategic Risk Management." December 5, 2022. https://business-essay.com/strategic-risk-management/.
- Government Agencies: Risk Management Plans Comparison
- Risk Management Practices in the Fire Service
- British Petroleum Firm’s Risk Management Plan
- Corporate Risk Management Decisions
- Risk Workshop and Risk Register
- Risk Management in IT Projects
- Risk Management in Railway Construction
- Project Risk Management: Aspects and Tools
- Financial Risk Management in International Banks
- Banking Risk Management and Performance
- Pronto Courier’s Information Security Management
- Economic Risk Management in Supply Chain
- Apple Company: Enterprise Risk Management
- Risk Management and Corporate Governance
- Security Manager and Risk Management
Risk Working Papers
Recent articles.

The future of bank risk management

Managing supplier risk in the transportation and infrastructure industry

Managing the people side of risk

Voices on bank transformation: Insights on creating lasting change

People and talent management in risk and control functions


A marathon, not a sprint: Capturing value from BCBS 239 and beyond

An executive’s guide to machine learning

Improving disaster recovery

Repelling the cyberattackers
Developing robust PPNR estimates

Taking the stress out of operational-risk stress testing

The age of utility: Are you a force that shapes the power markets, or do the forces shake you?

McKinsey Capital Management Survey 2015

P&L forecasting–the new horizon of stress testing, and beyond

A best-practice model for bank compliance
2014 article archive.

Enterprise-risk-management practices: Where’s the evidence?

Europe’s wholesale gas market: Innovate to survive

Introducing a holistic approach to stress testing

A time for stress: The challenges facing Europe's banks

Risk in emerging markets: The way forward for leading banks
2013 article archive, between deluge and drought: the divided future of european bank-funding markets, risk-based resource allocation: focusing regulatory and enforcement efforts where they are needed the most, getting to erm: a road map for banks and other financial institutions, concrete steps for cfos to improve strategic risk management, between deluge and drought: liquidity and funding for asian banks, managing third-party risk in a changing regulatory environment, next-generation energy trading: an opportunity to optimize, between deluge and drought: the future of us bank liquidity and funding, the hypotenuse and corporate risk modeling, strategic choices for midstream gas companies, strategic commodity and cash-flow-at-risk modeling for corporates, 2012 article archive, managing market risk: today and tomorrow, compliance and control 2.0: unlocking potential through compliance and quality-control activities, driving value from postcrisis operational risk management, day of reckoning for european retail banking, strategic insight through stress-testing: how to connect the 'engine room' to the boardroom, first-mover matters: building credit monitoring for competitive advantage, capital management: banking's new imperative, commodity trading at a strategic crossroad, enterprise risk management: what's different in the corporate world and why, 2011 article archive, the use of economic capital in performance management for banks, assessing and addressing the implications of new financial regulations for the us banking industry, strengthening risk management in the us public sector, day of reckoning new regulation and its impact on capital-markets businesses, new credit-risk models for the unbanked, good riddance: excellence in managing wind-down portfolios, mastering icaap: achieving excellence in the new world of scarce capital, 2010 article archive, taking control of organizational risk culture, a board perspective on enterprise risk management, variable annuities in europe after the crisis: blockbuster or niche product, after black swans and red ink: how institutional investors can rethink risk management, getting to grips with counterparty risk, top-down erm: a pragmatic approach to managing risk from the c-suite, credit underwriting after the crisis, basel iii and european banking: its impact, how banks might respond, and the challenges of implementation, getting risk ownership right, 2009 article archive, upgrading your risk assessment for uncertain times, responding to the variable annuity crisis, best practices for estimating credit economic capital, bad banks: finding the right exit from the financial crisis, risk modeling in a new paradigm: developing new insight and foresight on structural risk, the national credit bureau: a key enabler of financial infrastructure and lending in developing economies, capital ratios and financial distress: lessons from the crisis, 2008 article archive, the risk revolution, making risk management a value-added function in the boardroom, incorporating risk and flexibility in manufacturing footprint decisions, liquidity: managing an undervalued resource in banking after the crisis of 2007-2008, turning risk management into a true competitive advantage: lessons from the recent crisis, probabilistic modeling as an exploratory decision-making tool, "option games": filling the hole in the valuation toolkit for strategic investment, shaping strategy in a highly uncertain macro-economic environment.
- View PDF
- Download full issue

European Journal of Operational Research
Invited review risk assessment and risk management: review of recent advances on their foundation.
- • The paper reviews recent advances on the foundation of risk assessment and management.
- • Trends in perspectives and approaches are identified.
- • The paper points to areas where further developments of the risk field are needed.
- • Examples of integrative risk research are highlighted.
- Previous article in issue
- Next article in issue
Cited by (0)
- Search Close search
- Find a journal
- Search calls for papers
- Journal Suggester
- Open access publishing
We’re here to help
Find guidance on Author Services
Open access
Business risk management in the context of small and medium-sized enterprises
- Cite this article
- https://doi.org/10.1080/1331677X.2020.1844588
1. Introduction
2. literature review, 3. purpose, data and methodology, 5. discussion, 6. conclusion, disclosure statement, additional information.
- Full Article
- Figures & data
- Reprints & Permissions
- View PDF PDF View EPUB EPUB
The aim of this paper is to review the impact of entrepreneurs' attitudes toward the defined business risks on the perception of the future of small and medium-sized enterprises (SMEs). 454 SMEs from the Czech Republic (CR) participated in the research and completed an online questionnaire. Structural equation modelling and factor analysis were used to identify the causal relationships between the examined variables. Entrepreneurs' attitudes toward business failure also have a positive effect on the future of the SME. The perception of financial risk in positive indicators of financial performance and the perception of financial risk as part of the company's everyday life have the most significant impact on future business. Operational risk is reflected in the utilisation of corporate resources, reducing customer complaints about the quality of the company's products and the company's independence of a limited number of suppliers. The company's sales volume adequacy provides a source of market risk. It has the third strongest positive impact on the future business in the SME segment. The research results provide a valuable platform for the authors of national and regional development strategic plans looking for SME support and development as well as the authors of the relevant policies.
- Small and medium-sized enterprises
- business failure
- business environment
- business risk
- companýs future
The responsibility of an SME owner/top SME manager to make strategic decisions plays the key role in ensuring financial prosperity and the sustainability of SMEs in the business environment (Cepel et al., Citation 2018 ) or a smooth digitalization process (Dincă et al., Citation 2019 ). Business decisions are made under uncertainty and risk. SMEs are becoming more aware of the need for risk management and control (Wegner et al., Citation 2017 ).
The benefits of SME risk management are highlighted by several authors. The primary effects are seen in the gradual increase of SME financial performance; improving the SME position in the business segment; improving services/products for customers and the employee productivity (Psarska et al., Citation 2019 ). The secondary effects become evident not only in the improved economic indicators (purchasing power of the population, etc.) in the SME location (city, region) but also in the country’s macroeconomic indicators (Audretsch & Keilbach, Citation 2005 ).
It is important to help companies with risk management, i.e. identify, analyse, evaluate and manage risks (Belas et al., Citation 2018 ). The diagnostics of risk sources in SMEs is the most important phase of risk management because preventive actions can only be devised to eliminate the identified risk (Gorzeń-Mitka, Citation 2019 ).
The adverse consequences of the absence of business risk management threaten the very existence of a company (Balcaen & Ooghe, Citation 2006 ). This includes the inability to pay debts to suppliers, employees, the state, and the lack of job orders from customers, unfavourable values of financial indicators of the company, or stressful situations between employees and the management. These side effects translate into the company’s insolvency and often lead to its liquidation (Chłodnicka & Zimon, Citation 2020 ).
Given the important position of SMEs in the overall economic system of national policies and the European Union as a whole, there are efforts to analyse the business risks and their relationship to the direction of a business in the future in more detail (Lima et al., Citation 2020 ).
The study was motivated by these consistent facts, focusing on the perception of business risks and business failure in relation to future business in the SME segment.
The structure of the paper is as follows: The literature review is focused on business risk management. In the next part of the study, the database, methodology and procedures are described. The analytical part contains a proposed and verified SEM model with fit-test characteristics and the most important results of factor analysis. They provide a platform for the discussion part and conclusions. The conclusion of the study is a comprehensive evaluation of the results and their applicability for different types of policies. It also implies many topics for subsequent research in this field.
Fear of the future is amongst the most important reasons why entrepreneurs do not engage in business (Cacciotti et al., Citation 2016 ). Business literature identified the difference between entrepreneurs and managers lies in their level of openness to experience (e.g. Zhao & Seibert, Citation 2006 ). Shane et al. ( Citation 2010 ) says that openness to experience explains much of the variation in the genetic predisposition of an individual and underlines its importance in the business process. Business stability and performance is based on the implementation of an enterprise risk management system (Gordon et al., Citation 2009 ).
Several studies (e.g. Dvorsky et al., Citation 2020 ; Grimsdottir & Edvardsson, Citation 2018 ) confirm the application of strategic management elements in the SME sector is somewhat different compared to large enterprises and it is considerably limited and questionable. Svarova and Vrchota ( Citation 2013 ) examined a sample of 176 respondents for the relationship between the implementation of strategic management in the SME segment and its market stability and financial success of the company. The authors concluded based on empirical research that a formulated strategy has a positive effect on the SME financial performance while at the same time it does not influence the financial success of the SME. Klammer et al. ( Citation 2017 ) provide that SMEs that are business-oriented and willing to learn can have successful strategic management.
H1: The entrepreneur's attitude toward strategic risk management has a positive effect on the perception of a company's future (FB).
Market risk is determined by a number of causes focused on the overall level of market competitiveness (Malega et al., Citation 2019 ). Market risk can be defined as the strategic risk of SMEs which consists in the long-term retention of the existing customers and in the acquisition and retention of new customers and in the production of new products or delivery of new services (Rowland et al., Citation 2019 ). Nothing but a sufficient number of customers allows SMEs to implement a reasonable sales volume which allows them to maintain their market position (Herath & Mahmood, Citation 2014 ). The level of a company's competitiveness is largely based on two main factors of the competitive environment: customers and competitors (De Clercq et al., Citation 2013 ). SMEs must develop their competitive advantages to survive; the companies managing scarce resources that are difficult to replace typically gain a competitive advantage (Vochozka & Psarska, Citation 2016 ). One such resource is human resources (Caseiro & Coelho, Citation 2018 ). Businesses must be able to innovate new products, achieve success and growth, and satisfy consumer demand (O'Cass & Sok, Citation 2014 ). Business performance is the primary goal of any type of firm, being a top priority for managers (Trif et al., Citation 2019 ).
H2: The entrepreneur's attitude toward market risk management has a positive effect on the perception of a company's future.
The level of financial risk must be assessed in terms of the risk performance in a company towards successful financial risk management decisions because risk is considered an integral part of a company's business (Olah et al., Citation 2019 ). Financial risk is one of the main threats to SME business (Yang, Citation 2017 ). Difficulties in business financing and lack of funds are the most common symptoms of SME financial risk (Bosma et al., Citation 2018 ) because most of the operation of the company is financed by the capital of owners or managers themselves. This may result in the increase of operating costs and corporate debt, and debt repayment problems and consequently high financial risk. Access to finance is likely to improve the quality of a business environment by leading firms toward a more productive scope of business.
The purpose of the Yao Wang study ( Citation 2016 ) was to analyse the biggest obstacles to the growth of SMEs from the perspective of business managers based on the World Bank enterprise survey including data from 119 developing countries. SMEs consider the access to funds as the critical obstacle to their growth while managers consider the access to finance, tax rates and competition as the biggest obstacles to the external financing of SMEs.
H3: The entrepreneur's attitude toward financial risk management has a positive effect on the perception of a company's future.
The quality of human capital in a company provides the basis for increasing the company’s performance (Gede Riana et al., Citation 2020 ). Empirical studies show that voluntary efforts by employees will increase productivity and ultimately performance (Neary et al., Citation 2018 ). They also create a competitive advantage for the company (Habanik et al., Citation 2020 ). It is important to develop a positive interpersonal relationship between individuals working at different levels of the organisation (Alnoor, Citation 2020 ). Employees working together with others to build a social interpersonal relationship uphold the need for affiliation and fellowship. The social exchange and reciprocity theories explain how managers and the behaviour of co-workers determine the quality of this relationship and influence the judgments of employees (Redmond & Sharafizad, Citation 2020 ).
H4: The entrepreneur's attitude toward personnel risk management has a positive effect on the perception of a company's future.
The political stability and orientation of a country the company chooses to operate in are highly important for SMEs. Political factors set up the legal framework and control the business environment (Dickson & Weaver, Citation 2008 ).
Cepel et al. ( Citation 2018 ) says the political and legal environment provides a legal and supporting framework for business activities and it regulates the international business relations, tax and levy policies, antitrust policy, the stability of the legal environment, judicial efficiency, and law enforcement, or the administrative burden on businesses, etc.
The government regulation is perceived as the major obstacle to market entry (Lutz et al., Citation 2010 ). Stenholm et al. ( Citation 2013 ) studied a sample of 65 countries to identify how differences in the institutional organisation may affect business activities in a country. The authors consider the institutional methods and regulatory provisions are connected to the level of business activities, and therefore they suggest to facilitate the entry of new companies into the market which may have a positive effect on business activities.
H5: The entrepreneur's attitude toward legal risk management has a positive effect on the perception of a company's future.
The impact of SME internal capabilities on a competitive advantage was studied by Games and Roliza ( Citation 2019 ) while they also considered the age of the company. In the case of Indonesia, the SME internal capability had a strong and positive correlation with a competitive advantage. For SMEs with less than five years of operation, this connection is weak in comparison to older companies. Innovation has a profound and significant influence on the company's competitiveness through increasing productivity as documented in the transitional market study (Ngoc Mai et al., Citation 2019 ). A higher level of customer satisfaction and loyalty leads to a higher support for the purchasing processes. The important indicators that may affect the narrower business environment include the support of business customers and suppliers (Balan et al., Citation 2019 ). The support of corporate customers has a greater effect on the narrower business environment. Mafini and Muposhi ( Citation 2017 ) studied the relationship between SMEs and their suppliers. The authors suggest the existence of long-term relationships between SMEs and their suppliers does not automatically lead to better risk management.
H6: The entrepreneur's attitude toward operational risk management has a positive effect on the perception of a company's future.
Empirical studies emphasize the determinants and consequences of business failure (Karabag, Citation 2019 ). In general, SME bankruptcy research can be divided into three main parts: (i) predictive models, (ii) finance and law, and (iii) organizational failure. Another current research topic addresses the issue of perception, consequences and costs of business failure (Ucbasaran et al., Citation 2013 ).
The significant causes of business failure include: lack of planning activities of the company's management; lack of working capital; offering too much credit to customers (Hanzaee et al., Citation 2011 ); failure to implement rapid outsourcing; market competition; insufficient monitoring of corporate finances (Santisteban & Mauricio, Citation 2017 ).
Other factors may also contribute to business failure. Süsi and Lukason ( Citation 2019 ) stated the risk of failure decreases as the manager’s age increases and managerial ownership is present. On the other hand, the presence of larger management boards and managers in other companies will increase the risk of failure.
H7: The entrepreneur's attitude toward business failure (BF) has a positive effect on the perception of a company's future.
The aim of this paper is to review the impact of entrepreneurs' attitudes toward the defined business risks on the perception of the future of SMEs. Following the goal definition, empirical research was conducted using online questionnaires. Data was collected in the CR from 9/2019 to 3/2020. 8250 SMEs were randomly selected from the Cribis database. This SME database is considered to be the most reliable sources of information concerning businesses in the Czech business environment. The questioning technique was used to receive feedback from respondents to specific statements by completing an online questionnaire. In the first phase, respondents were contacted by email with a structured request for completion of a questionnaire. In the second phase, SMEs were contacted by telephone.
The questionnaire consisted of several parts. The questions were assigned to the questionnaire by random (except for the demographic characteristics of respondent). The statements concerning business risks, the perception of BF and future business were formulated in a positive way to maintain the continuity of logical thinking. Provided that business risks are managed correctly by SMEs, then the future of SMEs is perceived more positively. The average return of questionnaires was 3.6%. Respondents’ opinions were based on the Likert's five-point scale: 1 "I strongly agree" to 5 "I strongly disagree" with a statement. The questionnaire was completed by 465 respondents. The number of correctly/incorrectly completed questionnaires (hereinafter referred to as the sample) was represented by 454/11 respondents. The general evaluation of questions looking at the characteristics of a company and respondent is shown in Table 1 .
Table 1. Structure of respondents according to demographic characteristics.
To achieve the aim of the study, the authors selected methods of mathematical statistics (factor analysis (FA) and structural equation modelling - SEM) for verification.
The FA was applied in the first step. The process of the FA exploration technique can be logically organized into three steps: i. data validation; ii. factor extraction; iii. factor rotation (Brown, Citation 2015 ).
The SEM method is an appropriate tool for constructing, identifying and quantifying the relationships between latent variables (Smith et al., Citation 1998 ) as well as their graphical representation using a structural model. The final structural model can identify and quantify complex, not only direct but also indirect relationships of latent variables to each other and between latent and manifest variables (Levy, Citation 2011 ).
Latent variables are considered to be the most significant business risks that are impossible to measure directly. Latent variables can be defined using manifest variables (Babin et al., Citation 2008 ).
The suitability of a test model can be verified by selected measures: Goodness of Fit (GFI); CMIN/DF - The minimum discrepancy; Comparative Fit index (CFI); Roat Mean Square Error of Approximation (RMSEA); Normed fit index (NFI). The SEM model is statistically significant if: the GFI p-value is greater than 0.05 (Hooper et al., Citation 2008 ); CMIN/Df value is within the interval of −2 to 2 (Byrne & Reinhart, Citation 1989 ); the RMSA value ranges from 0 to 0.05 (Smith et al., Citation 1998 ); the NFI index value is greater than 0.9 (Bentler, Citation 1990 ); the CFI value is greater than 0.95 (Wheaton et al., Citation 1977 ). All the above tests were performed through IBM SPSS Statistics and IBM SPSS Amos.
The general description of business risk indicators, BF indicators and the perceived future of business (mean (M), standard deviation (SD), sample skewness (S) and kurtosis (K)) are summarized in Table 2 . Table 2 shows the results of factor reliability and the relationship between the corrected item (CI) and the total correlation (TC) of a selected factor.
Table 2. Descriptive statistics (DS) of indicators and Cronbach´s Alpha (CA) test results.
The results in Table 2 show that although the Cochran´s alpha values exceed 0.7, the corrected item-total correlation (CI-TC) of indicators such as MR4, FR1, FR4, LEG4, BF5 is lower than 0.5. The indicator reliability is not acceptable according to Hair et al. ( Citation 2010 ). These results were also confirmed in the individual (factor) KMO tests. The factor loading (FL) understood as a correlation of each item and a factor should be better than 0.5 (Hair et al., Citation 2010 ) to ensure the indicator is correlated with the type of business risk or BF. The results indicate that MR4 (FL = 0.214); FR3 (FL = 0.284); FR4 (FL = 0.322); LEG2 (FL = 0.417); PER3 (FL = 0.474); PER4 (FL = 0.451); BF3 (FL = 0.397) do not meet the above threshold requirements. The results of a KMO test and Bartlet test of sphericity without the above indicators are illustrated in Table 3 .
Table 3. Kaiser-Meyer-Olkin test (KMO) and Bartlett´s test results.
The KMO test results in Table 3 confirmed a proportion of variance of the individual variables that can be explained by background factors. The reason is that the KMO test value is close to the value of 1, or a large proportion of the variance is explained by factors. Also, the results of the Bartlet test (P - value = 0.000) showing the null hypotheses that the correlation coefficient of the variables in the sample is zero are accepted at a significance level of 0.05.
The Varimax rotation technique (6 iterations) was used to interpret the factor matrix. If the results of the indicator iterative process showed a less communality of indicators with high transverse overload (> | 0.4 |), then they were removed. Table 4 summarizes the results of the rotated solution of the indicator matrix.
Table 4. Rotated component matrix – indicator to business risk relationship.
The results obtained with the Principal Component Analysis extraction method: 8 factors; the maximum number in the range of 5-10 factors. The result of the BIC method is 8 factors. The obtained results are very satisfactory in view of the defined number of latent variables (6 - business risk types, 1 - perception of BF by the respondent) and 1 endogenous variable (perception of future business by the respondent). Table 5 shows the results of the total variance explained by the above factors.
Table 5. Total variance explained.
Based on the values in Table 5 , it was concluded that the selected factors explain nearly 64.7% of the variability in the total variance. Based on the results in Tables 4 and 5 , it was concluded that all selected factors are identified. These results are identical to the scree plot which also confirmed the number of 8 factors since the very 8 components, consequently denoted by factors, were obtained using Kaiser rule (more than 1% of the total variance; Bentler, Citation 1990 ). Other non-significant indicators which do not strongly correlate with the selected factors are shown below the running mark in the scree plot (MR4, FR3, FR4, LEG2, PER3, PER4 and BF3 - see also Table 2 ). The scree plot is not included in the results due to duplicated results obtained in Tables 4 and 5 .
The characteristics of a structural model ( Figure 1 ) that was subsequently verified by the summary fit characteristics are as follows: one dependent variable and seven independent variables; latent variables measured by manifest variables (indicators), each manifest variable contains an unexplained part (residual errors not explained by the model); the relationship between latent exogenous variables (SR, …, OPE, BF) and endogenous variables (FB) is determined by an arrow. The above process resulted in a structural (SEM) model ( Figure 1 ) of the relationship between business risks, perception of BF and perception of future business.
Figure 1. SEM model with standardized estimates. Source: created by the authors in the IBM SPSS AMOS software.

The resulting model ( Figure 1 ) is the best solution to the proposed model and empirical data based on the Summary Fit Model (see Table 6 ). The resulting model assumes that selected types of business risks are independent. To achieve satisfactory results, it was necessary to remove variables from the SEM model (based on the path coefficient: OPE2, MR2, SR1, SR3, BF3. Before interpreting the structural model of relationships (see Figure 1 ), the most important FIT tests of the created SEM model were calculated and interpreted (see Tables 6 and 7 ).
Table 6. Hypothesis testing and path coefficients (positive effects).
Table 7. sem model - summary fit model..
The results of the GFI characteristic (see Table 7 ) demonstrated the statistical significance of the structural model (p-value = 0.061). The SEM model has the value of CMIN/Df. = 1.914. This value is at the upper limit of acceptability because the CMIN/Df value higher than 2 indicates a poor fit of the proposed SEM model with data in the sample of SME attitudes. The RMSA value is higher than the recommended SEM model acceptance interval <0; 0.5>. However, Smith et al. ( Citation 1998 ) provides that if the RMSA value is in the range <0.5; 0.8>, the SEM model is accepted. The values of the NFI and CFI fit tests are below the limit of perfect agreement.
Based on the above results of the SEM model verification, hypotheses H1,…, H7 are supported.
The results of the SEM model of the specific research areas of business risks and BFs allowed us to set up an interesting discussion platform. It was identified that the perception of positive future business is influenced by all identified types of business risks. The level of their impact is not the same as that which is also connected with the many macroeconomic effects as well as the attitudes of the examined SMEs. The effective risk management in SMEs is deciding to a large extent whether they are fit to survive in the market and contributes to the development not only of a company but also its market and social environment. At the same time, note the appropriate risk management requires a certain degree of risk perception in a given business environment, risk identification, planning and alignment of preventive measures, or risk management systems (Ślusarczyk & Grondys, Citation 2019 ). The results show that financial risk has the most significant positive impact on a perception of the future (path coefficient - PC = 0.16). Financial risk is determined by a positive perception of financial risk as part of everyday life as well as a positive perception of financial performance. Financial risk largely explains the perception of the financial performance of a business which is linked to the perception of financial risk as part of everyday life. Ausloos et al. ( Citation 2018 ) argues that a reasonable company's performance assessment is required to review the need for investment in the light of a credible expected long-term increase in sales, assets and other profitability indicators. The indicators such as the respondent's ability to understand the most important aspect of financial risk and the respondent's ability to properly manage financial risk do not form financial risk. It appears that the level of financial risk is most dependent on the macroeconomic situation of the country, thus macroeconomic indicators, and to a lesser extent on managerial characteristics. It raises many questions for discussion related to the survey of managerial competencies and the personality traits of managers, or their financial literacy, etc.
Operational risk has the second most important positive effect on the perception of a positive future (PC = 0.13). Operational risk is determined by a reasonable utilisation of corporate resources, reducing customer complaints concerning the quality of products/services as well as the company not being so dependent on a limited number of suppliers. Operational risk as a factor is best explained by the reasonable utilisation of corporate resources. An interesting finding is that service/product innovation and their positive reflection on the stability (performance) of a company is not an indicator that would determine operational risk. It is because operational risk is attached to the quality of the business process management while innovation processes are attached to the company at the stage preceding the process management, e.g. at the stage of product development, investment decision-making, modernization of production and services, etc. The results of the research are also supported by Mafini and Muposhi ( Citation 2017 ) and Sinha et al. ( Citation 2011 ) studies.
Market risk is another significant factor with a positive effect on the perception of a favourable future of the company (PC = 0.12). A positive perception of capital adequacy, i.e. expected lack of sales, as well as a reasonable challenge for selling products/services determines market risk. These results are supported by the conclusions of O'Cass and Sok ( Citation 2014 ). The influence of business competitors as a driving factor for entrepreneurs and the company's ability to acquire new markets in innovative ways have not been confirmed as important determinants of market risk. The results of the research are opposite to the results of studies by Vargas-Hernández et al. ( Citation 2016 ) and De Clercq et al. ( Citation 2013 ) who argue that SMEs have low working capital in comparison with their bigger competitors and they must adopt sophisticated and effective investment, innovation and competitive strategies. Therefore, it becomes the focus to examine the extent to which and in what types of companies, with a view to their sector differentiation and size, innovative development is important as a factor of prosperity and long-term progress of a company. Innovative development is associated with the allocation of capital which may not be available to every company. In particular, SMEs have many limitations in terms of their access to or funding of innovation.
The values similar to market risk were also identified in the perception of BF (PC = 0.12). Positive attitudes of entrepreneurs toward statements: BF is a natural part of business; BF does not mean the entrepreneur’s failure; BF does not reduce self-confidence, and the correct understanding of a commitment to prevent BF has a positive effect on the entrepreneurs' perception of a positive future. BF as a factor best explains the entrepreneurs’attitudes toward the self-confidence statement. The perception of BF (bankruptcy) as a factor is not derived from the indicator: the specific BF experience of an entrepreneur. Cacciotti et al. ( Citation 2016 ) says that fear of failure may also affect business motivation but not always in a negative way. In many cases, it may involve the decision to take an even more conservative approach. In addition, there are business performance, prosperity and profit margin implications. Thus it becomes the focus to more deeply study the factors determining the managers’ risk acceptance level depending on the risk quantification and the impact on the further development of a company. Being highly conservative in the decision-making processes can lead to business stagnation, a low level of creativity in the process of the identification of the ways for business growth and ultimately, apathetic managers and hampering their motivation levels in other business activities.
Legal risk is an equally positive factor that influences the perception of future business (PC = 0.07). The positive attitude of entrepreneurs was as follows: i. the legal environment in the CR is not overregulated; ii. legal risk is considered as reasonable (without any adverse impact on business); iii. the basic legal aspect of business as a factor (legal risk) has a positive effect on the positive perception of future business. These findings are directly proportional to the study of Cepel et al. ( Citation 2018 ). It would be interesting to review these attitudes in different phases of the business cycle, e.g. in the aftermath of the economic crisis, or after a pandemic and any other globalisation threats when managers are more sensitive to the legal aspects of business and tend to exert pressure and seek legislative changes through many relevant institutions.
Personnel risk is another significant factor with a positive impact on the perception of a positive future (PC = 0.05). The positive attitudes of entrepreneurs toward the interest of employees to increase their performance and low employee turnover in the company are the indicators that measure personnel risk. Redmond and Sharafizad ( Citation 2020 ) also emphasize the interest of employees to improve their performance. Respondents' attitudes toward the employee error rate or the adequacy of personnel risk are not measured by this indicator. These factors can also be identified as traditional where changes are seldom observed. The company's performance and a low turnover rate have always been the essential parameter of business success in different types of companies and are also the cardinal indicators of measurement systems.
The positive perception of future business is also influenced by the positive attitudes of entrepreneurs toward the selected statements on strategic risk (PC = 0.02). This factor has the least impact on the perception of future business. Regular monitoring, evaluation and management of strategic risk by the company as well as the fact that the company has implemented a strategic management system are all of the indicators that measure strategic risk. Regular monitoring, evaluation and management of strategic risks by the company is better explained by strategic risk. This factor is not determined by the opinion of entrepreneurs that quality strategic management increases the company’s competitiveness. These conclusions are in direct agreement with Klammer et al. ( Citation 2017 ). Nor this factor is determined by the position that strategic management is an important part of corporate governance. This attitude of the companies under review shows a lack of perception of the importance of strategic management in the SME segment, the absence of the development of formalized strategies and their related strategic planning processes. This in turn explains why SMEs do not implement performance measurement and management systems that have been used abroad for more than two decades and are also applied by SMEs. No measurement system can be set up without vision and strategy definition, and strategic and operational goals, and without a monitoring and evaluation system in place, and this is another reason why many small companies will not survive during challenging times.
The aim of the study was to review the impact of entrepreneurs' attitudes toward the defined business risks on the perception of the future of companies in the SME sector.
The results show the identified market, financial, personnel and operational risk have a positive effect on future business of SMEs. Operational risk has the most significant positive effect on future business in the form of the utilisation of corporate resources. Other significant risks with a positive effect include financial and strategic risk. The results showed a positive effect of corporate risk management and entrepreneurs' attitudes toward the threat of business failure on the perception of future business of a company. Different types of risks and their impact on future business were also confronted with research studies to provide a discussion platform. In the crisis and post-crisis times, these comparative trajectories may lose their significance due to changes in the risk prioritization currently perceived by entrepreneurs. A financial and economic crises will significantly change the views of risk management not only within SMEs but also in large companies. Companies of all sizes are now taking a proactive approach to risk management, seeking to centralize risk management and develop integrated management systems. It is not only a national but a pan-European trend. The most common goal of risk management would be to eliminate the impact of risk on the economic result. Businesses try to eliminate the negative impact of the different types of risks on the economic result in accordance with legal requirements which was evident when the area of legal risks was reviewed. Businesses are aware of the need for better risk management in connection with the ever more challenging external business conditions in the post-crisis times, so they must pay more attention to internal controls and process changes to eliminate risk. Importantly, businesses must also identify new types of risks not previously monitored and evaluated by them. Legal risk, as well as risks involved in international trade become ever more challenging which generates pressures to set up special risk management teams, or even departments and divisions in large companies. The biggest barriers that will prevent companies from managing risks effectively in the future include the availability of information, both internal and external, required to manage and evaluate risks and integrate them into decision-making processes. The study and its results call for the creation of specific databases to support research in this field and help develop relevant policies and set up stabilisation and regulatory mechanisms for SME support and eliminate the impact of economic and epidemiological crises and disasters directly projected into the economy of countries and their further development.
The study is limited by a lower number of respondents in the research sample (454) although the total number of business entities invited to participate was quite high − 8000 SMEs in the CR. It is not the issue of data collection in a given country, or a problem stemming from the nature of research, but a clear consequence of general apathy and the burden perceived by entrepreneurs to monitor and submit any kind of data about their businesses. As a result, agencies focused on the support of the business environment and did not gather extensive and comprehensive business data which does not provide a platform for creating the necessary conceptual framework of policies for the government and other relevant institutions. The results of the study were supposed to eliminate this research gap and provide the current relevant outputs from the research of various types of risks for the future business and development of SMEs. At the same time, they highly appeal for creating dedicated SME databases to support the formation of national and international benchmarking indicators. During the covid-19 pandemic, the importance of dealing with this issue has significantly grown and provides a strategic platform in the economic policy of governments.
Future research will focus on verifying the results achieved on a new sample of SMEs in the CR, but also on the identification of disparities within the perception of the business risks on the future of enterprises between entrepreneurs the Vysehrad Group countries.
No potential conflict of interest was reported by the authors.
- Alnoor, A. (2020). Human capital dimensions and firm performance, mediating role of knowledge management. International Journal of Business Excellence , 20 ( 2 ), 149–168. doi: https://doi.org/10.1504/IJBEX.2020.105357 Google Scholar
- Audretsch, D. B., & Keilbach, M. (2005). Entrepreneurship capital and regional growth. The Annals of Regional Science , 39 ( 3 ), 457–469. doi: https://doi.org/10.1007/s00168-005-0246-9 Web of Science ® Google Scholar
- Ausloos, M., Cerqueti, R., Bartolacci, F., & Castellano, N. G. (2018). SME investment best strategies. Outliers for assessing how to optimize performance. Physica A: Statistical Mechanics and Its Applications , 509 , 754–765. https://doi.org/https://doi.org/10.1016/j.physa.2018.06.039Ff Web of Science ® Google Scholar
- Babin, B. J., Hair, J. F., & Boles, J. S. (2008). Publishing research in marketing journals using structural equations modeling. Journal of Marketing Theory and Practice , 16 ( 4 ), 279–285. doi: https://doi.org/10.2753/MTP1069-6679160401 Google Scholar
- Balan, M., Marin, S., Mitan, A., Pînzaru, F., Vătămănescu, E.-M., & Zbuchea, A. (2019). Leaders in focus: Generational differences from a personality-centric perspective. Management & Marketing. Challenges for the Knowledge Society , 14 ( 4 ), 372–385. doi: https://doi.org/10.2478/mmcks-2019-0026 Web of Science ® Google Scholar
- Balcaen, S., & Ooghe, H. (2006). 35 years of studies on business failure: An overview of the classic statistical methodologies and their related problems. British Accounting Review , 38 ( 1 ), 63–93. https://doi.org/https://doi.org/10.1016/j.bar.2005.09.001 Google Scholar
- Belas, J., Smrcka, L., Gavurova, B., & Dvorsky, J. (2018). The impact of social and economic factors in the credit risk management of sme. Technological and Economic Development of Economy , 24 ( 3 ), 1215–1230. doi: https://doi.org/10.3846/tede.2018.1968 Web of Science ® Google Scholar
- Bentler, P. M. (1990). Comparative fit indexes in structural models. Psychological Bulletin , 107 ( 2 ), 238–246. https://doi.org/https://doi.org/10.1037/0033-2909.107.2.238 PubMed Web of Science ® Google Scholar
- Bosma, N., Content, J., Sanders, M., & Stam, E. (2018). Institutions, entrepreneurship, and economic growth in Europe. Small Business Economics , 51 ( 2 ), 483–499. https://doi.org/https://doi.org/10.1007/s11187-018-0012-x Web of Science ® Google Scholar
- Brown, T. A. (2015). Confirmatory factor analysis for applied research . The Guilford Press. 2015. ISBN 978-1462-1536-3. Google Scholar
- Byrne, D. G., & Reinhart, M. I. (1989). Work characteristics, occupational achievement and the type A behaviour pattern. Journal of Occupational Psychology , 62 ( 2 ), 123–134. doi: https://doi.org/10.1111/j.2044-8325.1989.tb00483.x Web of Science ® Google Scholar
- Cacciotti, G., Hayton, J. C., Mitchell, J. R., & Giazitzoglu, A. (2016). A reconceptualization of fear of failure in entrepreneurship. Journal of Business Venturing , 31 ( 3 ), 302–325. doi: https://doi.org/10.1016/j.jbusvent.2016.02.002 Web of Science ® Google Scholar
- Caseiro, N., & Coelho, A. (2018). Business intelligence and competitiveness: The mediating role of entrepreneurial orientation. Competitiveness Review: An International Business Journal , 28 ( 2 ), 213–226. doi: https://doi.org/10.1108/cr-09-2016-0054 Web of Science ® Google Scholar
- Cepel, M., Stasiukynas, A., Kotaskova, A., & Dvorsky, J. (2018). Business environment quality index in the SME segment. Journal of Competitiveness , 10 ( 2 ), 21–40. doi: https://doi.org/10.7441/joc.2018.02.02 Web of Science ® Google Scholar
- Chłodnicka, H., & Zimon, G. (2020). Bankruptcu risk assessment measures of polish SMEs. WSEAS Transactions on Business and Economics , 17 , 14–20. https://doi.org/https://doi.org/10.37394/23207.2020.17.3 Google Scholar
- De Clercq, D., Dimov, D., & Thongpapanl, N. T. (2013). Organizational social capital, formalization, and internal knowledge sharing in entrepreneurial orientation formation. Entrepreneurship: Theory and Practice , 37 ( 3 ), 505–537. doi: https://doi.org/10.1111/etap.12021 Web of Science ® Google Scholar
- Dickson, P. H., & Weaver, K. M. (2008). The role of the institutional environment in determining firm orientations towards entrepreneurial behavior. International Entrepreneurship and Management Journal , 4 ( 4 ), 467–483. doi: https://doi.org/10.1007/s11365-008-0088-x Google Scholar
- Dincă, V. M., Dima, A. M., & Rozsa, Z. (2019). Determinants of cloud computing adoption by Romanian SMEs in the digital economy. Journal of Business Economics and Management , 20 ( 4 ), 798–798. https://doi.org/https://doi.org/10.3846/jbem.2019.985620 . Web of Science ® Google Scholar
- Dvorsky, J., Petrakova, Z., Ajaz Khan, K., Formanek, I., & Mikolas, Z. (2020). Selected aspects of strategic management in the service sector. Journal of Tourism and Services , 11 ( 20 ), 109–123. doi: https://doi.org/10.29036/jots.v11i20.146 . Web of Science ® Google Scholar
- Games, D., & Roliza, R. (2019). SME internal capability and competitive advantage in an emerging market: Moderating effects of firm age. AMAR (Andalas Management Review)) , 3 ( 1 ), 103–114. doi: https://doi.org/10.25077/amar.3.1.103-114.2019 Google Scholar
- Gede Riana, I., Suparna, G., Gusti Made, I., Kot, S., & Rajiani, I. (2020). Human resource management in promoting innovation and organizational performance. Problems and Perspectives in Management , 18 ( 1 ), 107–118. doi: https://doi.org/10.21511/ppm.18(1).2020.10 Google Scholar
- Gordon, L. A., Loeb, M. P., & Tseng, C. (2009). Enterprise risk management and firm performance: A contingency perspective. Journal of Accounting and Public Policy , 28 ( 4 ), 301–327. doi: https://doi.org/10.1016/j.jaccpubpol.2009.06.006 Web of Science ® Google Scholar
- Gorzeń-Mitka, I. (2019). Interpretive structural modeling approach to analyze the interaction among key factors of risk management process in SMEs: Polish experience. European Journal of Sustainable Development , 8 ( 1 ), 339–349. doi: https://doi.org/10.14207/ejsd.2019.v8n1p339 Web of Science ® Google Scholar
- Grimsdottir, E., & Edvardsson, I. R. (2018). Knowledge management, knowledge creation, and open innovation in icelandic SMEs. Entrepreneurship/Small Business , 8 ( 4 ), 1–13. https://doi.org/https://doi.org/10.1177/2158244018807320 Google Scholar
- Herath, H. M. A., & Mahmood, R. (2014). Strategic orientations and SME performance: Moderating effect of absorptive capacity of the firm. Asian Social Science , 10 ( 13 ), 95–107. doi: https://doi.org/10.5539/ass.v10n13p95 Google Scholar
- Habanik, J., Martosova, A., & Letkova, N. (2020). The impact of managerial decision-making on employee motivation in manufacturing companies. Journal of Competitiveness , 12 ( 2 ), 38–50. doi: https://doi.org/10.7441/joc.2020.02.03 Web of Science ® Google Scholar
- Hair, J. F., Black, W. C., Babin, B. J., & Anderson, R. E. (2010). Multivariate data analysis . Prentice Hall. Google Scholar
- Hanzaee, K. H., Ghalandari, K., & Norouzi, A. (2011). The effect of brand social power dimensions on purchasing decision based on Iranian customers' subjective readiness. World Applied Sciences Journal , 13 (5), 1197–1208. Google Scholar
- Hooper, D., Coughlan, J., & Mullen, M. R. (2008). Structural equation modelling: Guidelines for determining model fit. Electronic Journal of Business Research Methods , 6 (1), 53–60. Google Scholar
- Karabag, S. F. (2019). Factors impacting firm failure and technological development: A study of three emerging-economy firms. Journal of Business Research , 98 , 462–474. doi: https://doi.org/10.1016/j.jbusres.2018.03.008 Web of Science ® Google Scholar
- Klammer, A., Gueldenberg, S., Kraus, S., & ÓDwyer, M. (2017). To change or not to change – antecedents and outcomes of strategic renewal in SMEs. International Entrepreneurship and Management Journal , 13 ( 3 ), 739–756. doi: https://doi.org/10.1007/s11365-016-0420-9 Web of Science ® Google Scholar
- Levy, R. (2011). Bayesian data-model fit assessment for structural equation modeling. Structural Equation Modeling , 18 ( 4 ), 663–685. doi: https://doi.org/10.1080/10705511.2011.607723 Web of Science ® Google Scholar
- Lima, P. F. D., Crema, M., & Verbano, C. (2020). Risk management in SMEs: A systematic literature review and future directions. European Management Journal , 38 ( 1 ), 78–94. doi: https://doi.org/10.1016/j.emj.2019.06.005 Web of Science ® Google Scholar
- Lutz, C. H. M., Kemp, R. G. M., & Dijkstra, S. G. (2010). Perceptions regarding strategic and structural entry barriers. Small Business Economics , 35 ( 1 ), 19–33. doi: https://doi.org/10.1007/s11187-008-9159-1 Web of Science ® Google Scholar
- Mafini, C., & Muposhi, A. (2017). Predictive analytics for supply chain collaboration, risk management and financial performance in small to medium enterprises. Southern African Business Review , 21 , 311–338. Web of Science ® Google Scholar
- Malega, P., Rudy, V., Kovac, J., & Kovac, J. (2019). The competitive market map as the basis for an evaluation of the competitiveness of the Slovak Republic on an International Scale. Journal of Competitiveness , 11 ( 4 ), 113–119. doi: https://doi.org/10.7441/joc.2019.04.07 Web of Science ® Google Scholar
- Neary, B., Horak, J., Kovacova, M., & Valaskova, K. (2018). The future of work: Disruptive business practices, technology-driven economic growth, and computer-induced job displacement. Journal of Self-Governance and Management Economics , 6 ( 4 ), 19–24. https://doi.org/https://doi.org/10.22381/JSME6420183 Google Scholar
- Ngoc Mai, A., Van Vu, H., Xuan Bui, B., & Quang Tran, T. (2019). The lasting effects of innovation on firm profitability: Panel evidencefrom a transitional economy. Economic Research-Ekonomska Istraživanja , 32 ( 1 ), 3417–3430. doi: https://doi.org/10.1080/1331677X.2019.1660199 Web of Science ® Google Scholar
- O’Cass, A., & Sok, P. (2014). The role of intellectual resources, product innovation capability, reputational resources and marketing capability combinations in firm growth. International Small Business Journal: Researching Entrepreneurship , 32 ( 8 ), 996–1018. doi: https://doi.org/10.1177/0266242613480225 Web of Science ® Google Scholar
- Olah, J., Kovacs, S., Virglerova, Z., Lakner, Z., Kovacova, M., & Popp, J. (2019). Analysis and comparison of economic and financial risk sources in SMEs of the visegrad group and Serbia. Sustainability , 11 (7), 1853. Web of Science ® Google Scholar
- Psarska, M., Vochozka, M., & Machova, V. (2019). Performance management in small and medium-sized manufacturing enterprises operating in automotive in the context of future changes and challenges in SR. AD ALTA: Journal of Interdisciplinary Research , 9 (2), 281–287. Web of Science ® Google Scholar
- Redmond, J., & Sharafizad, J. (2020). Discretionary effort of regional hospitality small business employees: Impact of non-monetary work factors. International Journal of Hospitality Management , 86 , 102452. doi: https://doi.org/10.1016/j.ijhm.2020.102452 Web of Science ® Google Scholar
- Rowland, Z., Machova, V., Horak, J., & Hejda, J. (2019). Determining the market value of the enterprise using the modified method of capitalized net incomes and Metfessel allocation of input data. AD ALTA: Journal of Interdisciplinary Research , 9 (2), 305–310. Web of Science ® Google Scholar
- Santisteban, J., & Mauricio, D. (2017). Systematic literature review of critical success factors of information technology startups. Academy of Entrepreneurship Journal , 23 (2), 1–23. Google Scholar
- Shane, S., Nicolaou, N., Cherkas, L., & Spector, T. D. (2010). Do openness to experience and recognizing opportunities have the same genetic source? Human Resource Management , 49 ( 2 ), 291–303. doi: https://doi.org/10.1002/hrm.20343 Web of Science ® Google Scholar
- Sinha, P., Akoorie, M. E., Ding, Q., & Wu, Q. (2011). What motivates manufacturing SMEs to outsource offshore in China? Comparing the perspectives of SME manufacturers and their suppliers. Strategic Outsourcing: An International Journal , 4 ( 1 ), 67–88. doi: https://doi.org/10.1108/17538291111108435 Google Scholar
- Ślusarczyk, B., & Grondys, K. (2019). Parametric conditions of high financial risk in the SME Sector. Risks , 7 ( 84 ), 1–17. doi: https://doi.org/10.3390/risks7030084 Google Scholar
- Smith, R. M., Schumacker, R. E., & Bush, M. J. (1998). Using item mean squares to evaluate fit to the Rasch model. Journal of Outcome Measurement , 2 (1), 66–78. PubMed Google Scholar
- Stenholm, P., Acs, Z. J., & Wuebker, R. (2013). Exploring country-level institutional arrangements on the rate and type of entrepreneurial activity. Journal of Business Venturing , 28 ( 1 ), 176–193. doi: https://doi.org/10.1016/j.jbusvent.2011.11.002 Web of Science ® Google Scholar
- Süsi, V., &Lukason, O. (2019). Corporate governance and failure risk: evidence from Estonian SME population. Management Research Review , 42 ( 6 ), 703–720. doi: https://doi.org/10.1108/MRR-03-2018-0105 Web of Science ® Google Scholar
- Svarova, M., & Vrchota, J. (2013). Strategic management in micro, small and medium-sized businesses in relation to financial success of the enterprise. Acta Universitatis Agriculturae et Silviculturae Mendelianae Brunensis , 61 ( 7 ), 2859–2866. doi: https://doi.org/10.11118/actaun201361072859 Google Scholar
- Trif, S.-M., Duțu, C., & Tuleu, D.-L. (2019). Linking CRM capabilities to business performance: A comparison within markets and between products. Management & Marketing. Challenges for the Knowledge Society , 14 ( 3 ), 292–303. doi: https://doi.org/10.2478/mmcks-2019-0021 . Web of Science ® Google Scholar
- Ucbasaran, D., Shepherd, D. A., Lockett, A., & Lyon, S. J. (2013). Life after business failure: The process and consequences of business failure for entrepreneurs. Journal of Management , 39 ( 1 ), 163–202. doi: https://doi.org/10.1177/0149206312457823 Web of Science ® Google Scholar
- Vargas-Hernández, J. G., Casas Cardenaz, R., & Calderón Campos, P. (2016). Internal control and organizational culture in small businesses: A conjunction to competitiveness. Journal of Organisational Studies and Innovation , 3 (2), 16–30. Web of Science ® Google Scholar
- Vochozka, M., Psarska, M. (2016). Factors supporting growth of added value, performance and competitiveness of SMEs and selected EU countries. In Proceedings of the Innovation Management Entrepreneurship and Corporate Sustainability (pp. 756–767). Google Scholar
- Wang, Y. (2016). What are the biggest obstacles to growth of SMEs in developing countries? – An empirical evidence from an enterprise survey. Borsa Istanbul Review , 16 ( 3 ), 167–176. doi: https://doi.org/10.1016/j.bir.2016.06.001 Web of Science ® Google Scholar
- Wegner, D., Zarpelon, F. M., Verschoore, J. R., & Balestrin, A. (2017). Management practices of small-firm networks and the performance of member firms. Business: Theory and Practice , 18 ( 0 ), 197–207. doi: https://doi.org/10.3846/btp.2017.021 Google Scholar
- Wheaton, B., Muthén, B., Alwin, D. F., & Summers, G. F. (1977). Assessing reliability and stability in panel models. In D. R. Heise (Ed.), Soxciological methodology 1977 (pp. 84–136). Jossey-Bass. https://doi.org/https://doi.org/10.2307/270754 [] Google Scholar
- Yang, J. S. (2017). The governance environment and innovative SMEs. Small Business Economics , 48 ( 3 ), 525–541. https://doi.org/https://doi.org/10.1007/s11187-016-9802-1 Web of Science ® Google Scholar
- Zhao, H., & Seibert, S. E. (2006). The big five personality dimensions and entrepreneurial status: A meta-analytical review. The Journal of Applied Psychology , 91 ( 2 ), 259–271. https://doi.org/https://doi.org/10.1037/0021-9010.91.2.259 PubMed Web of Science ® Google Scholar
- Back to Top
Related research
People also read lists articles that other readers of this article have read.
Recommended articles lists articles that we recommend and is powered by our AI driven recommendation engine.
Cited by lists all citing articles based on Crossref citations. Articles with the Crossref icon will open in a new tab.
- People also read
- Recommended articles
To cite this article:
Download citation, your download is now in progress and you may close this window.
- Choose new content alerts to be informed about new research of interest to you
- Easy remote access to your institution's subscriptions on any device, from any location
- Save your searches and schedule alerts to send you new results
- Export your search results into a .csv file to support your research
Login or register to access this feature
Register now or learn more
Risk Management and Its Types Essay
- To find inspiration for your paper and overcome writer’s block
- As a source of information (ensure proper referencing)
- As a template for you assignment
Introduction
Operational risks, social risk, works cited.
Risk management refers to the process of identifying, assessing, and prioritizing risks, as well as consequent application of measures to monitor, minimize, and control their effects (Frame 53).
Risks emanate from several occurrences such as financial uncertainties, project failures, legal liabilities, credit difficulties, accidents, and other unpredictable events. Risk management standards apply avoidance of risks by organizations.
Methods, goals, and definitions of risk standards depend on field of application. Types of risks include social risks, operational risks, financial risks, credit risks, currency risks, quantitative risks, market risks, and project risks (Frenkel and Rudolf 26).
Types of risk management differ based on an organization’s goals, objectives, and operations. Risk management plays a vital role in promoting organizational growth and success.
Operational risks refer to risks encountered by organizations owing loses experienced from execution of internal activities. Operational risk management focuses on mitigating risks incurred due to operations executed by organizational systems and people.
Operational risks include fraud, physical risks, and legal risks (Hutter and Power 33). Basel II regulations define operational risk as probability of an organization’s exposure to failures in operations, systems, or people due to certain events external to an organization (Frenkel and Rudolf 36).
The difference between operational risk management and other types of risk management is that operational risk management does not earn profits for organizations. Organizations are aware that people, systems, and organizational processes are prone to errors that expose them to losses.
The degree of losses that an organization is willing and ready to handle determines its ability to manage operational risk (Hutter and Power 34).
Types of operational risks include employee errors, system failures, fraud, criminal activity, and natural disasters such as floods and fire (Hutter and Power 35).
Internal processes such as employee training, staff development, media communication, stakeholder management, and product or service development are common sources of operational risks (Hopkin 31).
Other examples include employment practices, execution and process management, workplace safety, and business practices (Khatta 34). Operational risk arises from failures or weaknesses in these processes (Frenkel and Rudolf 29).
For example, if employee training does not give desired results or stakeholder management does not meet goals and objectives, operational risks arise.
Attributes of operational risks include emotional effects, financial loses, increased costs, reduced productivity, reduced effectiveness and efficiency, and poor results.
Social risk refers to risks encountered due to factors such as age, gender, religion, culture, and race (Khatta 39). Social risk management refers to a framework that focuses on preventing people from effects of social risks by presenting protective and coping strategies.
According to research, poor people are the most vulnerable to effects of social risks (Hopkin 44). Several classes of factors expose individuals to social risks.
Examples include health, life cycle, economic situation, environmental aspects, as well as administrative and political factors (Khatta 42). Health risks expose individuals to injuries, disabilities, and illnesses.
In extreme cases, people are exposed to pandemics that have severe effects. Life cycle is associated with birth, age, and death. Economic situation determines availability of employment opportunities to individuals.
Discrimination is one of the risks experienced under administrative and political factors. Discrimination leads to politically induced malpractices such as denial of social privileges such as human rights and freedom (Schutt 82). Discrimination is also associated with religion and race.
Attributes of social risks include lack of cohesion in communities, racial and social segregation, religious intolerance, and division of people into socio-economic groups (Khatta 53).
Gender is another common aspect of social risk. Researchers from the University of Amsterdam and Columbia Business School found out that women take fewer risks than men (Hopkin 54).
In comparison, women perceive risks to be higher in the financial and ethical areas but lower in the social arena. Women take more social risks than men, while men take more financial risks than women.
Social risks that women take include advancing careers at advanced ages and giving their opinions regarding religion or gender equality at meetings and in public (Hopkin 55). Men and women behave differently when faced with social risks.
This difference in behavior is attributed to varying perception of social risk (Schutt 89). Each gender perceives risk as less or more risky depending on length of exposure.
Risk refers to probability that a certain activity will lead to a certain loss. On the other hand, risk management refers to the process of identifying, assessing, and prioritizing risks, as well as consequent application of measures to monitor, minimize, and control effects.
Risks emanate from several occurrences such as financial uncertainties, failure of projects, legal liabilities, credit difficulties, accidents, and other unpredictable events. Two common types of risks include social risk and operational risk.
Operational risk is associated with risks encountered by organizations owing to execution of internal activities.
It focuses on risks incurred due to operations executed by organizational systems and people. Social risk refers to risk associated with religion, gender, race, place of origin, age, and socioeconomic class.
Frame, James. Managing Risk in Organizations: A Guide for Managers . New York: John Wiley & Sons, 2009. Print.
Frenkel, Michael, and Rudolf Markus. Risk Management: Challenge and Opportunity . New Opportunity: Springer, 2007. Print.
Hutter, Bridget, and Power Michael. Organizational encounters with Risk . London: Cambridge University Press, 2005. Print.
Hopkin, Paul. Fundamentals of Risk Management: Understanding, Evaluating, and Implementing Effective Risk Management . New York: Kogan page Publisher, 2012. Print.
Khatta, Robert. Risk Management . New York: Global India Publications, 2001. Print.
Schutt, Harold. Risk Management: Concepts and Guidance . New York: DIANE Publishing, 2003. Print.
- Risk Management in the Events Industry
- Risk Management in Construction Projects
- The Secrets to Successful Strategy Execution
- Birmingham Revival - Project Execution Plan
- Source of Operational Risk to Banks
- Risk Management in Project Management
- Agricultural Greenhouses: Risk Assessment and Management
- Risk Identification, Assessment, and Handling
- Risks Identification and Management
- Company X Risk Management
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2019, July 5). Risk Management and Its Types. https://ivypanda.com/essays/risk-management-5/
"Risk Management and Its Types." IvyPanda , 5 July 2019, ivypanda.com/essays/risk-management-5/.
IvyPanda . (2019) 'Risk Management and Its Types'. 5 July.
IvyPanda . 2019. "Risk Management and Its Types." July 5, 2019. https://ivypanda.com/essays/risk-management-5/.
1. IvyPanda . "Risk Management and Its Types." July 5, 2019. https://ivypanda.com/essays/risk-management-5/.
Bibliography
IvyPanda . "Risk Management and Its Types." July 5, 2019. https://ivypanda.com/essays/risk-management-5/.
IvyPanda uses cookies and similar technologies to enhance your experience, enabling functionalities such as:
- Basic site functions
- Ensuring secure, safe transactions
- Secure account login
- Remembering account, browser, and regional preferences
- Remembering privacy and security settings
- Analyzing site traffic and usage
- Personalized search, content, and recommendations
- Displaying relevant, targeted ads on and off IvyPanda
Please refer to IvyPanda's Cookies Policy and Privacy Policy for detailed information.
Certain technologies we use are essential for critical functions such as security and site integrity, account authentication, security and privacy preferences, internal site usage and maintenance data, and ensuring the site operates correctly for browsing and transactions.
Cookies and similar technologies are used to enhance your experience by:
- Remembering general and regional preferences
- Personalizing content, search, recommendations, and offers
Some functions, such as personalized recommendations, account preferences, or localization, may not work correctly without these technologies. For more details, please refer to IvyPanda's Cookies Policy .
To enable personalized advertising (such as interest-based ads), we may share your data with our marketing and advertising partners using cookies and other technologies. These partners may have their own information collected about you. Turning off the personalized advertising setting won't stop you from seeing IvyPanda ads, but it may make the ads you see less relevant or more repetitive.
Personalized advertising may be considered a "sale" or "sharing" of the information under California and other state privacy laws, and you may have the right to opt out. Turning off personalized advertising allows you to exercise your right to opt out. Learn more in IvyPanda's Cookies Policy and Privacy Policy .
Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
- Explore content
- About the journal
- Publish with us
- Sign up for alerts
- Open access
- Published: 27 September 2024
Advancing the complex adaptive systems approach to enterprise risk management with quantified risk networks (QRNs)
- Ananya Sheth ORCID: orcid.org/0000-0003-4910-0857 1 &
- Joseph V. Sinfield ORCID: orcid.org/0000-0002-4472-6669 2
Scientific Reports volume 14 , Article number: 22312 ( 2024 ) Cite this article
Metrics details
- Socioeconomic scenarios
- Sustainability
Business enterprises are complex adaptive systems (CAS) subject to fragility caused by the non-linear effects of uncertain risk events. The regional bank collapses in the United States are a case in point. Recent papers have highlighted a shortcoming of the traditional risk management process, which focuses on compliance but considers neither the interdependence between complex risks nor the mechanism of their non-linear impact on the organization. A new perspective on Enterprise Risk Management (ERM) has instead called for a shift of mindset from mitigating risk to building resilience by honing a CAS view to contextualize, assess, and manage complex risks. But the building blocks needed for a CAS representation of ERM have not yet been systematically developed. Specifically, we are missing a typological inventory of risks and a mapping of risks onto the general structure of an enterprise. In this paper, we build an industry-agnostic inventory of plausible risk factors using information extraction on large scale text data. Additionally, we develop an understanding of risk-function and function-function interdependencies through a survey of top business managers. The result is a novel complex network view of enterprise risk called a Quantified Risk Network (QRN) that displays small-world properties and highlights internal company functions central to non-linear risk propagation mechanisms within the enterprise. The QRN draws attention to vulnerabilities in the enterprise structure such as risk-function connections measured by Edge Betweenness centrality. The generic QRN developed herein is a proof of concept and we advocate that enterprises build their own company-specific QRNs to identify highly connected and central functions in their company structure that could lead to cascading failure when specific risks arise. QRNs can contribute to the objective of building enterprise resilience.
Similar content being viewed by others
Identifying risks in temporal supernetworks: an IO-SuperPageRank algorithm
Heuristic assessment of choices for risk network control
Measuring system resilience through a comparison of information- and flow-based network analyses
Introduction.
The research discipline of management and organizational theory was originally based in a mechanistic paradigm 1 , 2 , emphasizing principles of operational structure and accountability under generally direct assumptions of cause and effect. However, companies are sociotechnical systems that display all the characteristic attributes of a complex system 3 such as interconnectedness 4 ; adaptation 5 , 6 ; nonlinearity, fragility and resilience 7 , 8 ; emergence 9 ; self-organization 10 ; and uncertainty 11 . Over time, several fields within management have adopted the Complex Adaptive Systems (CAS) lens 12 , 13 , 14 , 15 , 16 55 , but the field of risk management remains compliance-oriented and simplistic 17 , 18 .
A complex system view is relevant to risk management because the non-linear and uncertain impact of adverse events on companies is clearly observed in prominent events that have occurred within the last decade. Geopolitical conflicts, bank collapses, the pandemic, prolonged material and component shortages, supply chain blockages, and the global financial crises have all demonstrated the havoc that unexpected external events can wreak on companies, and this has reinforced the need for companies to build resilience through improved risk intelligence 19 .
There is growing recognition that risks are complex by nature, and recent calls to account for complexity in risk management emphasize interdependence between risks 20 , 21 , 22 , 23 , 24 . Most recent literature considers risk–risk interaction networks but does not consider risk-function or function-function interaction networks 25 . In other words, risk management theory recognizes one source of complexity (emerging from interacting risks) but falls short of recognizing the other (emerging from an enterprise’s organizational structure). Both are needed to make sense of how risks could propagate non-linearly across the enterprise 26 .
In this paper, we introduce Quantified Risk Networks (QRNs) as a view of a CAS enterprise subject to risks. QRNs connect external risks to the structure of the enterprise, thereby enabling us to visualize and investigate how the impact of external risks might propagate across the enterprise system. QRNs reflect pertinent risks for a company and highlight central functions of the enterprise, which have high risk exposure and through which impact can propagate. Therefore, QRNs advance the field of risk management from simplistic estimation of risk occurrence and impact towards a CAS view where firms can contextualize complex external risks 27 , estimate the typical responses of its internal structure, and understand the thresholds beyond which the system could change states. This brings to forth the concept of resilience from CAS theory that is highly relevant to risk management research 26 . In the next section we describe the enterprise CAS and highlight the gap in the risk management literature.
The enterprise CAS
An enterprise can be viewed as a CAS operating within a larger CAS, which we refer to as its business environment or operating context 28 . To contain our research at the company level of analysis, we draw a boundary between the CAS enterprise (alternatively referred to as the company or the organization) and the operating context. Practically, this boundary is the domain of the focal company, i.e., the point beyond which the company has no direct control, although factors beyond the boundary may still, and often do, have a direct impact on the company. External factors collectively form the operating context and can be grouped under themes such as market dynamics, competition, regulatory environments, technological trends, economic conditions, and societal influences, which interact and create feedback, presenting both opportunities and challenges for the company. In this paper, we focus only on the challenges, which the literature generally refers to as risks.
Unexpected events occur in the company’s operating context subjecting it to multilayered risks 29 . They may arise individually or in tandem to impact the company’s normal functioning 30 . In this regard, resilience is the ability of the enterprise system to persist by maintaining essential functions and to evolve by incorporating change when confronted with unpredictable and unexpected events 27 . The company’s risk management function evaluates the operating context and responds. Managers monitor, identify, and assess risks, and contextualizing them is important for shaping tactical and strategic decisions under uncertainty 27 . This falls under the remit of enterprise risk management (ERM) 31 , making it crucial to building resilience and to the company's long-term success.
A CAS view of ERM
The literature on managing uncertainty in organizations dates to the seminal work of Frank Knight 32 , who defined uncertainty based on ‘knowledge’ and broadly divided it into the knowable and unknowable. Knowable situations lead to a probabilistic view, where known probabilities of occurrence and their impact quantify the ‘risk’ to the company. In contrast, uncertainty includes those factors and situations that are epistemically difficult or impossible to know, i.e., unknowable unknows. Hence, from the Knightian perspective, quantifying uncertainty requires converting the unknown situations or factors into a tangible quantification of risk for the company 33 .
Risk management theory is grounded in the Knightian perspective and has evolved from a compliance-driven estimation and mitigation of risks to Enterprise Risk Management (ERM)—a more holistic approach to managing any risk that can potentially inhibit the enterprise from achieving its strategic objectives 34 . Thus, ERM blurs the boundary between uncertainty and risk. In doing so, ERM moves risk management scholarship from simple linear cause and effect towards a complex system view.
The International Organization for Standardization (ISO) published ISO 31000:2009, a framework for ERM, which although progressive in comparison to earlier frameworks, is simultaneously criticized for offering limited guidance on the challenge of identifying and contextualizing complex risks 27 . An amended framework issued in 2017 35 connects ERM with strategy by anchoring it to the context of a corporation’s performance 23 , 36 , but the ERM process still involves converting uncertainty into risk by estimating occurrence probabilities and determining impact. Note that ERM recognizes two sources of uncertainty- unexpected events and unexpected impact, and the ERM process suggests quantifying them into risk 37 .
However, when ERM is viewed as a CAS, complexity theory tells us that uncertainty and thus unpredictability is a consequence of the behavior of the system in which risk factors originate 21 . Therefore, knowing a priori how risks will emerge and how the enterprise CAS will respond to emerging risks requires understanding the ERM system and its states. Papers that call for the adoption of the CAS view on ERM recognize that risks are complex in nature, i.e., they form from feedback loops without pre-determined manifestation patterns. They correctly suggest that complexity theory can help us better understand limits of system states and changes in system states if unexpected events were to take place 37 . In other words, by adopting the tools of complexity theory, risk managers can identify those factors that destabilize the system and better understand the points at which the system becomes unstable and/or changes states. This is a novel approach to ERM when compared to simply estimating the probabilities of occurrence of individual risks 20 , 23 . However, proponents of the complexity view emphasize much less the estimation of the impact that complex risks will have on the enterprise, given that the functions of the enterprise are themselves interconnected and interdependent. In this sense, the literature does not consider the role of the enterprise’s organizational structure in contributing to the non-linear behavior of the enterprise CAS 38 , 39 . CAS theory indicates that singular or simultaneous events manifesting in the company’s business environment will likely have a non-linear impact on the company, which could in turn lead to cascading consequences. In practice, the company’s risk managers, who have agency to make tactical and strategic decisions, would be expected to respond to curb the non-linear negative impact.
The CAS view on risk management is important because it can highlight the points and mechanisms of fragility for the company, and this is particularly critical for interdependent risks. Schiller and Prpich 38 , for example, emphasize that “Whereas independent risks generally follow Gaussian distributions, interdependent risks represent Paretian distributions, which represent extreme system behaviours or black swan events. ERM guidance has not yet accounted for these alternations in risk character.” Although the CAS view on ERM suggests non-linear impact of risks on the organization—and scholars have suggested that “the correlations between risks in different parts of an enterprise must be recognized, accounted for, and appropriately managed” 34 , there remains a gap in research towards understanding the mechanism of non-linearity and its measurement. We hypothesize that advancing the CAS view thus requires internal focus on the enterprise structure as dependencies between various enterprise functions propagate the negative impact of manifesting external risks. In this paper, we seek to understand and quantify how non-linearity is formed and propagated within the enterprise.
For CAS theory to be adopted into ERM practice, the field needs foundational elements (a comprehensive organized inventory of external risks and a generic enterprise structure with functional interdependencies, in light of the risks) to identify risks and assess their non-linear impact on an interconnected organization 17 . In this paper we address both gaps by building the foundational elements and demonstrating a process to identify risks, risk-function and function-function interactions. We analyze the functions of a generic enterprise that are more (or less) central and the risk-function edges, which connect dense clusters in the enterprise. Following principles of network theory, we hypothesize that business functions that are more central to the enterprise in the context of risk events are more likely to lead to the non-linear impacts that organizations experience when risk events manifest. Below we explain our representation of the risk management function as a CAS.
Representing ERM as a CAS
A CAS involves interacting components / agents that learn and adapt 40 . Thus, the two building blocks of a CAS are components and the interactions between them, which give rise to emergence as the dynamics of a CAS proceeds 41 . Network analysis is one of the methods to analyze CAS where components and interactions are represented as the nodes and links of the network, respectively. Then, in a CAS view of ERM, groups of risks and business functions (nodes) interact in interdependent ways to produce enterprise-wide effects, which can demonstrate cascading behavior across the CAS. All CAS share four major features: parallelism, conditional action, modularity, and adaptation and evolution 42 . Table 1 describes each of them and translates the described behaviors into the context of ERM, and thereby helps us translate the conceptual features of a CAS into the CAS view of ERM. However, from a practical standpoint defining the ERM as a CAS requires identification of the nodes of the ERM function and their interdependencies.
For the ERM CAS, nodes are the external risk factors occurring in the business environment as well as the various business functions such as finance, operations, strategic management, and product development that depend on one another for generating value in the enterprise. External factors variably impact business functions. For instance, a supply chain blockage will influence the manufacturing and distribution operations, which may also influence the company finances / cash flow 38 . An inventory of external risks is needed to understand the external-internal interface. Most current studies that look at risk interdependencies rely on a handful and/or idiosyncratic set of risks 25 , 43 . In the methods section we describe how we built an inventory of risks and identified the risk-function and function-function interdependencies. Performing this process provides us with a general structure of a CAS organization and a first of its kind inventory of risk factors linked to it that is ready for complex network analyses.
Methodology
A goal of this effort was to develop a comprehensive inventory of risk factors. Currently, company risk factor data is distributed across public and private sources and available in an unstructured form. A major public source of risk data is annual reports. The Securities & Exchange Commission (SEC) mandates firms listed on US stock exchanges to provide risk disclosure in the Sections 1A and 7 of form 10-k filed annually. This data source has been used in studies on risk management 44 , 45 , 46 , 47 , 48 , 49 , 50 . We collected annual reports of roughly 15 years (up to year-2020) for companies listed in the S&P 500. In addition, we used a commercial data platform to access private analyst reports for the same companies, and gathered related information from the SCOPUS academic database.
Risk Extraction
The next step was to process the large volume of unstructured data to identify and organize risk factors into a typology. Risk factors in 10-k reports contain descriptive sentences, which may explicitly mention specific risk factors (e.g., currency risk, supply chain risk) or may implicitly provide risk information (e.g., “stoppages in material supply may cause a hindrance to our business objective”). We built a program leveraging natural language processing methods sequentially to extract relevant risk related information from sentences. We first extracted risk information content by tokenizing sentences into bi- and tri-grams and sought out syntactical patterns such as “ Noun -risk” and “ Noun - Noun -risk” 51 . This helped extract terms such as “ currency risk” and “ supply chain risk” while avoiding phrases such as “is risky”. The program used regular expressions 52 to flexibly cover variations of words (e.g., risky). This provided us several explicitly stated risk factors. Second, we used the topic modeling technique to extract factors implicit in text sentences. The Sentence Latent Dirichlet Allocation (Sent LDA) is a popular topic modeling approach to infer risks as topics from sentences 53 , 54 . See the two referenced papers for the detailed Sent LDA algorithm. Lastly, we used the extracted factors as seed inputs into the SCOPUS database and further identified related risk factors provided as ‘author given keywords’ in the papers returned by the search. Not all author keywords were risk factors and required manual filtering. Overall, we extracted ~ 800 + risk factors, which is significantly larger than most published risk databases. The risk extraction process in pseudocode is as follows:
For each firm \(f\in \left\{S\&P 500\right\}\) , build a corpus \(C\) of text data on risk factors to firms
Query the SEC Edgar database for 10-k reports
Query the Refinitiv Eikon platform for commercial analyst reports
Use a bag-of-words approach to build the vocabulary
For each document in \(C\) ,
Tokenize sentences into bi-grams and tri-grams
Using spaCy and syntactic logic, extract risk factors and add to the inventory
Identify latent topics in the corpus using SentLDA
For each topic \(k\in \left\{1,\dots ,K\right\}\) , draw a distribution over the vocabulary \({\beta }_{k}\sim Dirichlet\left(\eta \right)\)
For each document \(\mathcal{d}\) ,
Draw a vector of topic proportions \({\theta }_{d}\sim Dirichlet\left(\alpha \right)\)
For each sentence \(s\) in document \(\mathcal{d}\) ,
Draw a topic assignment \({z}_{d,s}\sim Multinomial\left({\theta }_{d}\right)\)
For each word \({w}_{d,s,n}\) in a sentence \(s\) ,
Draw a word \({w}_{d,s,n}\sim Multinomial({{\beta }_{z}}_{d,s})\)
where \({\beta }_{k}\) denotes the V-dimensional word distribution for the topic \(k\) derived by tokenizing the 10-k document; \({\theta }_{d}\) denotes the K-dimensional risk factor vector; and \(\eta\) and \(\alpha\) denote the hyperparameters of Dirichlet distributions.
Manually review identified latent topics and add to the risk inventory
Expand the risk inventory using the SCOPUS database
Query SCOPUS and perform a combinatorial search of extracted risk inventory words
For each paper in the returned set of papers
Isolate the ‘author given keywords’ JSON object
Manually review and add to the risk inventory
Figure 1 provides a schematic process view of our complete methodology.

Process steps leading to the risk inventory.
Organizing risk factors into a risk typology
Our objective was to link external risk factors to internal enterprise structure. For this, we organized the above inventory of risk factors into a typology. We used a top-level organizing structure described in existing literature on value-based strategy to link risk types to a generic organization represented as a system of value exchange. The value-based view in strategic management emphasizes the creation and enhancement of shareholder value as the primary objective of a company’s strategic decisions and actions. Thus, the activities performed by all companies fulfill a shared set of functions that can be linked back to value. The eight value functions include ‘manage value’, ‘identify value’, ‘convey value’, ‘create value’, ‘deliver value’, ‘capture value’, ‘protect value’, ‘sustain value’ 55 (See the referenced paper for a detailed description). This structure forms the basis of our contribution, which is to determine how business function interdependence leads to cascading impact of external risks.
A manual thematic analysis process was adopted to build a 5-level typology, where level 5 risk factors are clustered based on similarity, which are a type-of level 4 risk, which in-turn are a type-of level 3 risk group. Risk groups are linked to an enterprise’s generic functions at level 2, and functions are linked to one of eight value functions at level 1. Figures 2 and 3 show this organized typology of risks to any company.

The risk inventory expanded along a single ‘operational capability’ branch.

Overview of risk-factor inventory. The background figure is a zoomed-out view of the full typology organized under the 5-level value structure with the 800 + risk factor inventory identified through text analysis on the perimeter. The box shows a zoomed-in view of level 5 risk factors for one branch of the typology related to geopolitical uncertainties.
Network development and network analysis
With the risk inventory mined and typology developed, our next step was to build the function-function and risk-function interlinks. For this we developed a survey, which was administered to 65 managers in large companies with different functional expertise. Subjects were selected based on designation. The preset criteria was to invite only middle-management level and higher. The distribution of responses by designation and company size is shown in Fig. 7 . Subjects were recruited leveraging personal networks of the authors as well as through the Purdue University alumni network. A snowball sampling method was used by requesting experts who agreed to participate to forward the survey to colleagues in their networks who they deemed appropriate based on the criteria. The survey is provided in the attached supplementary materials, where a live link to the survey is also available.
Each subject matter expert quantified on a 0–100% slider scale how the business function of their expertise impacted other business functions within the organization. Further, each expert was asked to rate the level of impact caused by sets of risks on the business function/s of their expertise. This was kept as a fuzzy quantification exercise using ‘high impact’, ‘medium impact’, and ‘low impact’ ratings to provide ease of use and incentivize survey completion. With these two ratings, we were able to develop a generalized CAS network for analysis. Previous studies in ERM have used similar survey techniques to build risk networks 56 , 57 , 58 , 59 . Figure 4 highlights the processes to develop the QRN as they relate to the creation and structure of the risk inventory. The QRN in Fig. 5 represents a general complex network to capture the impact of external risks on a CAS enterprise. The descriptive statistics in Table 2 below summarize the QRN and describe its structure.
Relationship between risk inventory structure and QRN development process. On the left are 5 levels of the risk typology organized in a value-based frame and expanded along a different branch of the typology. On the right are the process steps leading to QRNs.

Last, we applied network topology measures to analyze the QRN 61 , 62 . Though network analysis-based approaches have been adopted in risk management 43 , 58 , 59 , they have largely focused on creating risk interdependencies and estimating impact. This is a point of departure for the approach adopted herein, which builds the complex enterprise network structure and focuses on understanding the impact of risks, given a complex network topology. Measures from Network Theory are used including node degree and edge betweenness centrality. Node outdegree is the number of edges directed out from a node in the network, and we use it to quantify how many other functions each enterprise function impacts. In network analysis, ‘Betweenness’ is a centrality measure, i.e., how central a node is to the network, or said differently, how much is the network dependent on a node for propagation 63 . It is typically measured as the count of the paths between node pairs in a network that pass through a given node. Thus, nodes with high betweenness lie on paths between many others and will likely have some influence over the spread (of risk impact) across the network 64 , 65 . We use a specific centrality measure called Edge Betweenness Centrality (EBC). The EBC of any connected edge \(e\) is defined as the number of shortest paths between a node pair \(\left(s,t\right)\) that go through \(e\) divided by the total number of shortest paths that go from \(s\) to \(t\) . Like betweenness centrality in nodes, EBC provides an intuition for edges that lie on central paths in a complex network. Edges with high EBC therefore connect dense sub-networks and help identify community structures in networks 66 . This is important as the impact of risks in contained sub-networks could propagate through an edge with high EBC.
The methodology outlined above resulted in two major outputs: a structured inventory (typology) of 800 + risks, and a Quantified Risk Network (QRN), which is a weighted graph linking categories of identified potential risks to the functional structure (the system within managers’ control). A description of the results and a discussion follows.
The structured inventory is a novel resource and likely the largest organized database of risks to companies. Figure 2 illustrates a single branch of the risk along the value creation node. Given the wide breadth of coverage it is an obvious challenge to show all 800 + risk factors in a clear and concise manner. As an alternative, the background Fig. 3 captures the entire 5-level typology with the 800 + risk factors on the perimeter and the zoomed-in box illustrates inventory risks belonging to the geopolitical uncertainties category. Visit 28 to access the risk factor tables.
For clarity, the QRN is separated into Fig. 5 a and b. Figure 5 a indicates the complexity added by function-function interconnections. The larger orange nodes represent functions impacting the highest number of other functions. For example, Business strategy impacts 17 other functions whereas Market risk assessment impacts 10 other functions. They both impact the Competitive intelligence function similarly, but Business strategy has greater impact on the Marketing & sales function as compared to Market risk assessment (shown by the dark and light gray edges). An enterprise function when subject to external risks, will carry over the impact of the risk to connected functions, especially when it cannot contain the impact. This is a path or mechanism for risk propagation across functions.
Figure 5 b shows three views of a weighted network connecting (57) level 4 risk categories to the (18) enterprise functions. Figure 5b1 captures all risk-function edges, whereas Figs. 5b2 and b3 show risk-function edges filtered by high and low risk impact indicated by experts, respectively. As expected, several high impact risks affect the most central nodes of the enterprise structure (top functions in the left column) with thick risk-function edges. These are top risks that should be continuously monitored. For instance, value chain stability risk causes high impacts on at least five functions and has high EBC edges. Further, the more central business functions are exposed to a broader and more diverse range of external risk factors. Even though several risks are marked as low-impact by experts (in Fig. 5b2), the thick edges indicate that there can be high EBC risk-function edges, albeit with risks considered to cause low impact on the enterprise. For example, corporate architecture risk has a seemingly low impact on sourcing. Yet that link is central to the network and can lead to a percolation or cascading impact across the enterprise if the function is unprepared or has a low threshold to manage the risk 67 . Comparing Figs. 5b2 and 5b3, we should also note that the same categories of risk can impact different enterprise functions differently, thereby further reinforcing the necessity for cross-function communication among risk managers as has been called for by previous studies. The networks in Figs. 5 a and 5b collectively give us a QRN, which managers can use to identify complex network effects as demonstrated above in addition to relying on consensus on what risks and functions should be monitored. This way they can uncover any missed risks or at least develop a shared language and perspective on risk factors to their enterprise that should be reviewed.
Figure 6 is a histogram plot of the EBC scores for risk-function edges. The EBC scores in our QRN are skewed towards lower EBC scores. There are some outlying edges with significantly high EBC scores. Table 3 lists the top 10 risk-function edges with highest betweenness centrality scores, bringing to light those specific risk-function pairs that are highly central to the QRN. They should be monitored as those edges connect dense parts of the QRN.

Histogram of risk-function edge betweenness centrality scores. The top 10 EBC score edges all lie on the right tail of the histogram.
Lastly, the basic topology of the generic QRN developed herein points to features relevant to ERM. Watts and Strogatz 60 empirically show that for similar values of characteristic path length (which measures the degree of separation in the network) and clustering coefficients (which are a measure of the cliquishness of the network) as found in our QRN (see Table 2 ), the network structure tends to be a small-world network. We suspect that enterprise risk networks in general and company-specific QRNs should also show a small-world network structure because by adding company-specific risk-function and function-function links, the clustering coefficient would further increase. Small-world networks have specific properties such as a hub-spoke structure and greater efficiency of flow in the network, which in the case of risk impact is a negative feature (Fig. 7 ).

Count of survey respondents by designation and company size.
QRNs form the basis for such complex network analyses. Having a QRN creates a mechanism for managing risks by connecting decontextualized risk knowledge to a company’s specific structure to interpret related impacts on its functions at a level that affects decision-makers. It shows the level of impact a risk category has on a business function and illustrates how firms can isolate and identify key functions that link densely connected risks and are therefore particularly significant to risk management.
Implications of a CAS view for ERM practice
A CAS view has been called for in ERM research. The CAS view looks at the holistic system and considers a broad spectrum of risks that could directly impact specific industries. For example, level 4 of the risk typology contains risk categories such as ‘geopolitical risks’, ‘product portfolio risks’, and ‘supply chain and operations risks’, which directly impact energy companies, companies engaged in developing physical and digital products, and companies engaged in manufacturing, respectively.
Further, the system view enables firms to look at beyond-industry risks, i.e., those risks that a company is exposed to indirectly and could affect it in reality but may not be considered major risks in its industry. Sheth and Sinfield 19 illustrate cyber security risk impact to the shipping industry. Sheth and Kusiak 16 illustrate this for manufacturing logistics, and Sheth 28 illustrates this in the food processing industry.
Three primary components serve at the core of ERM: risk identification, assessment, and risk mitigation. But the systems view in ERM suggests that these process steps need to be embedded in the enterprise’s context such that the monitoring of risks is systematic and not random 27 . The CAS approach is made complete by the development of a robust risk inventory and a company-specific QRN that enhance the ERM process.
Identification
A significant challenge for ERM is identifying weak signals within a company’s operating context 23 , 68 . The risk inventory developed herein is a novel resource for risk managers as it helps identify a large collection of plausible risks that may occur outside the company boundary in the company's operating context. Although not a full set, its broad coverage drawing on a large historic database allows for minimal periodic evaluation to keep it up to date. This is especially so because risks remain largely the same over time indicating that completely new risks are few and instead risk events occur with already known risks manifesting in new ways such as combinations of risks 28 . Thus, as managers monitor external threats, they have an enhanced ability to consider a broader set of risk factors and check across categories of risks for plausible interactions.
Having a structured typology is foundational to creating a system view because it connects a missing component of earlier ERM frameworks – the contextualization of risks to the enterprise and related system feedback 27 . This helps sense-making and assessment of the impact of risks on the company. The typology is a bridge between risks external to the company and the organization of company functions.
The function-function links developed through expert input clarify how the organization’s activities are interconnected. This is a typical unknown in organizations and a source of uncertainty for the CAS. Similarly, function-risk links reduce the other traditional and significant source of uncertainty, i.e., how unexpected events affect functions. A quantification of function-function linkages and a fuzzy evaluation of risk-function linkages (high, medium, or low impact of risks on a function) enables easy practical application. Even without perfect quantification, companies can garner value from QRNs as they reveal dense clusters of related functions and points of fragility in the company. QRNs help leaders better understand their company’s vulnerability to risk events by illuminating those functions that are central to the value exchange system.
Moreover, QRNs reveal counter-intuitive insights, such as a function’s indirect exposure to risks typically associated with a different but connected function. These links within the company structure are the reason for the non-linearity of impact during external unexpected events as they enable the propagation or cascade of impact through the CAS. For example, the QRN reveals that ‘reputation’ and ‘sales execution’ risks have a high impact relationship with the ‘marketing and sales’ function. In turn, the ‘marketing and sales’ function is strongly linked to the densely clustered ‘financial capital management’ function. Hence, both reputation and sales execution risks are 1 hop risks that the financial management function should monitor even though they are not directly linked. Overall, applying network analysis methods over QRNs helps explore the threshold limits of the enterprise system and can be used to explore failure modes in CAS enterprises 69 .
Developing a function driven and sector agnostic QRN offers a stepping off point for any organization to frame and develop its own QRN. Building a company specific QRN (following a similar procedure to that outlined above, but with entity-specific tailoring) enables planning for an adverse operating context, thereby advancing the risk management function. In addition, the process of developing company specific QRNs allows top managers across large organizations to clarify the differences in opinion on the significance of risk factors and on the potential impacts those could have on their company, which helps break down functional silos (which have plagued earlier ERM approaches). Thus, QRNs provide a shared language of risk management across CAS organizations.
Because the QRN is developed over a standard structure of business functions, this common basis provides opportunities for managers to learn from other organizations that share similar ways of fulfilling functions. This broadening of scope is novel because typically companies draw learnings from other companies operating in the same industry or sector. In addition, maintaining a watchful eye on companies outside of one’s sector that share ways of fulfilling business functions offers the potential to provide early awareness of weak signals not yet noticed in-sector.
Lastly, although the focus of this effort is on the challenges caused by external risks, honing an awareness of the precise location and mechanism of impact of manifesting challenges motivates the identification and pursuit of new opportunity because opportunities are often the inverse of challenges. Understanding the challenges clearly helps overcome them through more probable paths and can lead to opportunity capture.
Overall, the CAS view of organizations leads to advancement in traditional risk management of organizations that are operating in an increasingly interconnected and uncertain environment. Table 4 summarizes this comparison.
Limitations and Opportunities for Future Work
Using S&P 500 firms implied that the risk inventory would only contain risks impacting relatively large companies, only the risks faced by industries represented in S&P 500, and only those risks that were disclosed by them at least once. However, we took steps to partially overcome the bias induced by our choice. For instance, purchasing access to private analyst reports allowed us to identify additional risks undisclosed in public reports but mentioned in the investment analyses. Additionally, we used the identified risk factors as seed input into the SCOPUS academic database to run a second pass in identification. SCOPUS is one of the largest abstract indexing platforms and provides ‘author given keywords’ in each listed paper. As shown in Fig. 1 , the iterative mining process discovered additional related risks indicated as keywords in academic papers related to the particular risk.
In terms of the coverage of the S&P 500, it comprehensively represents all economic sectors even though it does not have as much granularity at sub-industry level. This is a shortcoming, and in the future, the data source can be expanded to include a larger set of companies such as the Russell 3000 list, on which the extraction and expansion process can be applied.
The stated limitations highlight several opportunities for future research. First, the data processing methods employed herein did not use transformers or large language models, which future research can include to validate and improve our typology. Second, evaluation of the risk-function and function-function linkages highlighted in this work could further benefit from the perspectives of additional expert evaluators given the broad scope and complexity of the developed comprehensive risk inventory. Further, numerous opportunities exist to draw on the underlying structure of the sector agnostic QRN provided here to examine specific industries and companies and thus further validate and/or refine it for application across contexts. Furthermore, by simulating the network growth dynamic over time, we can potentially predict the cascading behavior in small-world networks by studying the degree distribution and the betweenness distribution 70 . The simulation is not performed here because we do not have data on the threshold levels / impact absorption capacity of the enterprise functions. But collecting this data in a company-specific QRN building exercise will make it a promising path for future research on cascading failures and for the sensing of weak-signals indicative of cascading failure.
A specific takeaway of earlier ERM frameworks is that “risk management cannot be done in functional silos within an enterprise but instead must be a coordinated effort across organizational lines.” 34 In this paper, we advance the CAS-view of ERM by providing a method for firms to enhance their risk monitoring as well as better contextualize identified risks, across organizational silos, by building QRNs. The paper has developed a generic QRN, which while not specifically focused on a company or industry, offers a) a robust starting point for risk identification, b) a complete sector-agnostic organizing structure for company functions, and c) demonstrates the steps to develop a company specific QRN. It is a proof of concept that analyzing QRNs yields valuable insight regarding the points of weakness in the enterprise risk network. The approach taken to build and analyze QRNs brings ERM closer to complex network analysis, which is called for by the ERM research community but not yet performed. Ultimately, it has merits over current simplistic approaches because it highlights the plausible mechanisms of impact cascades.
Data availability
The datasets used and/or analyzed during the current study are available from the corresponding author on reasonable request.
Bohórquez Arévalo, L. E. & Espinosa, A. Theoretical approaches to managing complexity in organizations: A comparative analysis. Estudios Gerenciales https://doi.org/10.1016/j.estger.2014.10.001 (2015).
Article Google Scholar
Turnbull, S. A New Way to Govern. SSRN Electron. J. https://doi.org/10.2139/ssrn.310263 (2002).
Anderson, P. Perspective: Complexity theory and organization science. Organ. Sci. 10 , 216–232 (1999).
Chandra, Y. & Wilkinson, I. F. Firm internationalization from a network-centric complex-systems perspective. J. World Bus. 52 , 691–701 (2017).
Teece, D. J. Dynamic Capabilities and Strategic Management: Organizing for Innovation and Growth . (2009).
Pathak, S. D., Day, J. M., Nair, A., Sawaya, W. J. & Kristal, M. M. Complexity and adaptivity in supply networks: Building supply network theory using a complex adaptive systems perspective*. Decis. Sci. 38 , 547–580 (2007).
Zhang, Y. & Yang, N. Vulnerability analysis of interdependent R&D networks under risk cascading propagation. Physica A 505 , 1056–1068 (2018).
Article ADS Google Scholar
Taleb, N. N. Antifragile: Things That Gain from Disorder . (2012).
Stacey, R. D. The science of complexity: An alternative perspective for strategic change processes. Strateg. Manag. J. 16 , 477–495 (1995).
Sheth, A. & Sinfield, J. V. Simulating Self-Organization during Strategic Change: Implications for Organizational Design. (2019).
Townsend, D. M., Hunt, R. A., McMullen, J. S. & Sarasvathy, S. D. Uncertainty, knowledge problems, and entrepreneurial action. Acad. Manag. Ann. 12 , 659–687 (2018).
Puranam, P., Alexy, O. & Reitzig, M. What’s “new” about new forms of organizing?. Acad. Manag. Rev. 39 , 162–180 (2014).
Baumann, O. Models of complex adaptive systems in strategy and organization research. Mind Soc. 14 , 169–183 (2015).
Novak, D. C., Wu, Z. & Dooley, K. J. Whose resilience matters? Addressing issues of scale in supply chain resilience. J. Bus. Logist. https://doi.org/10.1111/jbl.12270 (2021).
Choi, T. Y., Dooley, K. J. & Rungtusanatham, M. Supply networks and complex adaptive systems: Control versus emergence. J. Oper. Manag. https://doi.org/10.1016/S0272-6963(00)00068-1 (2001).
Sheth, A. & Kusiak, A. Resiliency of smart manufacturing enterprises via information integration. J. Ind. Inf. Integr. https://doi.org/10.1016/j.jii.2022.100370 (2022).
Sachs, R. & Wadé, M. Emerging Risk Discussion Paper: Managing Complex Risks Successfully . https://www.researchgate.net/publication/267370113 (2013) https://doi.org/10.13140/2.1.2128.8961 .
Kassymkanova, G. Insurance Professionals’ Use of Best Practices for Enterprise Risk Management . (2023).
Sheth, A. & Sinfield, J. V. Risk Intelligence and the Resilient Company. MIT Sloan Manag Rev 64 , (2023).
Johnson, J. Can complexity help us better understand risk?. Risk Manag. 8 , 227–267 (2006).
Smith, D. & Irwin, A. Complexity, risk and emergence: Elements of a “management” dilemma. Risk Manag. 8 , 221–226 (2006).
McKelvey, B. & Andriani, P. Avoiding extreme risk before it occurs: A complexity science approach to incubation. Risk Manag. 12 , 54–82 (2010).
Emblemsvåg, J. Risk and complexity – on complex risk management. J. Risk Financ. 21 , 37–54 (2020).
Andringa, L., Ökmen, Ö., Leijten, M., Bosch-Rekveldt, M. & Bakker, H. Incorporating project complexities in risk assessment: Case of an airport expansion construction project. J. Manag. Eng. https://doi.org/10.1061/(ASCE)ME.1943-5479.0001099 (2022).
Sasaki, H., Fujii, M., Sakaji, H. & Masuyama, S. Enhancing Risk identification with GNN: Edge classification in risk causality from securities reports. Int. J. Inf. Manag. Data Insights 4 , 100217 (2024).
Google Scholar
van der Vegt, G. S., Essens, P., Wahlström, M. & George, G. Managing risk and resilience. Acad. Manag. J. 58 , 971–980 (2015).
Haywood, L. K., Forsyth, G. G., de Lange, W. J. & Trotter, D. H. Contextualising risk within enterprise risk management through the application of systems thinking. Environ Syst Decis 37 , 230–240 (2017).
Sheth, A. B. Pathways to Enterprise Resilience. (Purdue University, 2021). https://doi.org/10.25394/PGS.15062880.v1 .
Ibrahim, S. E., Centeno, M. A., Patterson, T. S. & Callahan, P. W. Resilience in global value chains: A systemic risk approach. Global Perspect. https://doi.org/10.1525/gp.2021.27658 (2021).
Mark, S., Holder, S., Hoyer, D., Schoonover, R. & Aldrich, D. P. Understanding polycrisis: Definitions, applications, and responses. SSRN Electr. J. https://doi.org/10.2139/ssrn.4593383 (2024).
Bromiley, P., McShane, M., Nair, A. & Rustambekov, E. Enterprise risk management: Review, critique, and research directions. Long Range Plann 48 , 265–276 (2015).
Knight, F. H. Risk, uncertainty and profit (Hart, Schaffner and Marx, 1921).
Marshall, A., Ojiako, U., Wang, V., Lin, F. & Chipulu, M. Forecasting unknown-unknowns by boosting the risk radar within the risk intelligent organisation. Int. J. Forecast 35 , 644–658 (2019).
Nason, R. Risk management and complexity. in It’s not complicated: the art and science of complexity in business 165–191 (2017).
Committee of Sponsoring Organizations of the Treadway Commission (COSO). COSO Enterprise Risk Management – Integrating with Strategy and Performance . (2017).
Viscelli, T. R., Hermanson, D. R. & Beasley, M. S. The integration of ERM and strategy: Implications for corporate governance. Account. Horiz. 31 , 69–82 (2017).
Johansen, I. L. & Rausand, M. Defining complexity for risk assessment of sociotechnical systems: A conceptual framework. Proc. Inst. Mech. Eng. O J. Risk Reliab. 228 , 272–290 (2014).
Schiller, F. & Prpich, G. Learning to organise risk management in organisations: What future for enterprise risk management?. J. Risk Res. 17 , 999–1017 (2014).
Yang, L., Lou, J. & Zhao, X. Risk response of complex projects: Risk association network method. J. Manag. Eng. https://doi.org/10.1061/(ASCE)ME.1943-5479.0000916 (2021).
Holland, J. H. Complex adaptive systems. Daedalus 121 , 17–30 (1992).
Holland, J. H. Complex adaptive systems and spontaneous emergence. Contributions to Economics 25–34 (2002) https://doi.org/10.1007/978-3-642-50007-7_3 .
Holland, J. H. Studying complex adaptive systems. J. Syst. Sci. Complex 19 , 1–8 (2006).
Article MathSciNet Google Scholar
Bashir, H. et al. A weighted fuzzy social network analysis-based approach for modeling and analyzing relationships among risk factors affecting project delays. EMJ – Eng. Manag. J. 36 , 3–13 (2024).
Fujii, M., Sakaji, H., Masuyama, S. & Sasaki, H. Extraction and classification of risk-related sentences from securities reports. Int. J. Inf. Manag. Data Insights 2 , 100096 (2022).
Loughran, T. & McDonald, B. When Is a liability not a liability? textual analysis, dictionaries, and 10-Ks. J Finance 66 , 35–65 (2011).
Felipe Costa Spreb, L., Roussou, F., Marshall, A. & Mues, C. RISK RADAR : A METHODOLOGY TO CATEGORISE RISKS DISCLOSED ON SEC 10-K REPORTS . (2019).
Bode, C., Wagner, S. M., Zurich, E. & Kemmerling, R. Internal versus External Supply Chain Risks: A Risk Disclosure Analysis. In Supply Chain Safety Management – Security and Robustness in Logistics (eds Eßig, M. et al. ) 109–122 (Springer, Berlin, 2013).
Chapter Google Scholar
Mirakur, Y. Risk Disclosure in SEC Corporate Filings . https://repository.upenn.edu/wharton_research_scholars/85/ (2011).
Bao, Y. & Datta, A. Simultaneously discovering and quantifying risk types from textual risk disclosures. Manage Sci 60 , 1371–1391 (2014).
Beatty, A., Cheng, L. & Zhang, H. Are risk factor disclosures still relevant? evidence from market reactions to risk factor disclosures before and after the financial crisis. Contemporary Account. Res. 36 , 805–838 (2019).
Sheth, A. & Sinfield, J. V. Systematic problem-specification in innovation science using language. Int. J. Innov. Sci. 13 , 314 (2021).
Mitkov, R. The Oxford Handbook of Computational Linguistics 2nd edn. (Oxford University Press, Oxford, 2014).
Book Google Scholar
Zhu, X., Yang, S. Y. & Moazeni, S. Firm risk identification through topic analysis of textual financial disclosures. in 2016 IEEE Symposium Series on Computational Intelligence, SSCI 2016 (Institute of Electrical and Electronics Engineers Inc., 2017). https://doi.org/10.1109/SSCI.2016.7850005 .
Wang, Y., Li, B., Li, G., Zhu, X. & Li, J. Risk factors identification and evolution analysis from textual risk disclosures for insurance industry. Procedia Comput. Sci. 162 , 25–32 (2019).
Liu, J., Tong, T. W. & Sinfield, J. V. Toward a resilient complex adaptive system view of business models. Long Range Plann. 54 , 102030 (2021).
Marle, F. & Vidal, L. A. Project risk management processes: Improving coordination using a clustering approach. Res. Eng. Des. 22 , 189–206 (2011).
Fang, C. & Marle, F. A framework for the modeling and management of project risks and risk interactions In Handbook on Project Management and Scheduling 1105–1117 (Springer International Publishing, 2015).
Fang, C., Marle, F., Zio, E. & Bocquet, J. C. Network theory-based analysis of risk interactions in large engineering projects. Reliab. Eng. Syst. Saf. 106 , 1–10 (2012).
Fang, C., Marle, F. & Xie, M. Applying importance measures to risk analysis in engineering project using a risk network model. IEEE Syst. J. 11 , 1548–1556 (2017).
Watts, D. J. & Strogatz, S. H. Collective dynamics of ‘small-world’ networks. Nature 393 , 440–442 (1998).
Article ADS CAS PubMed Google Scholar
Freeman, L. C. Centrality in social networks conceptual clarification. Soc. Netw. 1 , 215–239 (1978).
Brandes, U., Borgatti, S. P. & Freeman, L. C. Maintaining the duality of closeness and betweenness centrality. Soc. Netw. 44 , 153–159 (2016).
Vespignani, A. Predicting the behavior of techno-social systems. Science 1979 (325), 425–428 (2009).
Article ADS MathSciNet Google Scholar
Newman, M. Networks (Oxford University Press, Oxford, 2018).
Newman, M., Barabási, A. & Watts, D. The Structure and Dynamics of Networks (Princeton University Press, Princeton, 2006).
Newman, M. E. J. & Girvan, M. Finding and evaluating community structure in networks. Phys. Rev. E 69 , 026113 (2004).
Article ADS CAS Google Scholar
Piraveenan, M., Prokopenko, M. & Hossain, L. Percolation centrality: Quantifying graph-theoretic impact of nodes during percolation in networks. PLoS One 8 , e53095 (2013).
Article ADS CAS PubMed PubMed Central Google Scholar
Shankar, R. K., Bettenmann, D. & Giones, F. Building hyper-awareness: how to amplify weak external signals for improved strategic agility. Calif. Manag. Rev. 65 , 43–62 (2023).
Pournajar, M., Zaiser, M. & Moretti, P. Edge betweenness centrality as a failure predictor in network models of structurally disordered materials. Sci. Rep. 12 , 11814 (2022).
Xia, Y., Fan, J. & Hill, D. Cascading failure in Watts-Strogatz small-world networks. Physica A 389 , 1281–1285 (2010).
Download references
Acknowledgements
This research was supported by the National Science Foundation under Grant Number 2049782.
Author information
Authors and affiliations.
Orfalea College of Business, California Polytechnic State University, San Luis Obispo, CA, USA
Ananya Sheth
Institute for Innovation Science, College of Engineering, Purdue University, West Lafayette, IN, USA
Joseph V. Sinfield
You can also search for this author in PubMed Google Scholar
Contributions
Ananya Sheth : Conceptualization; Funding acquisition; Methodology; Formal analysis; Visualization; Writing—original draft, review & editing. Joseph V. Sinfield : Conceptualization; Funding acquisition; Methodology; Project administration; Supervision; Writing—review & editing.
Corresponding author
Correspondence to Ananya Sheth .
Ethics declarations
Competing interests.
The authors have no competing interests as defined by Nature Research, or other interests that might be perceived to influence the results and/or discussion reported in this paper.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary Information
Supplementary information., rights and permissions.
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/ .
Reprints and permissions
About this article
Cite this article.
Sheth, A., Sinfield, J.V. Advancing the complex adaptive systems approach to enterprise risk management with quantified risk networks (QRNs). Sci Rep 14 , 22312 (2024). https://doi.org/10.1038/s41598-024-71764-x
Download citation
Received : 15 April 2024
Accepted : 30 August 2024
Published : 27 September 2024
DOI : https://doi.org/10.1038/s41598-024-71764-x
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
By submitting a comment you agree to abide by our Terms and Community Guidelines . If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
Sign up for the Nature Briefing newsletter — what matters in science, free to your inbox daily.
- SUGGESTED TOPICS
- The Magazine
- Newsletters
- Managing Yourself
- Managing Teams
- Work-life Balance
- The Big Idea
- Data & Visuals
- Case Selections
- HBR Learning
- Topic Feeds
- Account Settings
- Email Preferences
Risk management
- Change management
- Competitive strategy
- Corporate strategy
- Customer strategy
The Power of “Risktakes”
- Vineet Nayar
- August 18, 2010

What Do You Do When Employees Start Using a Free Cloud Service?
- Robert Plant
- September 18, 2015
Bringing the Environment Down to Earth
- Forest L. Reinhardt
- From the July–August 1999 Issue

The Board's New Innovation Imperative
- Linda A. Hill
- George Davis
- From the November–December 2017 Issue

The Hidden Dangers of Playing It Safe
- Doug Sundheim
- October 22, 2013
Living in a Radical State of Uncertainty
- Bruce Nussbaum
- March 23, 2011

Too Many Experts Can Hurt Your Innovation Projects
- Riitta Katila
- December 07, 2017
Leaning Your Way to Disaster
- Michael D. Watkins
- May 06, 2010
Strategy as Active Waiting
- Donald N. Sull
- September 01, 2005

Life's Work: An Interview with Alex Honnold
- Alex Honnold
- Eben Harrell
- From the May–June 2021 Issue
Making Real Options Really Work
- Alexander B. Van Putten
- Ian C. MacMillan
- From the December 2004 Issue
When Crowds Aren’t Wise
- Cass R. Sunstein
- From the September 2006 Issue

Preparing for Evil (HBR OnPoint Enhanced Edition)
- Ian I. Mitroff
- Murat C. Alpaslan
- April 01, 2003
Is Holacracy for Us? (HBR Case Study)
- Erik Roelofsen
- March 01, 2017

How Pharma Can Fix Its Reputation and Its Business at the Same Time
- Damiano de Felice
- February 03, 2017

What Organizations Need to Survive a Pandemic
- Nitin Nohria
- January 30, 2020

Have Your Privacy Policies Kept Up with Your Digital Transformation?
- Cillian Kieran
- June 29, 2020

4 Areas of Cyber Risk That Boards Need to Address
- Sander Zeijlemaker
- Chris Hetner
- Michael Siegel
- June 02, 2023
Why the Yale Model of Investing Doesn’t Work for Everybody
- April 09, 2010
The Next Volcano: Will Your Company Be Ready?
- Andrew Winston
- April 20, 2010

The End of the Chevron Doctrine Is Bad for Business
- Larry Downes
- Blair Levin
- September 13, 2024

Boards Need a New Approach to Technology
- Tarun Khanna
- Mary C. Beckerle
- Nabil Y. Sakkab
- From the September–October 2024 Issue

3 Common Archetypes of Employees Who Commit Fraud
- Kelly Richmond Pope
- Vairam Arunachalam
- August 15, 2024

When Cyberattacks Are Inevitable, Focus on Cyber Resilience
- Keri Pearlson
- July 18, 2024

How to Assess True Macroeconomic Risk
- Philipp Carlsson-Szlezak
- Paul Swartz
- From the July–August 2024 Issue

4 Types of Gen AI Risk and How to Mitigate Them
- Lazaros Goutas
- May 31, 2024

Make Decisions with a VC Mindset
- Ilya A. Strebulaev
- From the May–June 2024 Issue

Why Playing It Safe Is the Riskiest Strategic Choice
- Steve Dennis
- March 28, 2024

Bring Human Values to AI
- Jacob Abernethy
- François Candelon
- Theodoros Evgeniou
- Abhishek Gupta
- Yves Lostanlen
- From the March–April 2024 Issue

Why Data Breaches Spiked in 2023
- Stuart Madnick
- February 19, 2024

How to Vet a Corporate Intelligence Vendor
- Maria Robson-Morrow
- Katherine Tucker
- Paul R. Kolbe
- January 19, 2024

4 Questions to Assess the Trustworthiness of Your Company’s GenAI
- Shalene Gupta
- January 18, 2024

How to Red Team a Gen AI Model
- Andrew Burt
- January 04, 2024

2023: A Strange, Tumultuous Year in Sustainability
- December 28, 2023

Your Company Will Need Remote Work as Extreme Weather Gets Worse
- Erik Brynjolfsson
- Sebastian Steffen
- November 15, 2023

How to Capitalize on Generative AI
- Andrew McAfee
- Daniel Rock
- From the November–December 2023 Issue

What's Your Gen AI Strategy?
- Paul Leonardi
- Iavor Bojinov
- November 01, 2023

Smaller Companies Must Embrace Risk Management
- Ariane Chapelle
- September 08, 2023
Generative AI-nxiety
- Reid Blackman
- August 14, 2023

How a Federal Ban on Ransomware Payments Could Help CISOs
- Gary Barlet
- August 04, 2023

Hermitage's Russian Quandary (B)
- Eric Werker
- Raymond Fisman
- Lauren Weber
- April 25, 2011
Ça Va de Soi: A Phoenix Rises from the Ashes of a Failed IT Project - Part A - The Fall
- Simon Bourdeau
- Dragos Vieru
- Amelie Bernier
- September 01, 2016
Nikkei 225 Reconstitution
- Robin Greenwood
- March 15, 2007
23andMe: Genetic Testing for Consumers (B)
- John A. Quelch
- Margaret Rodriguez
- January 26, 2014
Theranos: Who Has Blood on Their Hands? (A)
- Nien-he Hsieh
- Christina R. Wing
- Emilie Fournier
- Anna Resman
- February 06, 2019
National Storage Affiliates: The REIT IPO Decision
- Charles F Wu
- Max de la Bruyere
- Gregory Himmel
- August 02, 2018
Protecting Foreign Investors
- Louis T. Wells Jr.
- March 30, 2006
Freemark Abbey Winery (Abridged)
- William S. Krasker
- July 19, 2005
Decision Analysis
- Barbara B. Jackson
- August 01, 1974
ALPES S.A.: A Joint Venture Proposal (A)
- Henry W. Lane
- Dennis Shaughnessy
- David T.A. Wesley
- February 07, 2006
Dow Corning Corp.: Business Conduct and Global Values (C)
- Kenneth E. Goodpaster
- David E. Whiteside
- May 05, 1989
Societe Generale (B): The Jerome Kerviel Affair
- Francois Brochet
- October 02, 2009
UnME Jeans: Branding in Web 2.0
- Thomas Steenburgh
- November 12, 2008
Phipps Houses and the Future of Affordable Housing in NYC
- V. Kasturi Rangan
- Lisa A. Chase
- October 17, 2016
Production Processes
- Garrett van Ryzin
- August 17, 2010
ATH Technologies: Making the Numbers
- Robert Simons
- Jennifer Packard
- May 18, 2017
Nodal Logistics and Custo Brasil
- Michael Moffett
- November 15, 2008
Mine Resistant Ambush Protected (MRAP) Vehicle
- Thomas Cross
- January 21, 2009
Prime Coalition: Estimating Climate Impact
- Natalia Rigol
- Benjamin N. Roth
- Brian Trelstad
- Amram Migdal
- October 31, 2023
Jet Propulsion Laboratory
- Robert S. Kaplan
- Anette Mikes
- February 18, 2010

A Better Recovery
- July 01, 2024

The Limits of Models
Popular topics, partner center.

IMAGES
VIDEO
COMMENTS
Conclusion of risk management analysis. Risk management is an important process that managers should maintain in an organization. It is inevitable to have risks and managers should have better strategies to deal with risks. The long-term survival of an organization depends on the ability to manage risks.
Risk management is a strategy or methodology used to identify, assess and counter risks in a process. The risk management strategy can be for any industry or task but is primarily for preserving company capital and finance. The hazards assessed in these strategies include disasters, financial volatility, industry downfall, etc.
4 Reasons Why Risk Management Is Important. 1. Protects Organization's Reputation. In many cases, effective risk management proactively protects your organization from incidents that can affect its reputation. "Franchise risk is a concern for all businesses," Simons says in Strategy Execution. "However, it's especially pressing for ...
The Importance of Risk Management. Risk management, a critical facet of modern business and decision-making, is the process of identifying, assessing, and mitigating potential threats and uncertainties that could affect an organization's objectives. From financial institutions to healthcare providers and even individuals, understanding and ...
An essay on risk management might cover strategies to mitigate risks, the impact of risk management on business performance, and the evolution of risk management practices over time. This topic might also touch on various risk assessment models, the ethical aspects of risk management, and case studies illustrating the consequences of inadequate ...
Business essay sample: The paper will carry out financial statements and operating indicator analysis to assess the financial condition of the two Health care facilities. Apple Company: Audit Risk Analysis Project. Business essay sample: Apple Inc. was incorporated by Steve Wozniak and Steve Jobs in 1977.
The purpose of. the paper is to perform a literature review of the empirical evidence on ERM and to propose futur e. research directions. In line with Tranfield et al.2003) and Prasad et al.2018 ...
Meriton Suites: The Risk Management. The business's name is Meriton Suites, and it is located in Australia, with the headquarters in Sydney; the business type is privately held. Pages: 6. Words: 2210. We will write a custom essay specifically for you.
A risk management essay might consider the most common sources of risks, like financial uncertainties, management errors, natural disasters, etc. One can also look at risk management strategies for various industries. A step further would be to compare these strategies and their possible outcomes.
A risk management process model is a cyclic framework that develops a continuous strategy for addressing risks in a business. The process starts by defining the function and the risk in question (Mayo, 1991). All the possible mechanisms are then developed to address the risk (s) that have been identified.
This collection of essays deals with the situated management of risk in a wide variety of organizational settings—aviation, mental health, railway project management, energy, toy manufacture, financial services, chemicals regulation, and NGOs. Each chapter connects the analysis of risk studies with critical themes in organization studies more ...
So, you check the weather forecast before planning. This is a simple example of risk management. In the same way, businesses also use risk management. They want to know about any problems that might happen. This way, they can make plans to avoid them or reduce their impact. Steps in Risk Management. Risk Management includes four main steps: 1.
This holistic approach to managing risk is sometimes described as enterprise risk management because of its emphasis on anticipating and understanding risk across an organization. In addition to a focus on internal and external risk threats, enterprise risk management (ERM) emphasizes the importance of managing positive risk. Positive risks are opportunities that could increase business value ...
Risk management is the forecasting or evaluation of possible risks and identifying the process to avoid or overcome it. It utilizes the right methods and tools to handle the threat. With a risk management plan, you can always be prepared in advance and let the business not be affected by it. Here are a few reasons why risk management is ...
In business, risks are factors that an organization encounters that may lower its profits or cause it to fail. Sources of risk can be external, such as changes in what consumers want, changes in ...
Risk Management―The Revealing Hand. by Robert S. Kaplan and Anette Mikes. This article explores the role, organization, and limitations of risk identification and risk management, especially in situations that are not amenable to quantitative risk modeling. It argues that firms can avoid the artificial choice between quantitative and ...
In this context, strategic risk management or SRM is defined as a process of determining, evaluating, and addressing risks that are directly associated with the company's strategy and can lead to the business or strategic failure (Tonello par. 3). Therefore, the manager's task is to identify possible risks, assess their impact on the ...
Risk Working Papers. McKinsey's Risk Working Papers present McKinsey's best current thinking on risk and risk management. They represent a broad range of views, both sector specific and cross-cutting, and are intended to encourage discussion internally and externally.
Enterprise Risk Management (ERM) is a method that is used for determining uncertainties and opportunities that influence the accomplishment of business goals. It involves the identification of internal and external factors that lead to the success or failure of the business. This essay provides an insight into enterprise risk management as a ...
Review. 1. Introduction. The concept of risk and risk assessments has a long history. More than 2400 years ago the Athenians offered their capacity of assessing risk before making decisions (Bernstein, 1996). However, risk assessment and risk management as a scientific field is young, not more than 30-40 years old.
The diagnostics of risk sources in SMEs is the most important phase of risk management because preventive actions can only be devised to eliminate the identified risk (Gorzeń-Mitka, Citation 2019). The adverse consequences of the absence of business risk management threaten the very existence of a company (Balcaen & Ooghe, Citation 2006). This ...
Risk management standards apply avoidance of risks by organizations. Methods, goals, and definitions of risk standards depend on field of application. Types of risks include social risks, operational risks, financial risks, credit risks, currency risks, quantitative risks, market risks, and project risks (Frenkel and Rudolf 26).
Business enterprises are complex adaptive systems (CAS) subject to fragility caused by the non-linear effects of uncertain risk events. The regional bank collapses in the United States are a case ...
Management Digital Article. Andrew McAfee. Daniel Rock. Erik Brynjolfsson. Paul Leonardi. Iavor Bojinov. Artificial intelligence is arguably one of our generation's most transformative ...